What happens next heavily depends on your company size and responsibilities within the IT team. Large organizations with a dedicated IT security team will most likely adopt mature tools such as a SIEM (Security Information and Event Management) system that integrates all the security events and incidents. They will follow their standard security procedures and work through the detected incidents.
Small and medium size organizations struggle with resources and IT security is just one of the responsibilities of a general IT team. For such organizations the major tool in place and single pane of glass is ITIM (IT infrastructure monitoring) such as Progress WhatsUp Gold where they manage all the alerts and events related to their digital environment.
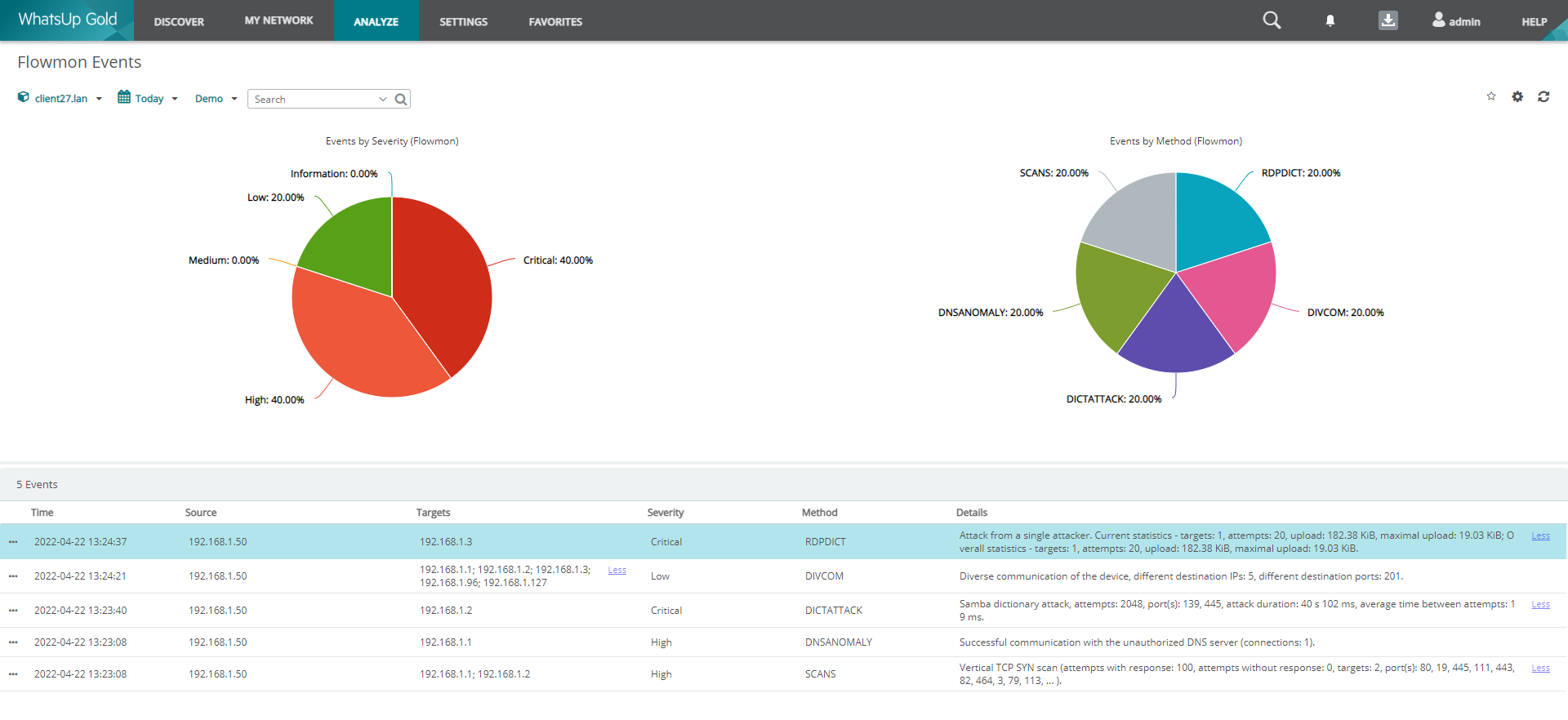
Efficiency of tools in place is especially important for these resource constrained IT teams. With the needs of such organizations in mind we have designed an integration between WhatsUp Gold and Flowmon ADS to bring security incidents detected through NDR technology into a unified view of WhatsUp Gold console. The integration relies on the Flowmon REST API and takes 5 minutes to configure if both Flowmon and WhatsUp Gold are already in place. As a result events detected by Flowmon ADS are displayed in WhatsUp Gold including summary statistics by severity and event type with the option to drill down to details of each individual event.
