FIPS compliant cipher suites hold the U.S. government's seal of approval, guaranteeing their suitability for federal systems. On the other hand, non-FIPS compliant cipher suites may present security vulnerabilities due to outdated cryptographic algorithms and potential lack of perfect forward secrecy. As a result, it becomes paramount to monitor TLS network traffic for non-FIPS compliant cipher suites. Doing so not only enhances security by identifying and blocking vulnerable suites, but it also ensures compliance with government regulations, mitigates risks of data breaches, and fortifies your organization's network against potential attacks.
Transport Layer Security (TLS)
Transport Layer Security (TLS) is a cryptographic protocol that is used to secure communications over the internet. TLS uses cipher suites to encrypt data that is transmitted over a network. FIPS compliant cipher suites are cipher suites that have been approved by the U.S. government for use in federal government systems.
There are a number of non-FIPS compliant cipher suites that are still in use today. These cipher suites are considered to be less secure than FIPS compliant cipher suites. This is because they may use older cryptographic algorithms that are more susceptible to attack. Additionally, some non-FIPS compliant cipher suites may not provide perfect forward secrecy, which means that if an attacker is able to compromise the encryption keys, they will be able to decrypt all past and future communications that were encrypted using those keys.
Why to monitor TLS network traffic for non-FIPS compliant cipher suites
There are several benefits to monitoring TLS network traffic for non-FIPS compliant cipher suites, including:
- Increased security: By identifying and reporting on non-FIPS compliant cipher suites, you can help to improve the security of your organization's network. This is because you will be able to identify and block non-FIPS compliant cipher suites, which will help to protect your organization from attack.
- Compliance: By monitoring TLS traffic for non-FIPS compliant cipher suites, you can help to ensure that your organization follows government regulations. For example, the U.S. government requires that all federal government systems use FIPS compliant cipher suites.
- Risk mitigation: By identifying and reporting on non-FIPS compliant cipher suites, you can help to mitigate the risk of data breaches and other security incidents. This is because you will be able to identify and block non-FIPS compliant cipher suites, which will help to protect your organization's data from unauthorized access.
Monitoring non-FIPS compliant traffic with Flowmon
Flowmon provides an easy way to monitor non-FIPS compliant TLS traffic by decrypting TLS traffic and inspecting the cipher suite that is used.
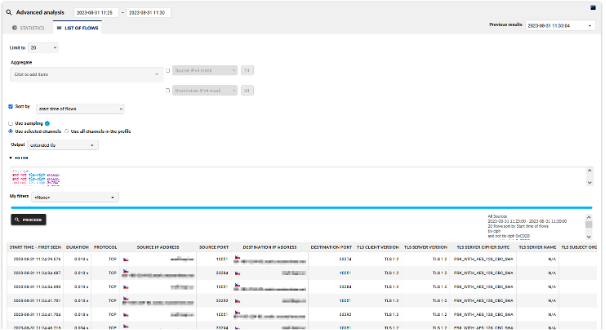
For one-shot review, navigate to Flowmon Monitoring Center -> Analysis page, analyze All Sources profile and filter for all TLS traffic using other than FIPS compliant cypher suites using the filter below.
tls-ciph
and not tls-ciph 0xC02B
and not tls-ciph 0xC02C
and not tls-ciph 0xC0AC
and not tls-ciph 0xC0AD
and not tls-ciph 0xC0AE
and not tls-ciph 0xC0AF
and not tls-ciph 0xC023
and not tls-ciph 0xC024
and not tls-ciph 0xC009
and not tls-ciph 0xC00A
and not tls-ciph 0xC02F
and not tls-ciph 0xC030
and not tls-ciph 0x009E
and not tls-ciph 0x009F
and not tls-ciph 0xC09E
and not tls-ciph 0xC09F
and not tls-ciph 0xC0A2
and not tls-ciph 0xC0A3
and not tls-ciph 0xC027
and not tls-ciph 0xC028
and not tls-ciph 0x0067
and not tls-ciph 0x006B
and not tls-ciph 0xC013
and not tls-ciph 0xC014
and not tls-ciph 0x0033
and not tls-ciph 0x0039
and not tls-ciph 0x00A2
and not tls-ciph 0x00A3
and not tls-ciph 0x0040
and not tls-ciph 0x006A
and not tls-ciph 0x0032
and not tls-ciph 0x0038
and not tls-ciph 0x00A4
and not tls-ciph 0x00A5
and not tls-ciph 0x003E
and not tls-ciph 0x0068
and not tls-ciph 0x0030
and not tls-ciph 0x0036
and not tls-ciph 0x00A0
and not tls-ciph 0x00A1
and not tls-ciph 0x003F
and not tls-ciph 0x0069
and not tls-ciph 0x0031
and not tls-ciph 0x0037
and not tls-ciph 0xC02D
and not tls-ciph 0xC02E
and not tls-ciph 0xC025
and not tls-ciph 0xC026
and not tls-ciph 0xC004
and not tls-ciph 0xC005
and not tls-ciph 0xC031
and not tls-ciph 0xC032
and not tls-ciph 0xC029
and not tls-ciph 0xC02A
and not tls-ciph 0xC00E
and not tls-ciph 0xC00F
and not tls-ciph 0x1301
and not tls-ciph 0x1302
and not tls-ciph 0x1304
and not tls-ciph 0x1305
Source of the cipher suite list, used in the filter: NIST SP 800-52 Rev. 2 - Guidelines for the Selection, Configuration, and Use of Transport Layer Security (TLS) Implementations.
To get better insight into TLS traffic in the list of flows you can choose extended-tls output, which presents TLS specific fields like TLS Client/Server version or TLS Cipher Suite.
If you're interested in permanent monitoring, define a new Profile on the Profiles -> Edit Profile page in FMC by using filter above in your profile channel filter.
