NDR is an indispensable piece of an overall security operation strategy.
So, what is Network Detection and Response (NDR)? Network Detection and Response uses non-signature-based techniques (as opposed to the signatures used by anti-virus/anti-malware) such as machine learning to spot anomalous and suspicious traffic that could point to a cyberattack. NDR solutions deeply parse raw network traffic and flow data to build models that define what traffic is normal on the network and can then spot deviations which prompt alerts.
“In addition to monitoring north/south traffic that crosses the enterprise perimeter, NDR solutions can also monitor east/west communications by analyzing traffic from strategically placed network sensors. Response is also an important function of NDR solutions. Automatic responses (for example, sending commands to a firewall so that it drops suspicious traffic) or manual responses (for example, providing threat hunting and incident response tools) are common elements of NDR tools,” argues Gartner.
While NDR can address myriad network issues, it is especially adept at dealing with hack attacks. We’ll use ransomware as just one example.
How Network Detection and Response (NDR) Addressed Ransomware
Ransomware attacks occur at an ever-quickening pace, crippling organizations and costing millions of dollars in ransom payoffs, lost productivity and diminished consumer confidence.

One accelerant is Ransomware as a Service (RAAS), readily found on the Dark Web. Threat actors look to make attacks easier, and what could be easier than an attack that is pre-built and offered as a service?
The Sophos State of Ransomware Report 2021 shows that the average cost to deal with an attack in 2021 was $1.85 million. This was up from the 2020 average of $761,106. These costs cover all the activities required to recover from a ransomware attack. These include paying the ransom, the costs associated with business disruption when IT systems are unusable, operational downtime for machinery and other plant devices usually controlled by IT systems, staff overtime payments during the recovery period and more. Within the 2021 figures, the actual ransom payment average was only $170,404.
The Security Operations Center (SOC) Visibility Triad
While solutions such as NDR tools are critical to network and IT security, having a framework in which NDR fits is just as vital. One such approach is the SOC Visibility Triad, a concept created by Anton Chuvakin of Gartner, which postulates that deploying complementary security tools that make up for each other's shortcomings will significantly reduce the chances that an attacker will be able to achieve their goals.
The Triad’s three pillars are:
- EDR for endpoint security,
- SIEM for processing logs and correlating events, and
- NDR for behavior analysis from the network perspective.
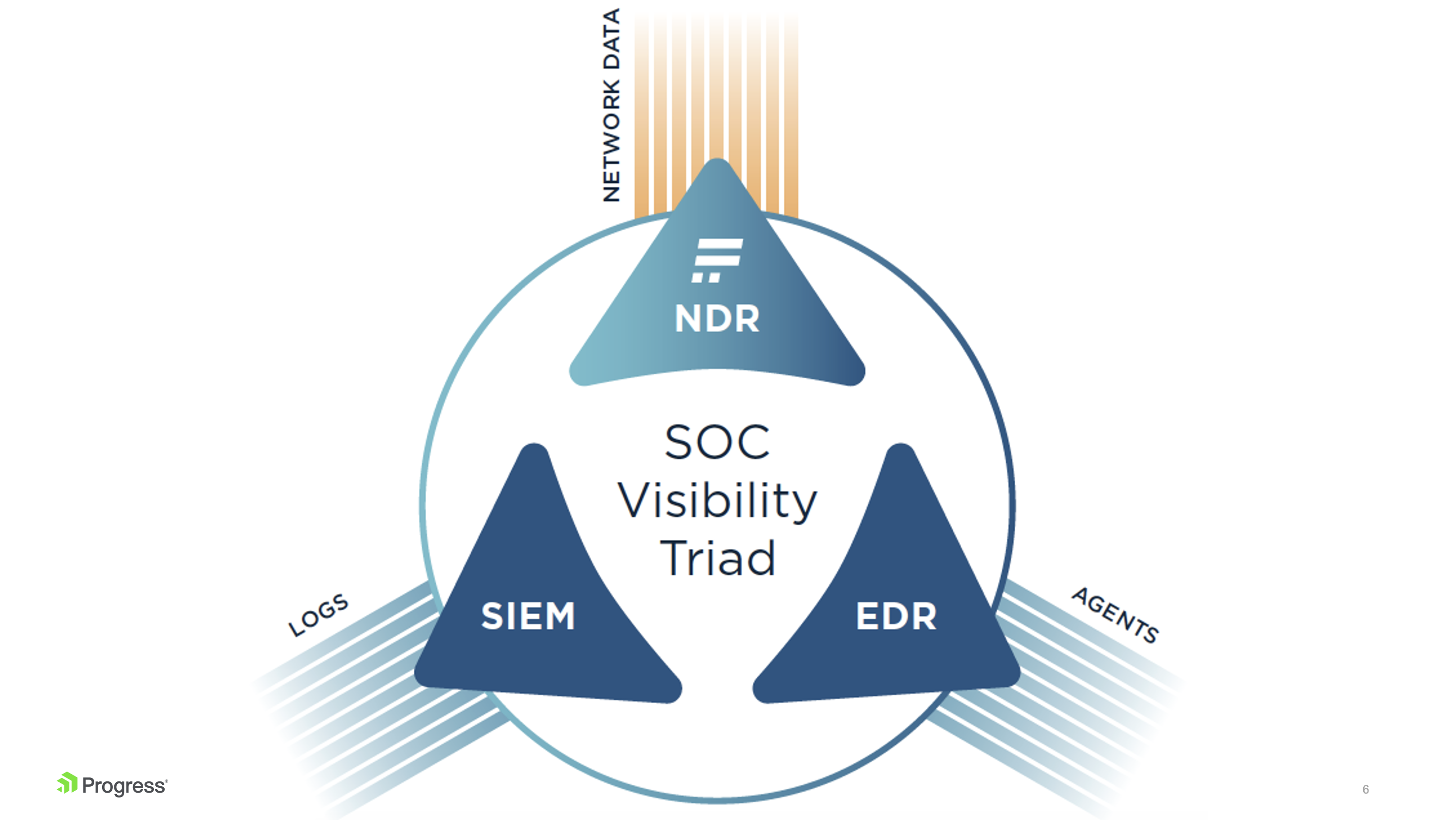
