Less noise, more comfort
We have redesigned the UI to feature more intuitive controls and to reduce information noise in results presentation.
The UI now shows only what is relevant. This means that the analysis status and results are shown as messages displaying the number of major issues if any are found. If not, the message tells the number of minor issues, and if no issues are detected, the message reads no findings.
Figure 1 - New UI and controls
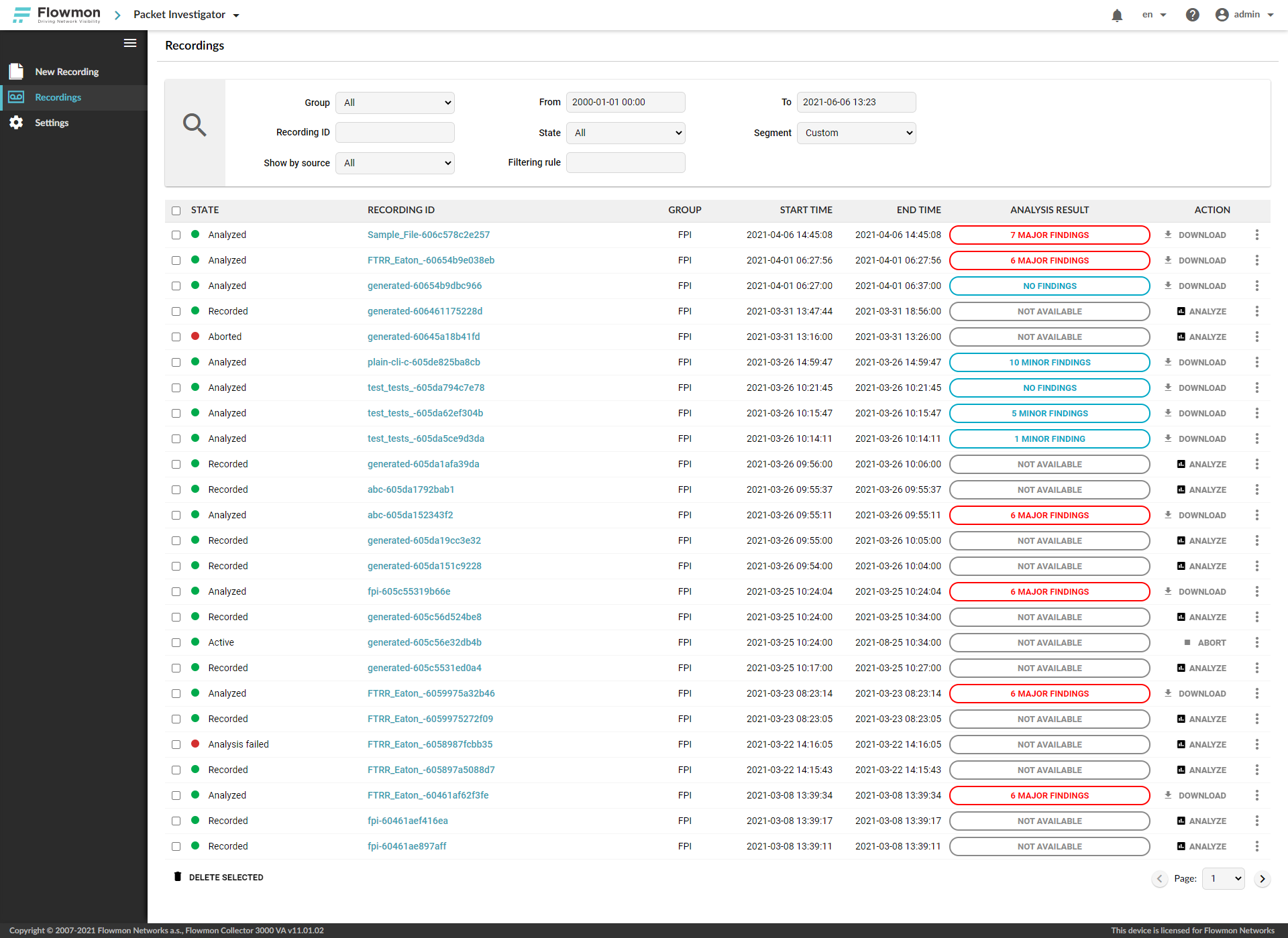
A status reading Not available means the recording has not yet been analyzed.
