Flowmon ADS Network anomaly detection system
Powered by an intelligent detection engine, Flowmon ADS leverages behavior analysis algorithms to detect anomalies concealed within network traffic to expose malicious behaviors, attacks against mission-critical applications, data breaches and indicators of compromise.
Seal the gap
Between perimeter and endpoint protection.
Expose breaches
Ransomware, malware, insider & unknown threats, etc.
Use machine learning
Leverage intelligent technology to detect threats others miss.
Watch Webinar: Mastering Incident Response: Becoming a Proficient Security Analyst
Advantage at every stage of compromise
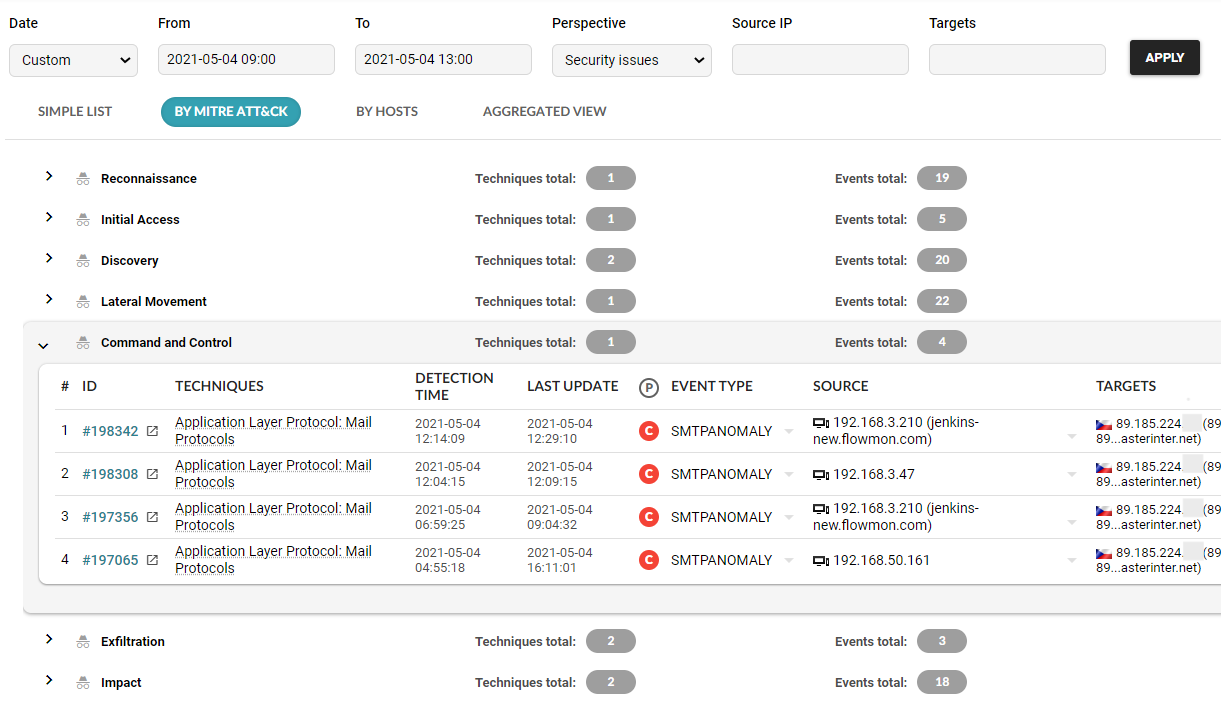
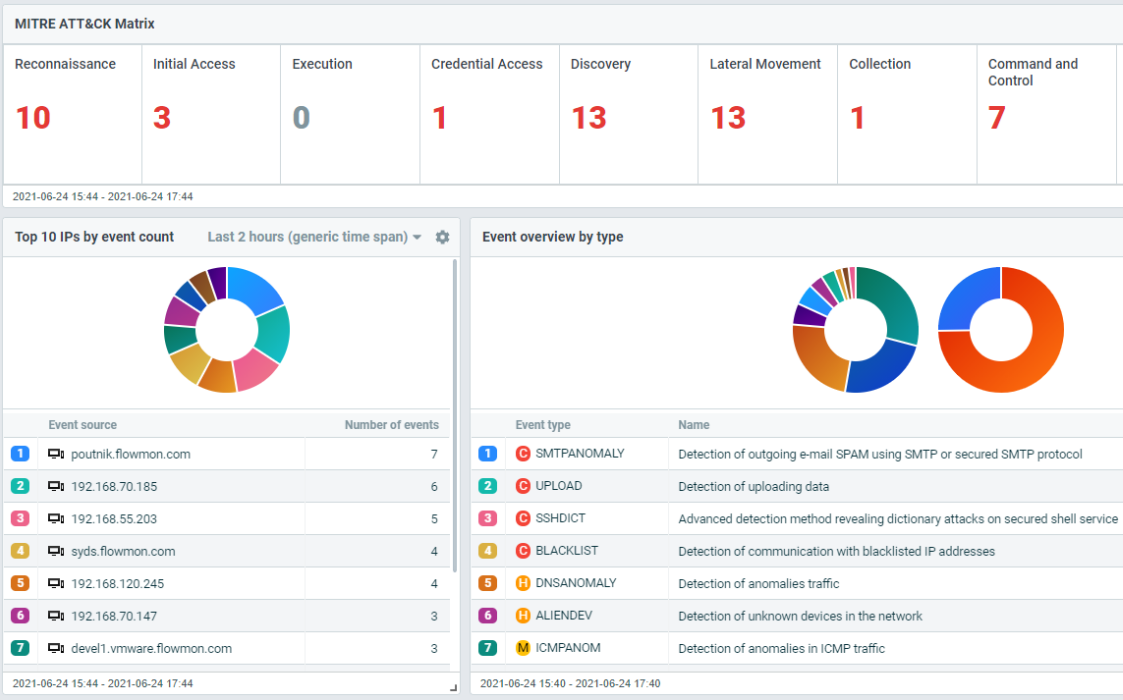
Flowmon ADS adds the network-centric layer of defense to your security matrix (see SOC Visibility Triad) to detect the slightest network anomalies that indicate the activity of unknown and insider threats undetectable by perimeter and endpoint security. Context-rich incident visualization in the MITRE ATT&CK® framework keeps you briefed on the scope, severity and future development of the breach.
Automated detection and response (NDR)