Today’s top security teams turn to a security model that extends log management and end-point protection with network detection and response tools. The NDR pillar compensates for the weak points of the other two pillars, SIEM and EDR, and together gives full visibility across complex IT environments.
Each of these segments addresses a different part of the anatomy of an attack. IT should have all three pillars covered to increase the probability of catching attacks – and catching them early. Lets dive into each pillar.
Security Information and Event Management (SIEM)
The first pillar is SIEM (Security Information and Event Management) and UEBA (User and Entity Behavior Analytics).
Some experts believe that over 80% of successful hacks are related to compromised credentials – a big part of the exploit world. That’s why having a deep understanding of what normal behavior looks like versus what abnormal behavior looks like is vital.
Let’s say someone tries to log in 200 times in less than a second. This is an activity you should do something about quickly, such as cutting that device off from the network.
In a large user environment, IT needs a way to collect all relevant logs, aggregate them and analyze them. Imagine dealing with it all manually, poring through thousands of logs. This doesn’t work for a small shop and it certainly doesn't scale for enterprise networks.
The point is that user behavior analysis and log aggregation are so key.
End Point Detection and Response (EDR)
The second Pillar is EDR, or End Point Detection and Response. When an asset or set of assets is compromised, cybercriminals are one step closer to now getting privileged access – a real disaster.
Network Detection and Response (NDR)
The third pillar, Network Detection and Response, is still sometimes called network traffic analysis (NTA), but evolved into NDR as the solutions grew.
NDR is about identifying intrusions across the network, as well as:
- Offering a way to triage issues,
- Narrowing down to what really matters, and
- Filtering out the noise
NDR lets incident responders and SOC operators get to the items that truly matter, staying ahead of issues and determining their actual impact state.
The idea is to catch the exploit at the beginning, seeing the footprints before the full impact of the exploit emerges. NDR is about finding and detecting those “small wins” helping you to understand what's anomalous so that you can then stop it and prepare for the next time that it happens.
“NDR solutions primarily use non-signature-based techniques (for example, machine learning or other analytical techniques) to detect suspicious traffic on enterprise networks. NDR tools continuously analyze raw traffic and/or flow records (for example, NetFlow) to build models that reflect normal network behavior,” Gartner argued. “When the NDR tools detect suspicious traffic patterns, they raise alerts. In addition to monitoring north/south traffic that crosses the enterprise perimeter, NDR solutions can also monitor east/west communications by analyzing traffic from strategically placed network sensors.”
