Detection of Insider Threats
Uncover suspicious behaviors. Get insight. Act immediately. Insider threats range from oversights by users to social engineering attacks or sophisticated infiltrations with compromised credentials. Flowmon’s security intelligence recognizes indicators of compromise on the network level, where breaches can be tracked at their every stage, provides immediate insights and alerting, as well as data for a thorough post-compromise analysis.
Launch demoWhat is an insider threat
An insider threat is an intentional or unintentional misuse of access rights that poses a risk of sensitive data breach, or endangers the integrity or availability of critical business assets. Insider threats do not come from employees only, basically everyone with the privilege of using an organization's network can be a source of threat (contractors, business partners, former employees etc.).
How to detect an insider threat
The diversity of insider threats is reflected in the complexity of protection against them. It requires a layered security approach that stacks multiple points of view together to provide a holistic view of the incident scope and impact. Flowmon monitors the entire network, sealing gaps between the perimeter, endpoint as well as account.
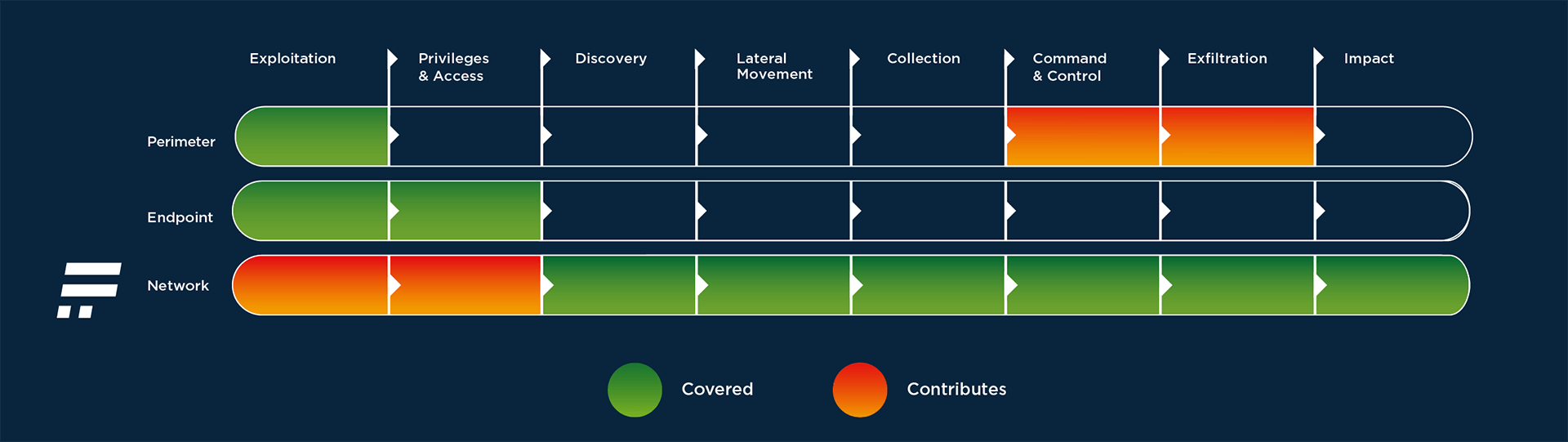
The Flowmon solution uses several techniques simultaneously that can pick up various anomalies and recognize them as indicators of compromise.
Once suspicious behaviors are detected, the administrator is provided with immediate insight and alerting, as well as data for a thorough post-compromise analysis. Adding such Network Detection & Response (NDR, see SOC Visibility Triad) capabilities enables uncovering insider threats, provides comprehensive incident understanding and significantly cuts incident resolution time.
- Machine learning
- Adaptive baselining
- Heuristics
- Behavior patterns
- Reputation databases
- Signature-based detection
How to respond to insider threats with Flowmon
- Gather network traffic metadata exported from different platforms (datacenter, SaaS, Cloud), encrypted traffic analysis included.
- Detection of unknown threats is based upon several techniques (machine learning, adaptive baselining, heuristics, behavior patterns, reputation databases, signature-based detection)
- Once a threat is detected, the user is alerted and can immediately see the event and what it represents in the given context.
- Flowmon can automatically trigger a response via integration with other security tools to block or quarantine the threat. The event is logged and recorded for full forensic drilldown.
Respond swiftly, reduce risk
A good protection plan against insider threats consists of security-aware users and a clever combination of measures to tackle situations before, during, and after an incident. Flowmon complements your existing systems, providing threat detection throughout the compromise life-cycle. It uses machine learning to give you insight into the network without noise or clutter, so that incident response is quick and straightforward. It shows precisely which assets have suffered damage and require repair. Data about previously encountered threats is stored for later analysis to test and refine incident response readiness. In this way, the solution reduces risks, improves prevention and makes sure the system is prepared for future challenges.
Request free trial
Get no-obligation 30-day trial of Flowmon in your network.
Get your trial today