Threats are detected early, instantly and automatically thanks to 40+ AI-based methods and 200+ algorithms. Reveal unknown threats, malware, ransomware, Windows DNS SIGRed exploitation, Trojan attacks or threats hidden in encrypted traffic. The ADS can be integrated with network access control, authentication, firewall and other tools for immediate incident response.
Leverage Flowmon IDS Probe powered by Suricata
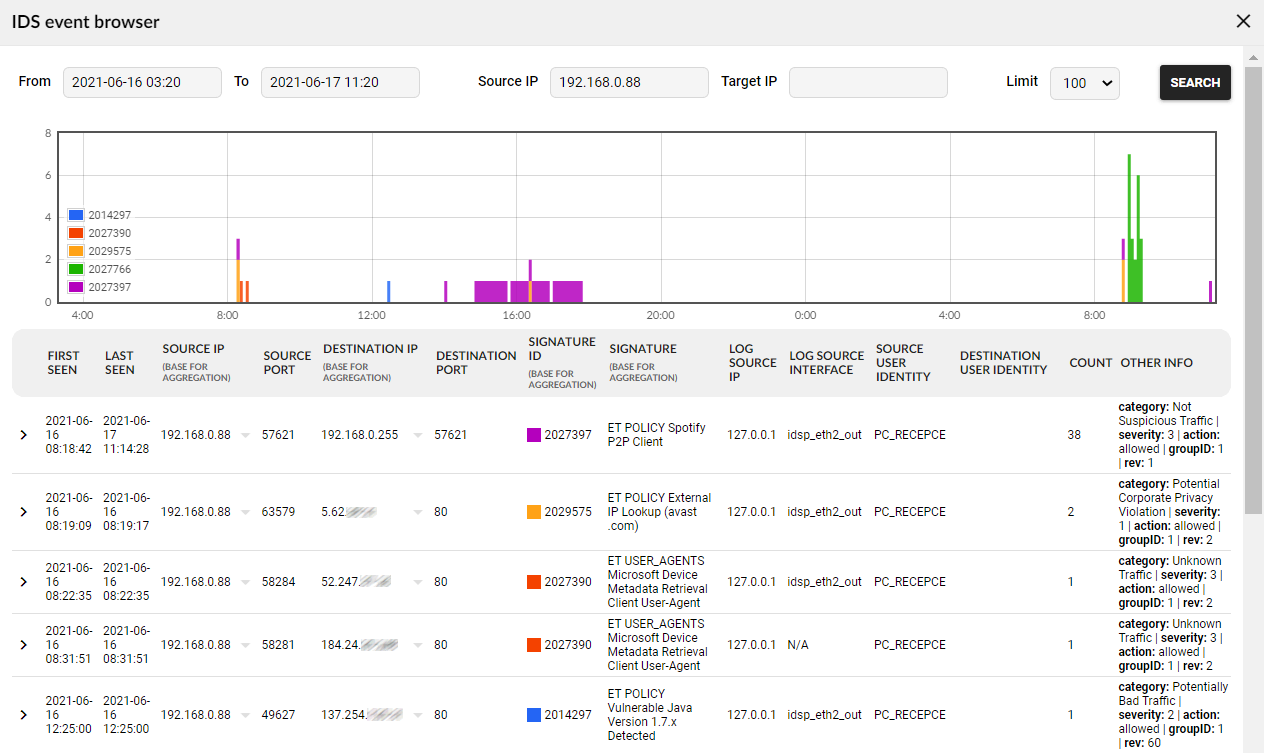
Flowmon ADS includes a built-in IDS collector that receives events from Flowmon IDS Probe powered by Suricata and allows the system to cover more attack vectors by combining the best of the two signature-less and signature-based approaches.
Minimize false positives and stay focused
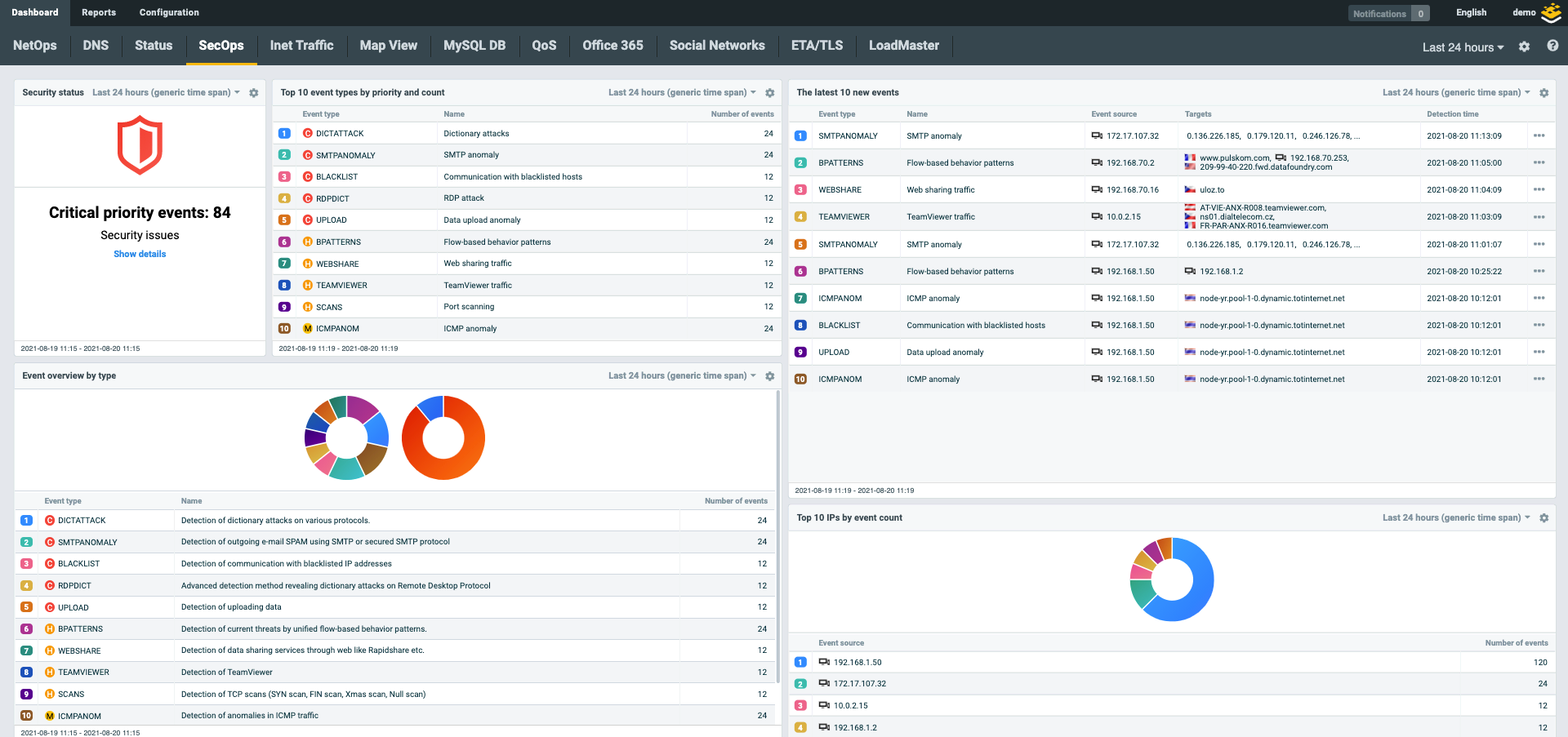
Center on relevant issues only. The ADS distinguishes between anomalies and normal traffic and only alerts you when a real danger occurs. Detected security events are ranked by severity, and the solution’s built-in expertise enhances your situational awareness and speeds up triage and response.
Configuration wizzard