The diagram below shows where NDR sits and how it is a key source of network truth. 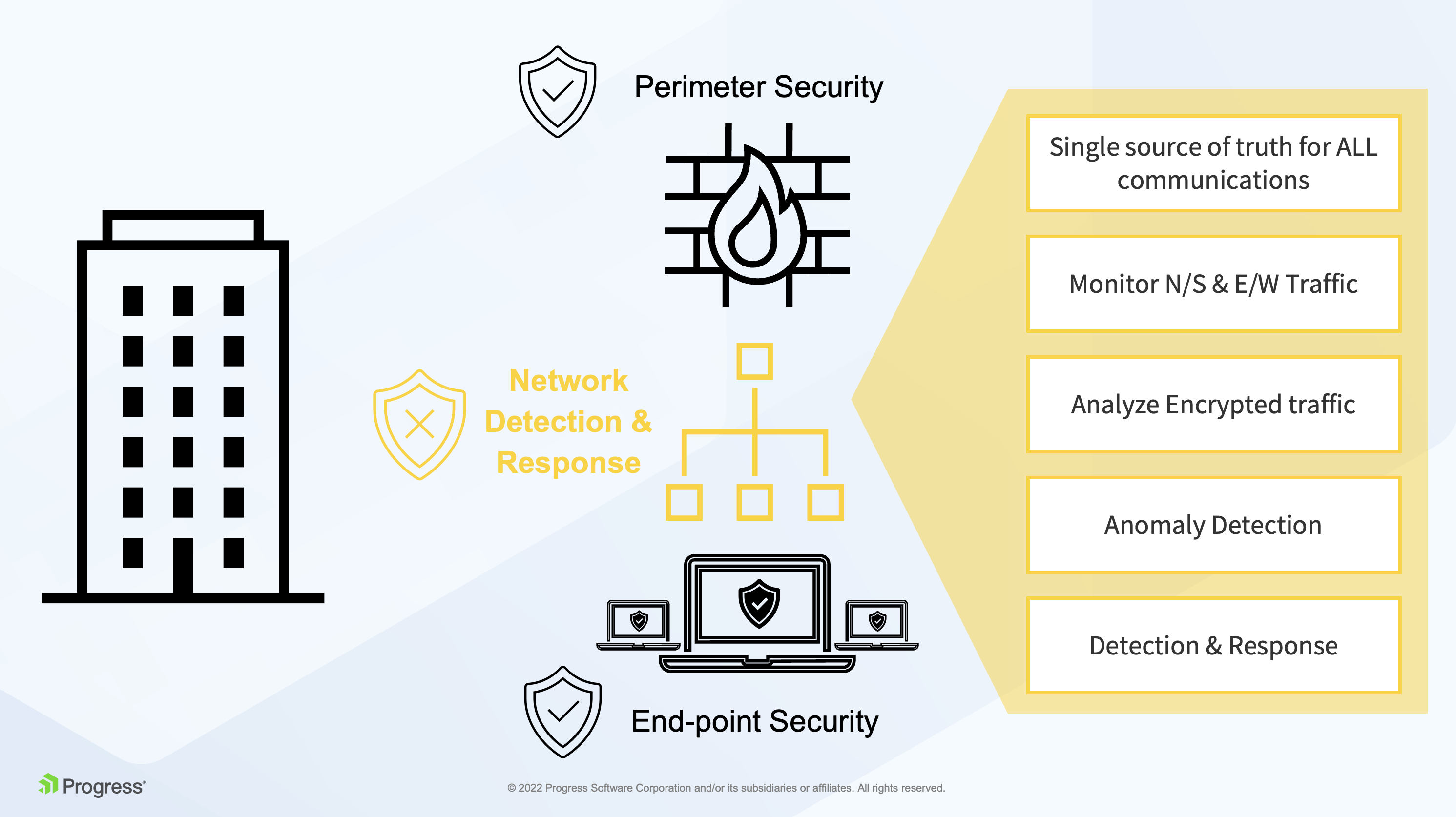
SIEM and EDR are important solutions, but still leave blind spots in the east-west corridor where adversaries can hide after they’ve slipped past perimeter defenses. By taking a network-based approach instead, NDR fills those critical visibility and coverage gaps.