Figure 1: Security events from Flowmon ADS displayed in WhatsUp Gold user interface. In this example we can see a range of malicious activities conducted by device 192.168.1.50 targeting other devices in the internal network.
From an event overview there is always the option to drill down directly into the Flowmon ADS to investigate specific events in detail.
Figure 2: Drill down available from context menu for each event displayed in WhatsUp Gold.
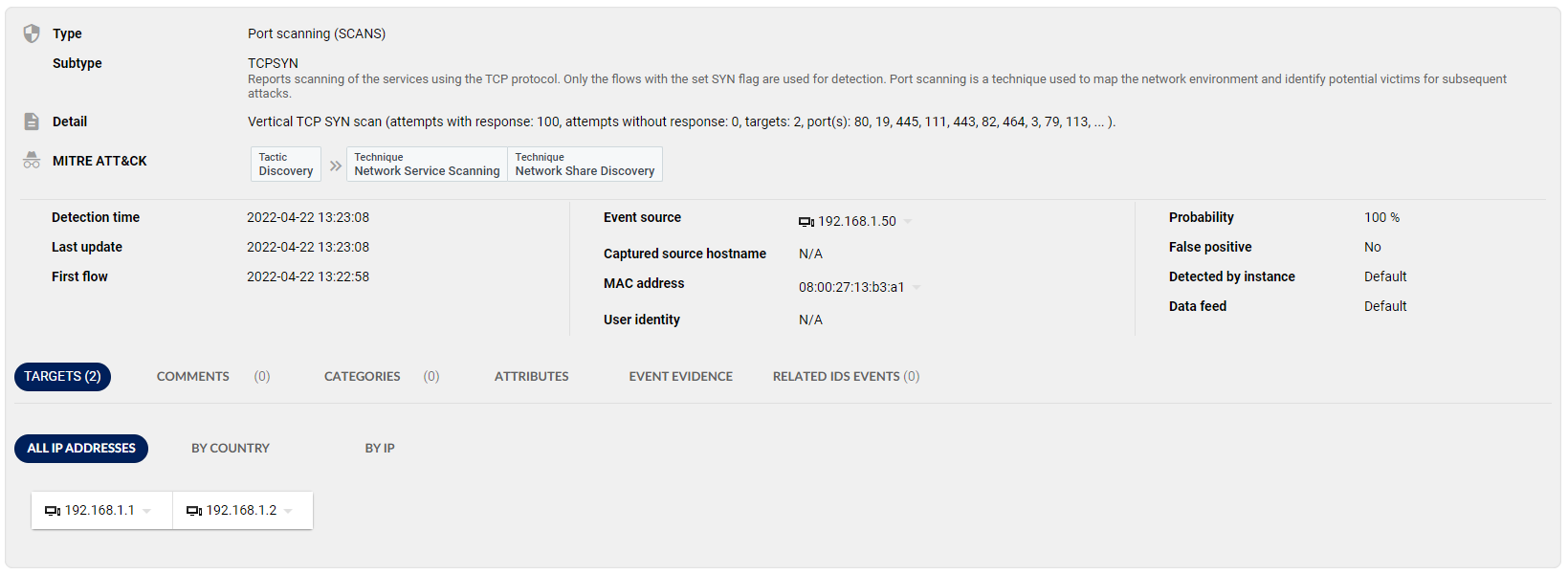
For each event Flowmon ADS provides a detailed classification of the malicious activity such as type and subtype or MITRE ATT&CK framework tactics and techniques. There is a human understandable detail that summarizes and further explains the nature of the activity in the network. In addition to event source IP address, MAC address or even user identity (if available) is provided. Further details and drill downs show network traffic that caused the event. All these details can be further augmented by integrated signature-based intrusion detection (leveraging Suricata) or full packet capture if Flowmon Probes are in use as a source of network telemetry.