The system comes with pre-defined configurations for a variety of network types and automatically adjusts the settings after the initial configuration by using a simple wizard. Then, by managing false positives, maximize the relevancy of detected events.
Attack evidence and analysis
Understand every suspicious event in its complexity. Context-rich evidence, vizualisation, network data or full packet traces for forensics allow taking decisive actions promptly.
Prioritization and reporting
Use out-of-the-box prioritization or apply your own severity rules at a global, group or user level. Create custom dashboards for security, networking, IT helpdesk or managers based on their interests.
Advanced action triggering
Respond to attacks automatically through script-based integration with network or authentication tools. When detecting an event, Flowmon can connect to, e.g. Cisco ISE through pxGrid, and quarantine the malicious IP address.
Attack recording automation
Trigger full packet capture automatically when detecting an event. Thanks to the Rolling Memory Buffer, the recorded packet trace includes network data, even from the period before the attack started. Use a filter to store the particular attack communication only.
User defined methods
Create custom detection methods flexibly. Red flag malicious, unwanted or otherwise interesting traffic specific to the client's network environment or policies. You only need to create a rule in an SQL-like syntax.
Behavior patterns
Detect misuse and suspicious behaviour of users, devices and servers. By understanding protocols such as DNS, DHCP, ICMP and SMTP you can reveal data exfiltration, reconnaissance, lateral movement and other unwanted activity.

"Flowmon is an integral part of a complex system that collects network data from partner institutions and detects traffic anomalies, allowing us to enhance the interception capability of each organization with a global security perspective."

Head of the NTA Department
See a fully interactive demo of Flowmon and learn what issues it can tackle for you
Detection and response explained
1. Detection
Machine learning, adaptive baselining, heuristics, behavior patterns, reputation databases, signature-based detection – all combined into one versatile capability that examines network traffic from multiple points of view and thus covers a wider spectrum of scenarios.