How? Because every asset, whether in the cloud or an on-premises data center, uses the network to communicate. That makes NDR the ultimate source of truth for cloud and hybrid security. Advanced NDR solutions are also capable of monitoring and analyzing encrypted traffic. It is estimated that over 90% of malware is hidden this way.
Early Breach Detection
NDR solutions permanently observe network traffic, analyzing communication to spot anomalies and reveal suspicious behavior. This enables a response to as yet unknown security threats undetectable by other technologies.
The average time taken from identifying a breach to safely containing it was 287 days in 2021. Meanwhile, threat actors are developing new malware every day for which the signature has not been created. That is why an NDR solution that does not rely on signatures, but leverages machine learning (ML), is critical.
The Three Steps of NDR
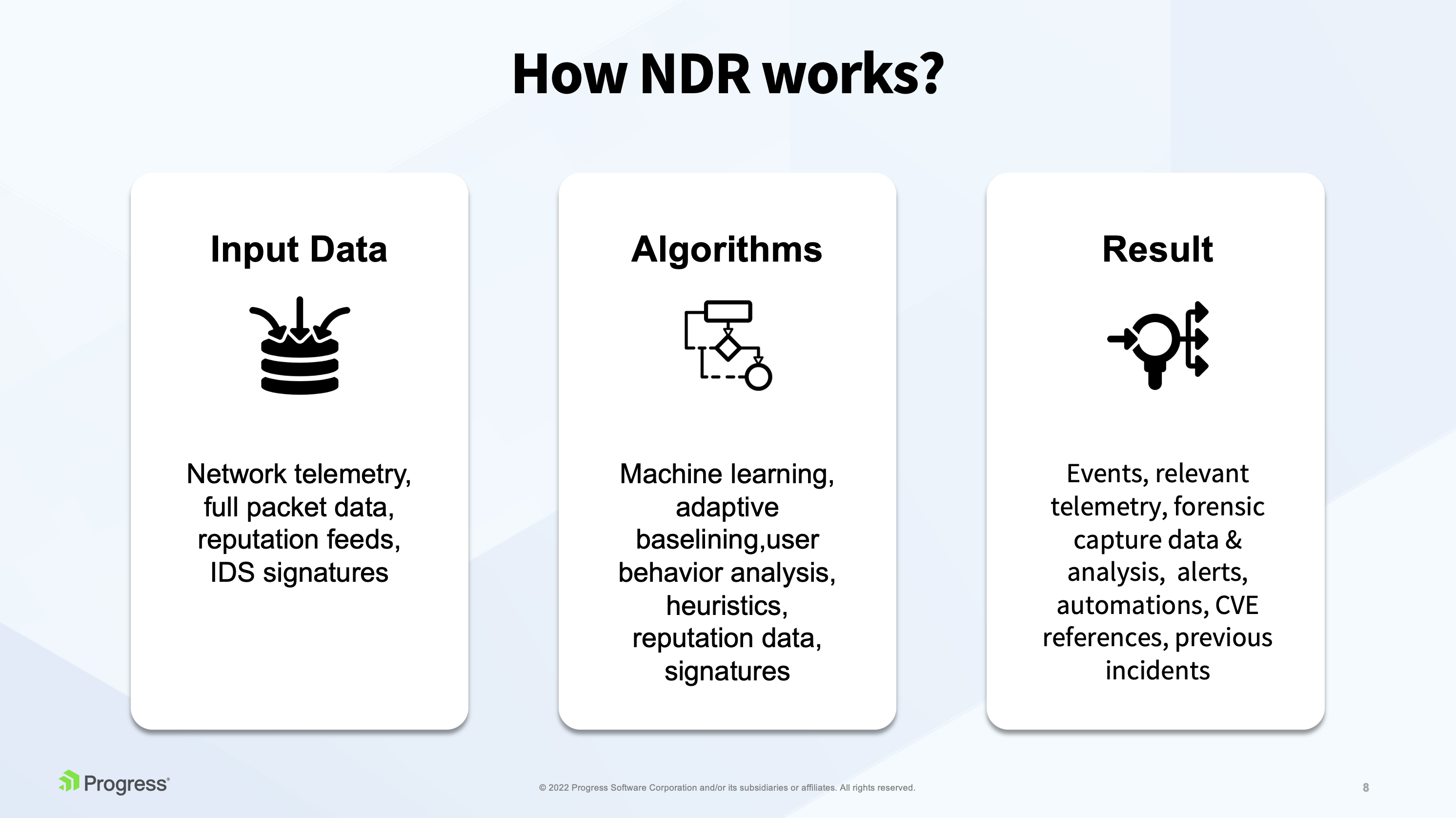
Data Collection/Algorithms
By applying Machine learning techniques, modeling baselines and analyzing user behavior in the network, NDR tools can uncover hidden malicious activity and alert on it.
