Strengthen Your Security with Network Detection and Response
Flowmon’s network detection & response solution allows Security Operation to detect network anomalies and early indicators of compromise, that bypass traditional security solutions.
Flowmon leverages Artificial Intelligence (AI) and Machine Learning (ML) principles to uncover any hidden malicious activities.
Boost Your Network Detection and Response

Detect all network breaches
Uncover hidden vulnerabilities with state of the art AI-powered network detection engine.

Hunt for network threats
Analyse every attacker’s step and stop it from spreading further.

Respond to network breaches quickly
Contain and eradicate breaches with manual or automatic response.

Forensic cyber security analysis
Analyse all cyber security incidents and build resilient cyber security.
Cyber security use cases
Leverage modern NDR solution in your network
Flowmon tackles anomalies that traditional solutions miss.
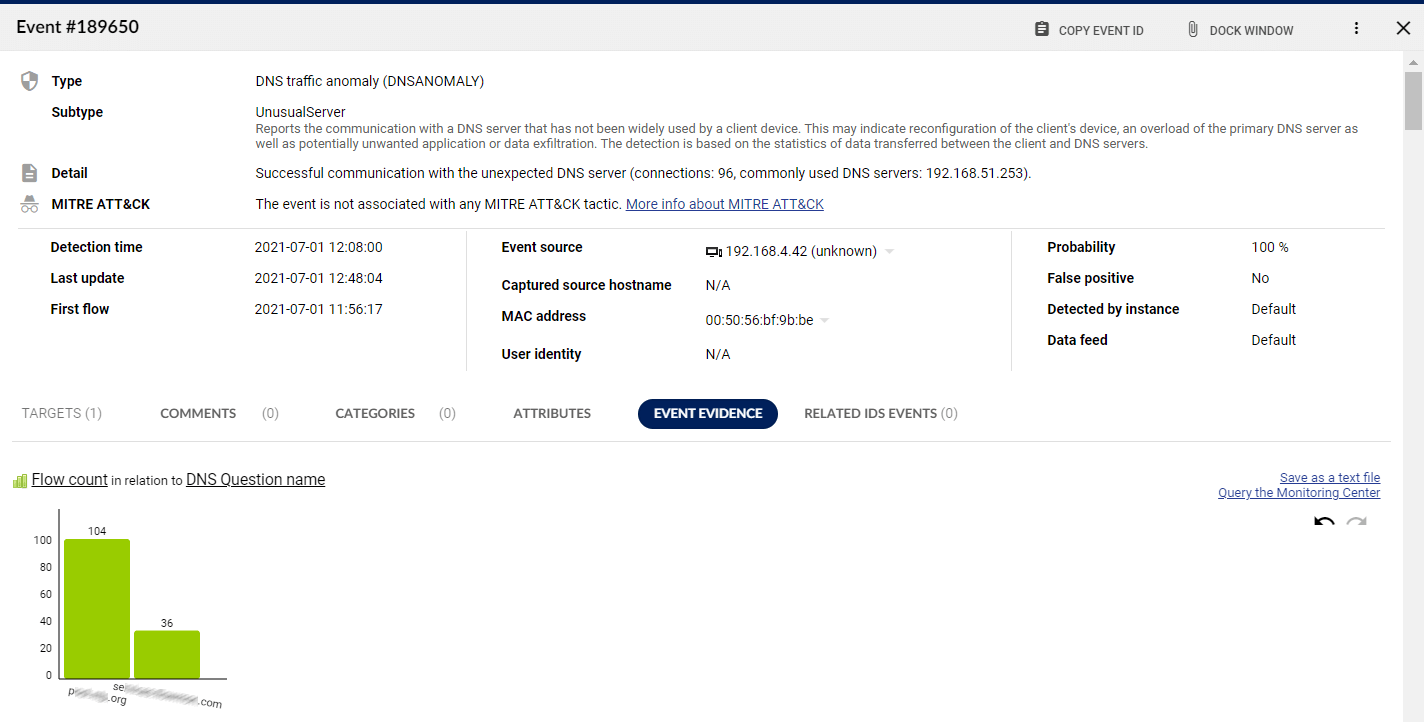
Attack evidence and analysis
Understand every suspicious network event in its complexity and take decisive action without delay.
AI-based detection
Leverage a state-of-the-art detection engine that uses entropy modeling and machine learning to detect suspicious anomalies in your network traffic.