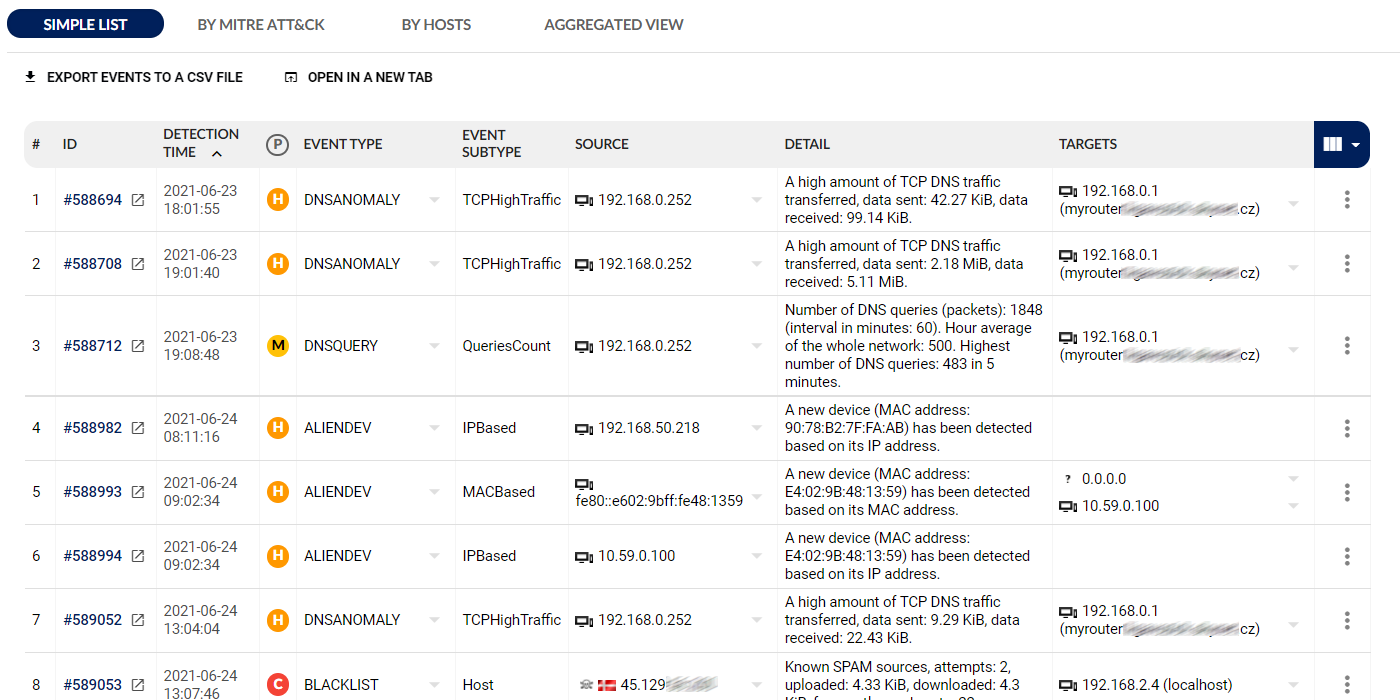
2. Reporting
The analytical view provides context-rich visualization of every attack including MITRE ATT&CK® mapping with drill-down analysis for a detailed understanding of what exactly is happening.