The results are where the network security rubber meets the road, as an NDR solution brings all the evidence together in one place where IT can see relevant telemetry data, captured forensic data and analysis.
The traditional method to detect anomalies in network traffic is a statistical analysis looking for traffic spikes and deviations from baselines. While useful for some use cases, this is behavior analysis — not NDR. To truly provide NDR, you need to be able to go beyond traditional statistical analysis and detect threats and attacks that are not volumetric in nature.
Let’s go together beyond the traditional statistical approach and look at a number of different tools an NDR solution can leverage for detection.
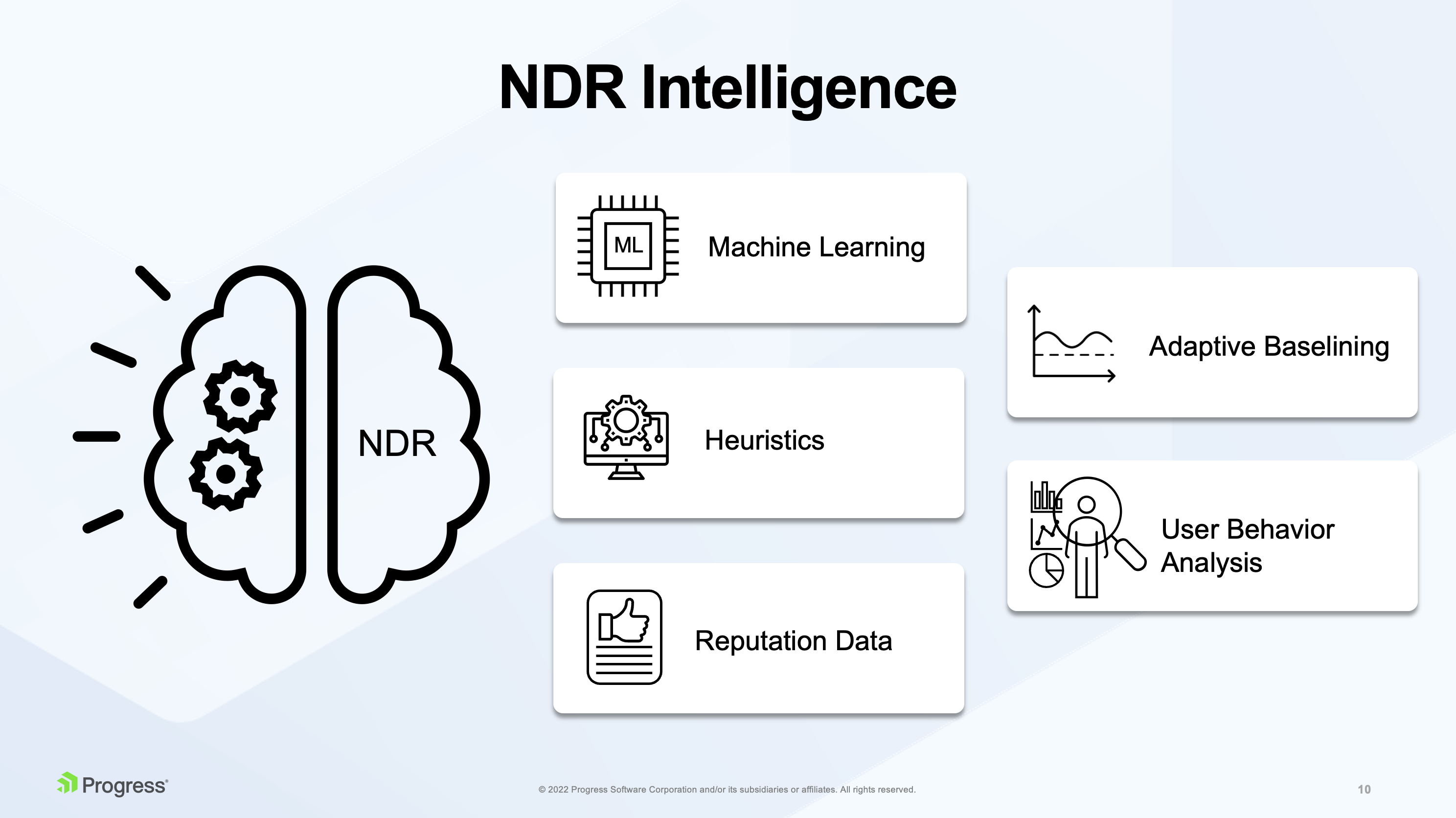
Machine Learning (ML)
Machine learning is the magic that continuously computes and analyzes entropy between individual communication parties in the network to distinguish human like and machine-like behavior. This way, NDR solutions detect different types of attacks against network services that demonstrate themselves with a very low entropy due to a repetitive pattern in the network that they generate. For example, if an attacker is doing a slow brute force attack (trying to guess your password) – ML can detect that.