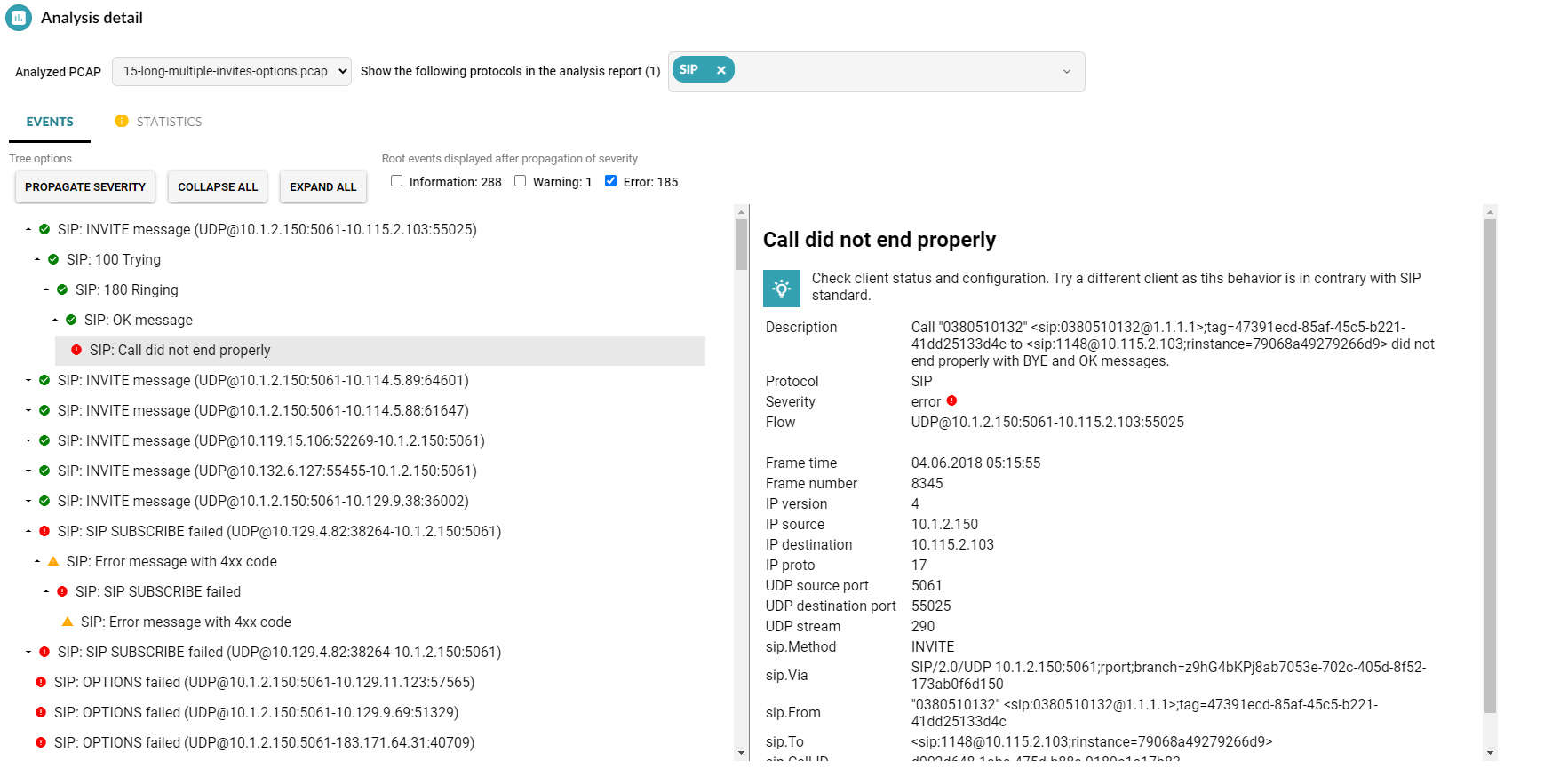
By clicking the message, you can access the full decision-tree results of the analysis.
Figure 2 – Full analysis detail (SIP protocol)
The Action controls follow a similar line as Analysis results, where only the command that is the most relevant to the stage of the analysis is displayed. You will see Analyze next to recordings that have not yet undergone analysis and Download next to those that have been analyzed. However, all these operations are also available from the context menu to the right at all times.
More scenarios, more context
The Packet Investigator’s analytical capability has been expanded by several new protocols. Besides industrial IoT protocols (CoAP, IEC104, GOOSE, MMS, and MQTT), these include ARP, ICMP, and NTP.
Specifically, ARP analysis can instantly recognize duplicate IP addresses in a local network, unsolicited ARP responses, or attempts to enumerate live hosts on the local network, which is useful for low level network diagnostics, investigating general connectivity or IP addressing issues, or tracing adversary activities within the network that were previously detected by Flowmon ADS.