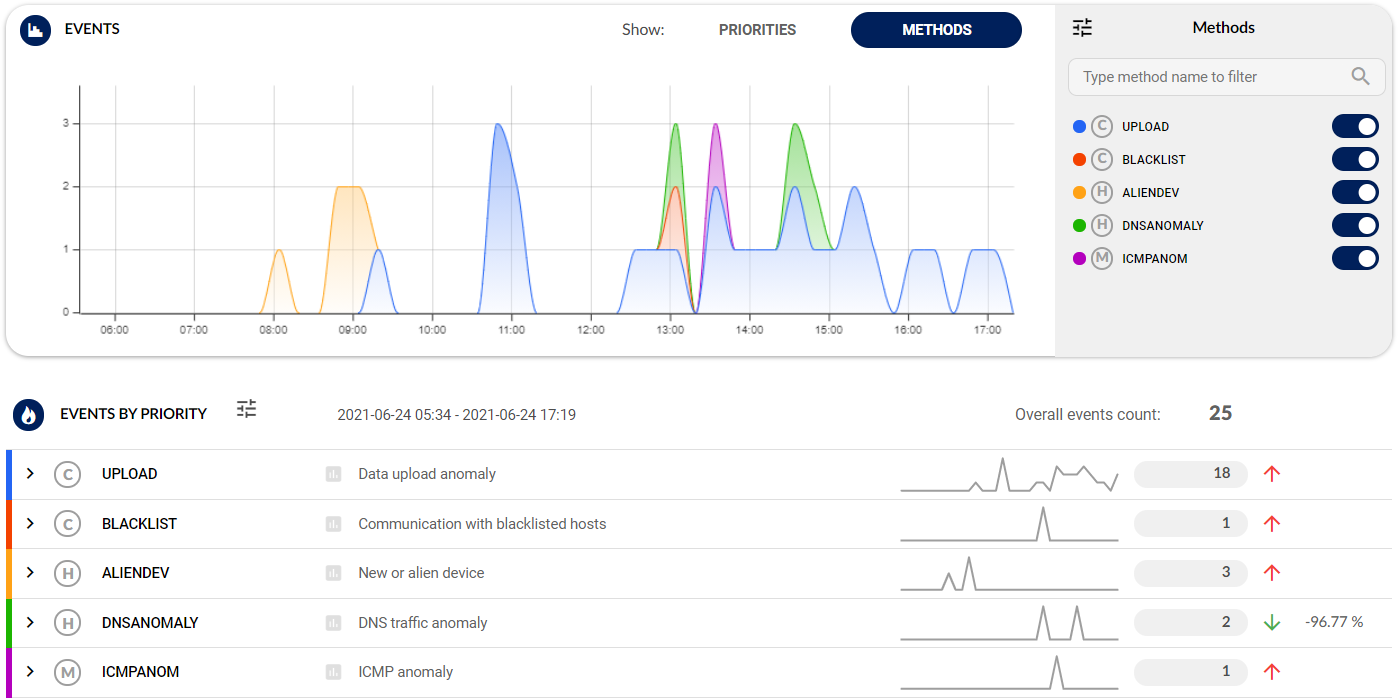
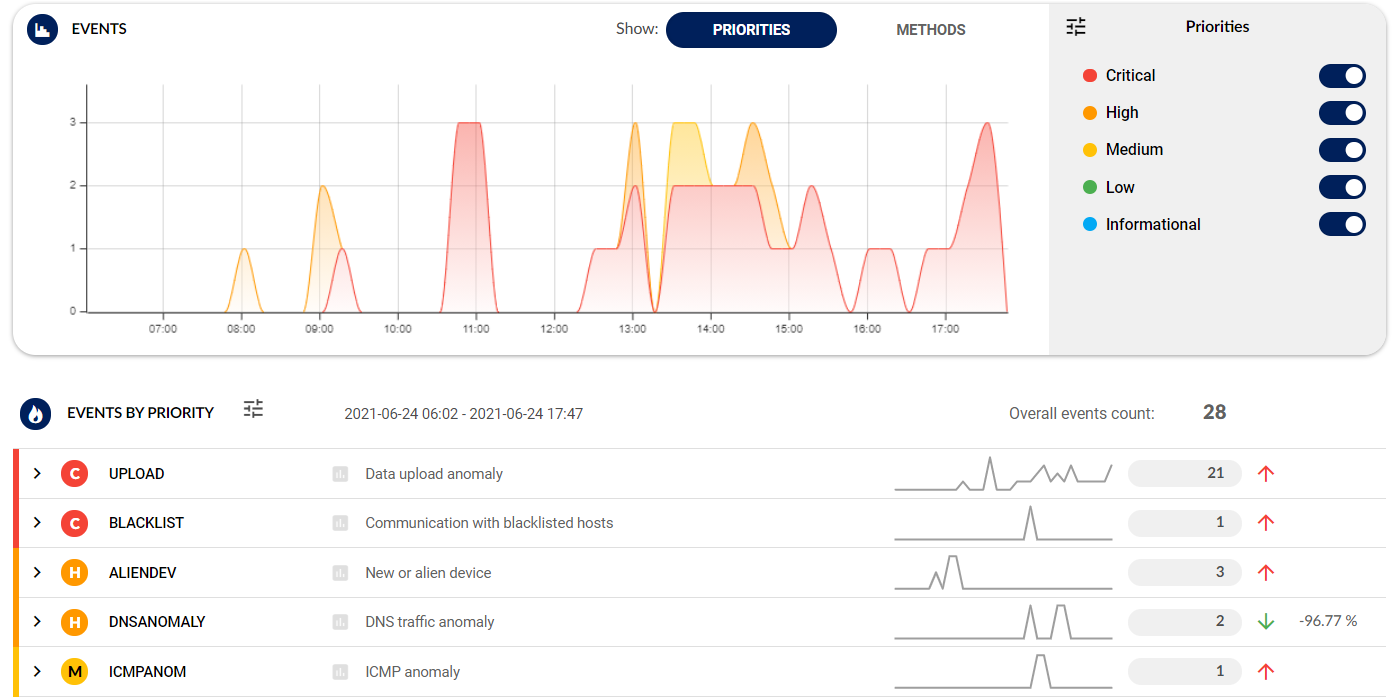
3. Triage
Incidents are ranked according to your priorities with an easy-to-use customization wizard that builds upon battle-tested, out-of-the-box configuration.