Seamless SIEM integration
Report network detected events via integration with SIEM systems, surveillance, and incident handling systems.
Automated attack recording
Trigger full packet capture upon network event detection. The rolling memory buffer ensures no data is lost.
Custom methods
Create your own custom methods and red-flag malicious or unwanted traffic specific to your environment or policies.
Threat intelligence
Enhance your network detection and response capabilities with a combination of commercial and community threat intelligence feeds and stay briefed on the latest indicators of compromise.
Discover Flowmon NDR
(more technical features)
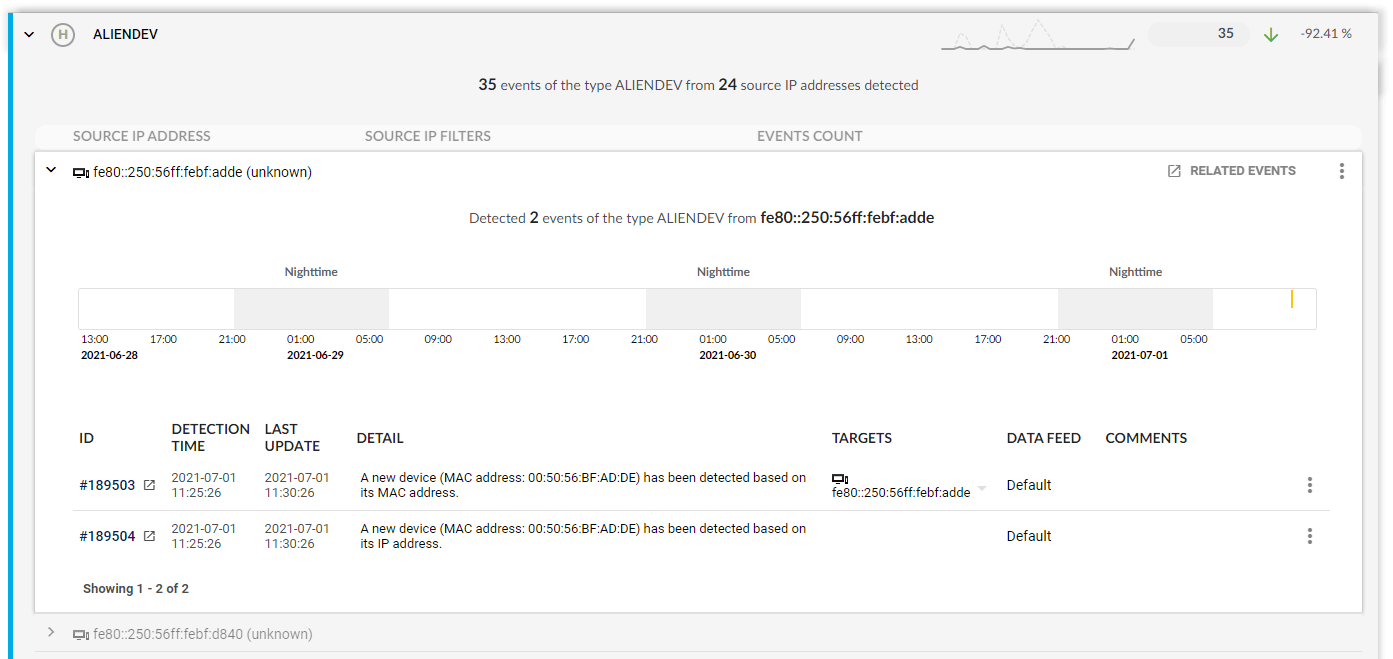
Unknown threat detection
Flowmon analyzes network traffic for signs of malicious activity and informs you about every suspicious or anomalous occurrence to give you a timely warning about unknown and insider threat actors operating in your network. It represents the network-centric approach to malware detection that complements traditional inline solutions and enables timely and proactive threat hunting.