Figure 3: Detail of an event representing discovery tactic through a vertical TCP SYN scan conducted by a device with IP address 192.168.1.50 against two devices 192.168.1.1 and 192.168.1.2. This screenshot is from the Flowmon ADS page where WhatsUp Gold will navigate the user automatically when drill down is requested.
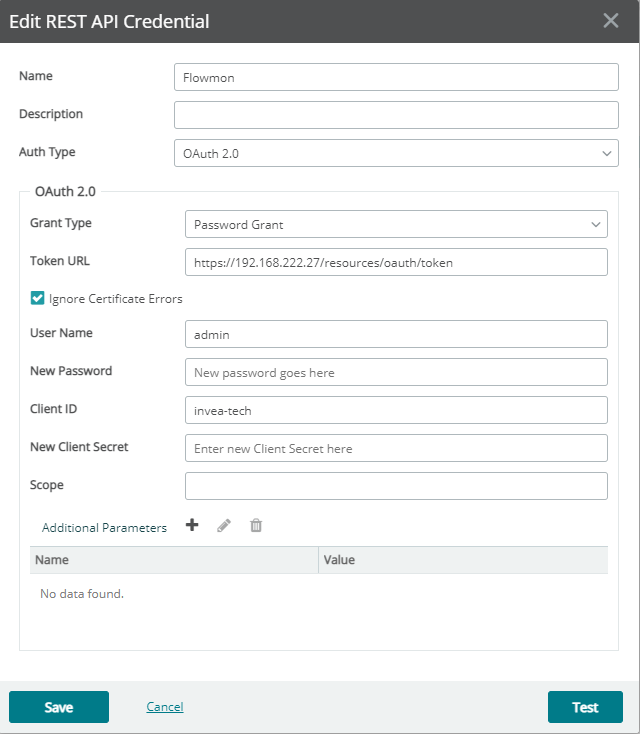
From the configuration perspective the connection of WhatsUp Gold to Flowmon requires specific REST API credentials to retrieve data from the Flowmon appliance. In Settings > Libraries > Credentials create new REST API Credentials specific to your Flowmon appliance. Obviously Flowmon ADS module needs to be installed on Flowmon appliance.
Figure 4: Flowmon REST API credentials. Token URL requires proper IP address or host name corresponding to your Flowmon deployment as well as login and password. No client secret is required. Client ID needs to be configured to “invea-tech” and authentication type is “OAuth 2.0”. If you are using a self-signed certificate on Flowmon side you need to enable “Ignore Certificate Errors”. However, proper security practice mandates to generate and use a trusted certificate through certification authority.
Do not forget to assign these particular credentials to your Flowmon device in Device Properties > Credentials. Now everything is ready to analyze Flowmon ADS events directly in WhatsUp Gold. Navigate to Analyze > Flowmon > Flowmon Events.
We have demonstrated how to integrate security events from Flowmon ADS in WhatsUp Gold that typically acts as a single pane of glass and main tool for IT professionals responsible for the digital environment.
Here at Progress we are on a mission to redefine Application eXperience and provide IT professionals with tools that will give them back control of the whole digital environment. The presented capability is based on WhatsUp Gold version 2022.0 that provides out of the box integration with Flowmon to gather and present volumetric and performance metrics as well as security events using Flowmon’s native REST API and is available to all WhatsUp Gold and Flowmon users. Flowmon version 11.1.x or 12.x is required. For security events Flowmon ADS version 11.4.x or 12.x is required.