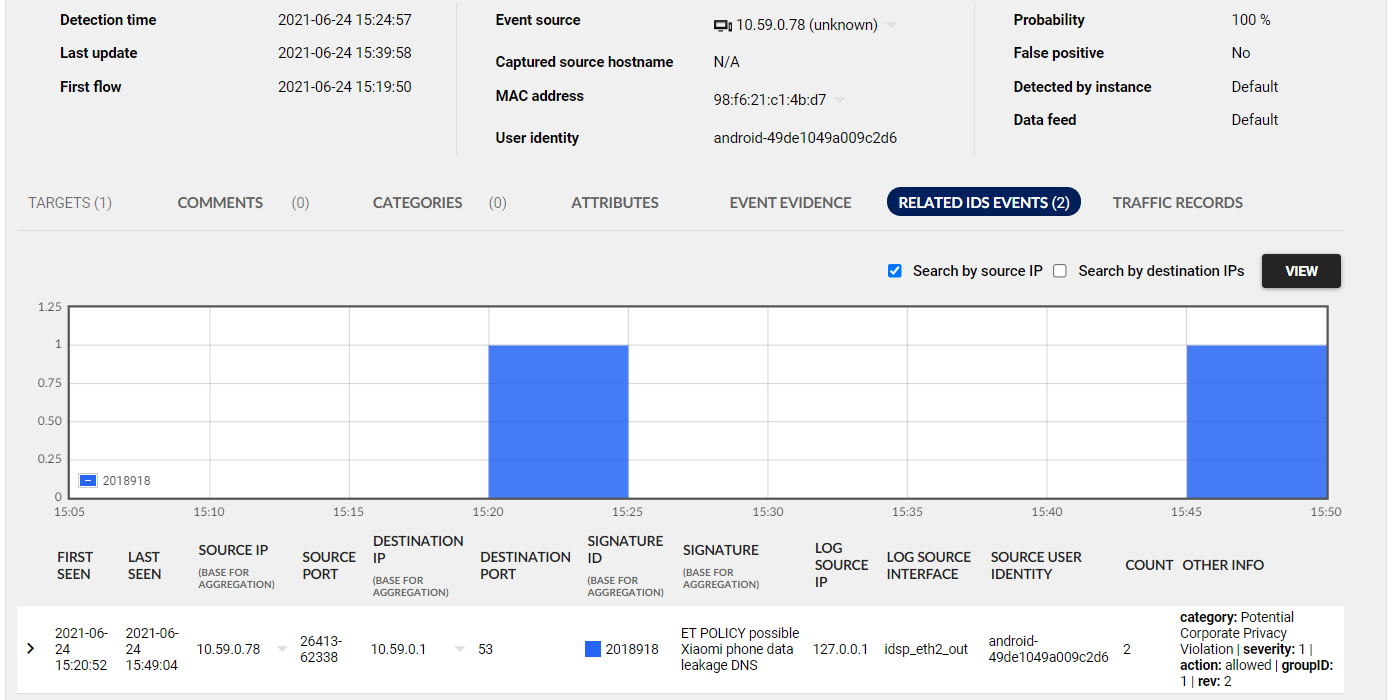
4. Response
Flowmon ADS can be integrated with network access control, authentication, firewall or other tools for immediate and automated incident response.
Integrations
Flowmon serves as a critical source of information to log management, SIEM, big data platforms, incident handling or response tools. You may integrate it via syslog, SNMP, email, REST API or custom scripts.
Get in touch
Do you have question around the solution or want to schedule a call. Write us a message.
Contact usRequest free trial
Get no-obligation 30-day trial of Flowmon in your network.
Get your trial todayRead more about the ADS
Flowmon ADS Models Specification
Flowmon and SIEM – Seamless Integration
Encrypted Traffic Analysis Datasheet