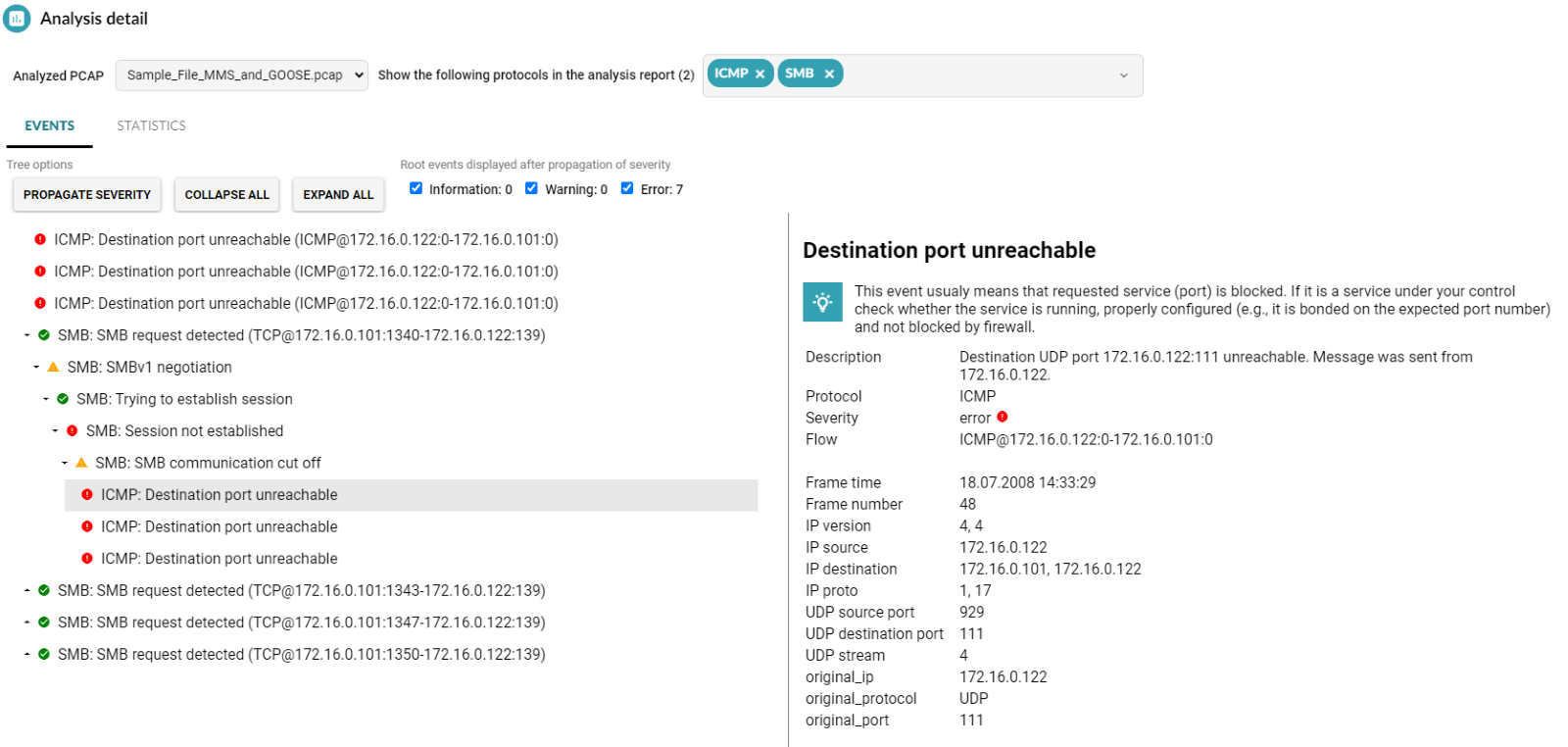
Similarly, delving into ICMP analysis may expose potential routing loops, unreachable parts of the network, badly configured MTU on network interfaces, or firewalls refusing to let traffic through. Analyzing the protocol can provide valuable context from the lower levels of the network protocol stack, such as the case in the figure below. It shows how a file-sharing issue over the SMB protocol can be traced to its root cause, in this case a blocked port on the server.
Figure 3 – SMB and ICMP protocol analysis
Lastly, the NTP protocol can be helpful for identifying the root causes of clock synchronization issues between devices and as a supplementary security tool that can analyze NTP amplification attacks captured in network traffic recordings.
Let the machine do the work
The Flowmon Packet Investigator 11.1 is a sterling example of a tool that combines automation, built in expertise, and a crisp user experience in one.
Do you have any feedback about the new version? Let us know!