Adaptive Baselining
Then we have something called adaptive baselining. This is not the baselining terms of statistical analysis of the whole data, but rather baselining of individual hosts, determining how they behave in the network and comparing behavior of individual hosts to one another. For example, you can detect that one host is generating much more emails than others in the same network, which may indicate some compromise, spam, or that something is exfiltrated through the DNS and so on.
Heuristic
Then we have heuristic algorithms that look for specific symptoms in the network and work with probability. For example, in peer-to-peer traffic you look for multiple different symptoms and calculate that there is, for example, an 80% probability that a specific device is probably plugged into some BitTorrent network and using BitTorrent download, which is something you don't want to see in the corporate environment.
User Behavior Analysis
Another example is analyzing user behavior. For instance, IT may know that a certain type of communication does not represent a legitimate pattern in the network. Let’s say someone tries to connect over and over to an SSH, suddenly connects and transfers lots of the data. This will be flagged as a potentially successful attack.
One customer of Flowmon, our NDR solution, detected a suspicious upload of data from a local network into the public data repository. This was hundreds of MB of data, and a specific station in the local network was identified as it source. The customer discovered an ex-employee was trying to backup company data.
Reputation Data
Many NDR vendors include open-source threat intelligence data in their offering to provide additional value. These can be commercial reputation feeds containing known malicious IPs, host names, domain names, JA3 fingerprints, etc.
Response
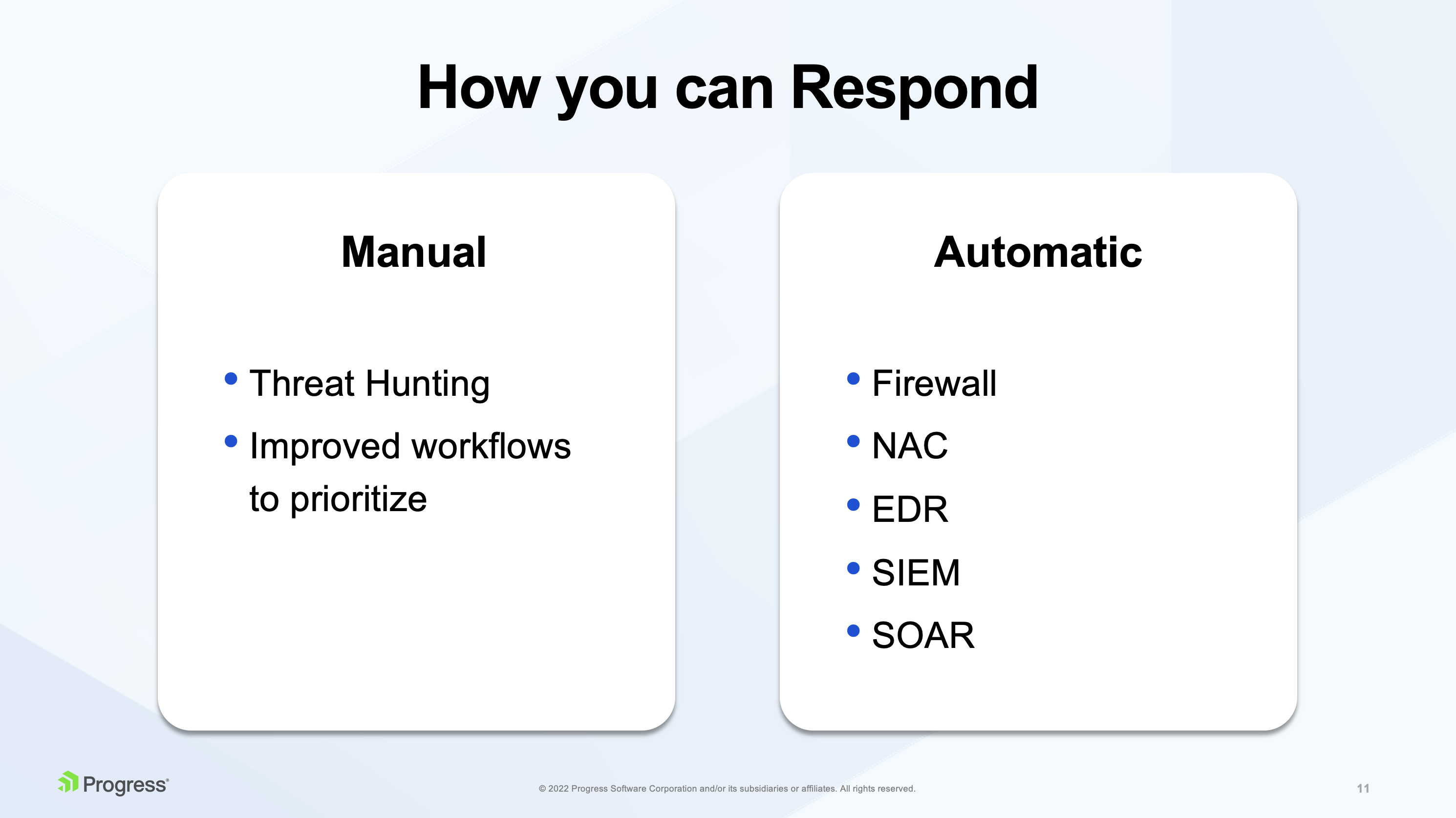
Response capabilities of NDR solutions can be divided into two groups – Manual Response and Automatic Response.
In their Market Guide for NDR, Gartner recommends deciding early on in the evaluation process if you require automated response versus manual response capabilities.
A clearly defined response strategy is valuable in selecting a shortlist of NDR vendors.
