Encrypted Traffic Analysis Uncovering Hidden Threats
With over 90% of today’s internet traffic cloaked in encryption, cyber attackers are exploiting this trend to conceal their own activities. Progress® Flowmon® helps detect hidden threats within encrypted traffic and provides robust security without the need for decryption.
Launch demo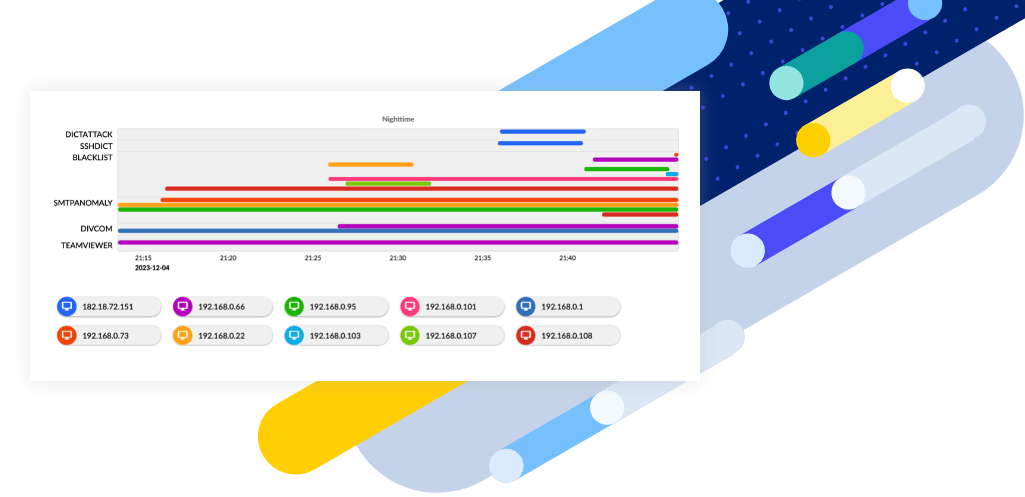
Detection and Compliance and Response

Detection Beyond Traditional Means
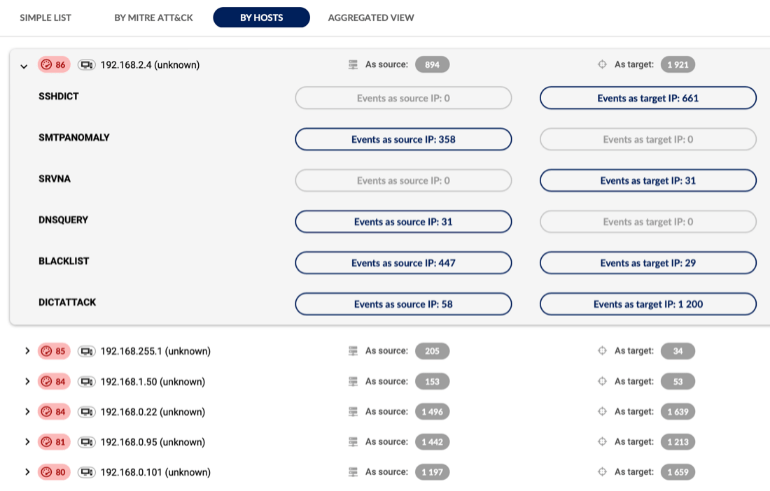
Employ AI and threat intelligence to uncover additional threat footprints in encrypted traffic that conventional methods may miss.

Observability Without Decryption
Get greater insights into encrypted data flows for proactive monitoring and maintain greater data integrity and confidentiality.

Boosting Security Compliance
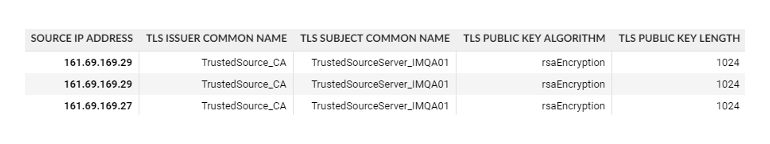
Benefit from rich intelligence of devices’ security posture, including cryptographic assessment and use of legacy protocols.

Automating Incident Response
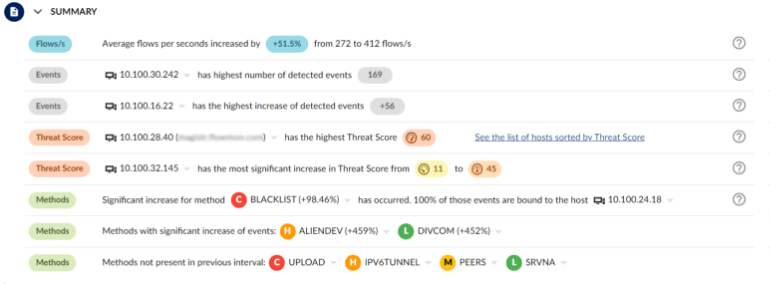
Minimize the need for manual intervention, reducing response time and limiting the potential damage caused by the attack on a non-compliant device.
Encrypted Traffic Analysis When Decryption Is Impossible
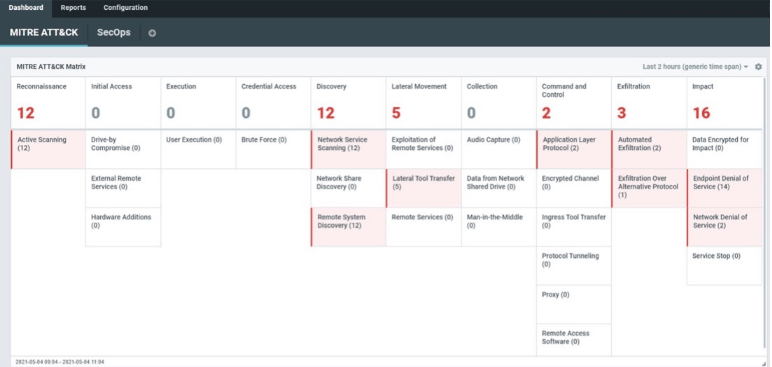
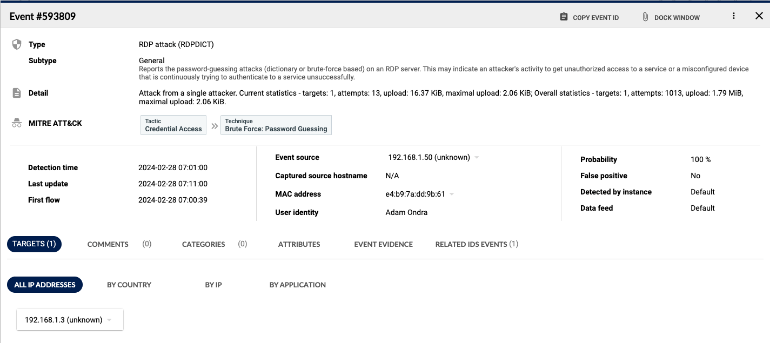
Encrypted traffic analysis detects malware and assesses cryptographic security when decryption is not an option, enhancing visibility into encrypted traffic without compromising scalability, latency or privacy. As malware increasingly hides in encrypted traffic, detecting malicious TLS activities is vital for compliance and protection. Flowmon passively collects network data, uses AI for threat detection and provides intelligent insights for cryptographic policy assessments in hybrid environments.
Expose Attacks Before It Is Too Late
Improve your cybersecurity resilience with Flowmon’s powerful features.