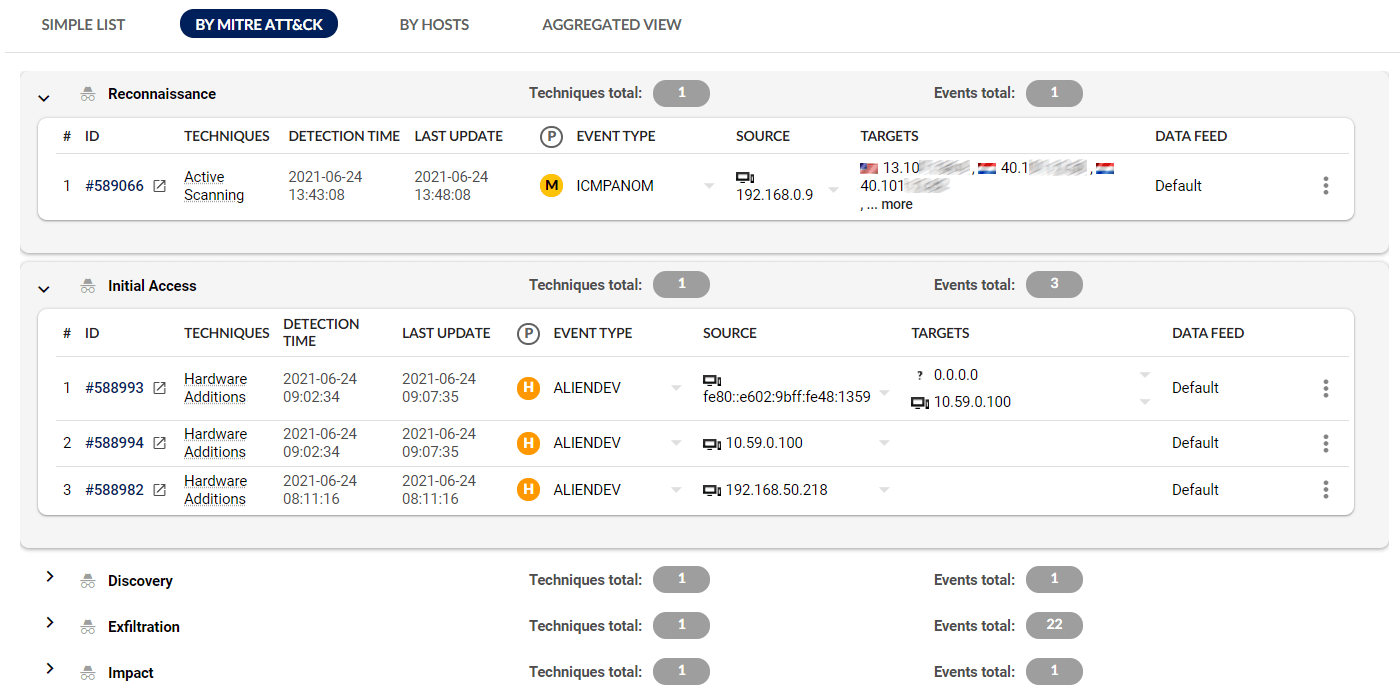
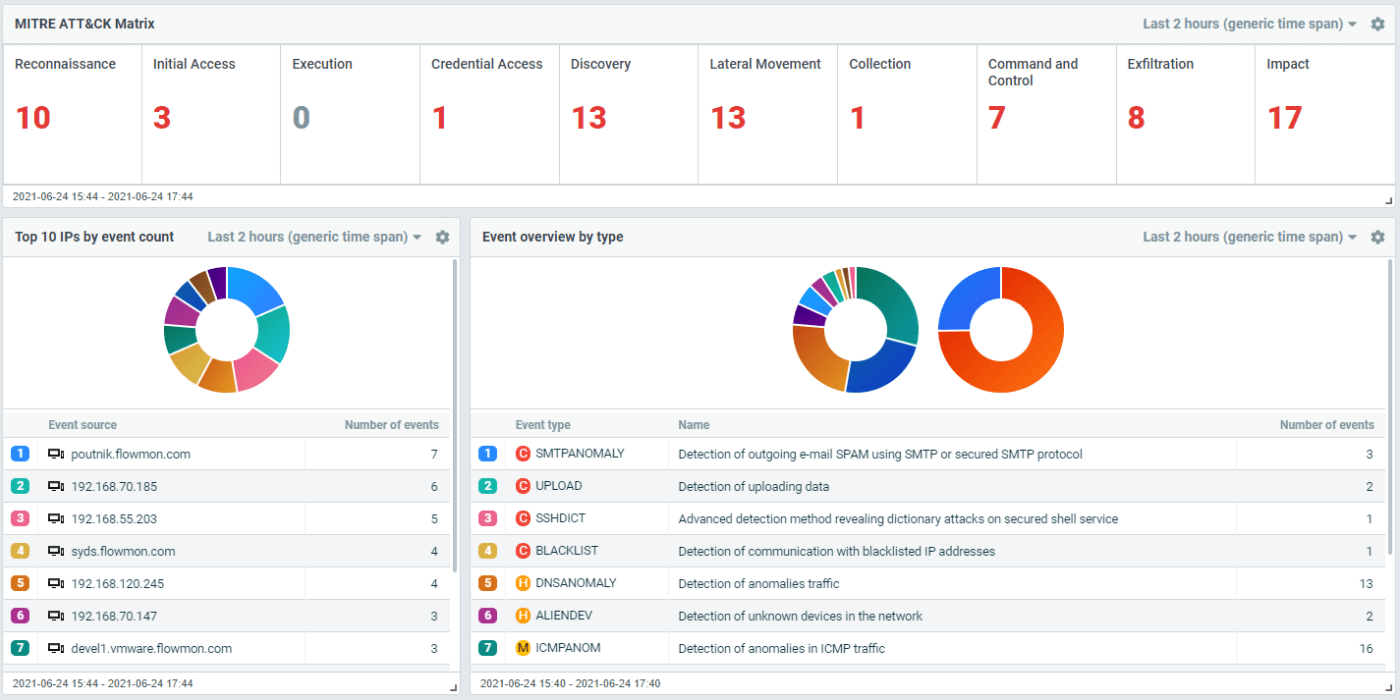
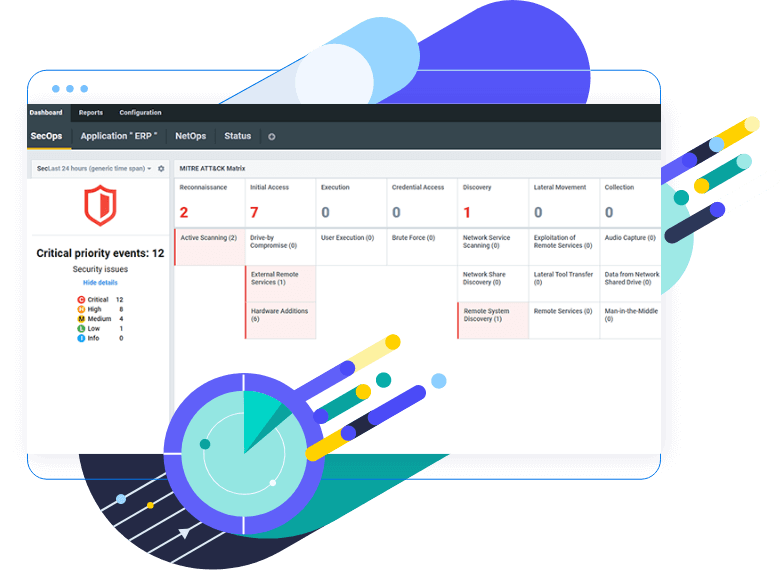
Context-aware investigation
Detected security events are categorized as MITRE ATT&CK® tactics and techniques to provide a clear idea about the attack’s severity, scope and future development. By drilling down into an event, you can quickly access full detail of the event to facilitate prompt triage and response.
Attack surface reduction
Flowmon leverages over 40 methods and more than 200 algorithms including machine learning, behavior analysis, MISP threat intelligence, IoCs, or reputation databases with automated packet capture available on demand. In combination with perimeter and endpoint security solutions, it adds an additional protection layer and improves the overall security posture.
Noise-free insights
The ML-powered engine discerns between network anomalies and normal traffic, and allows you to whitelist selected traffic to accelerate fine-tuning. Security events are ranked by severity and visualized in the UI with additional detail only a click away. By integrating Flowmon NDR with other security solutions, you can harden your entire defense matrix. For instance, you can use it to feed detected events to your SIEM and thus augment its analytical capability with the network-centric view, or enable your firewall to perform triggered quarantine of IP addresses involved in security events detected by Flowmon.
Flowmon Named Technology Leader in Network Detection and Response
Released in 2022, the SPARK MatrixTM report conducted by Quadrant Knowledge Solutions provides market insights, competitive evaluation, and vendor rankings to better understand the capabilities of different solutions in the network detection and response (NDR) market. In Customer Impact and Technology Excellence they awarded Flowmon's NDR the highest ranking of Technology Leader.
Get the report

Request free trial
Get no-obligation 30-day trial of Flowmon in your network.
Get your trial today