Manual
NDR solutions should provide a deep forensic investigation to help analysts understand advanced threats and attacks. Top NDR products also offer continuous packet capture (PCAP) for on-premises and cloud environments to provide the highest-fidelity evidence source available to investigators. NDR vendors are continuously improving workflow to prioritize events so analysts have everything at their fingertips to validate, triage and establish root cause, which allows them to drive rapid incident response.
For manual response, vendors improve their threat hunting and incident response functions by improving workflow features (for example, helping incident responders prioritize which security events they need to respond to first).
Automatic
For automated responses, NDR solutions focus on other complimentary security solutions to which it can automate a response. For example:
- FW - send commands to firewalls to drop suspicious traffic
- NAC(network access control) - send commands to the network access control (NAC) solution to isolate an endpoint
- EDR - EDR can be instructed by NDR to contain compromised endpoints
- You can send events detected by NDR to log management tools like SIEM
- or to SOAR, security operations automation response (SOAR) tools, where you can do event collection and correlation.
One More Framework – The MITRE Attack Framework
MITRE is a government funded research organization that was spun out of MIT. MTRE is also funded by NIST and has connections with government agencies (like CIA, FBI, NSA).
The framework is a blueprint of how threat actors use tactics, techniques and procedures to carry out an attack. It was originally developed to help provide a common language, common vocabulary and way of looking at things for not only vendors but also blue and red teams practicing against each other in cyber arena.
With MITRE, IT can pool resources and efforts to get ahead of potential threat actors. It also provides a useful way to play offense. It's not just about knowing the anatomy of an attack so that you can prevent it from happening, but pretending to be the attacker in a preparatory way. This way, IT can set up a robust infrastructure for dealing with threat actors and potential attacks in the future.
