Data from multiple cybersecurity industry sources show that insider threat incidents are a major risk now and will remain so in the future. One survey reported that two-thirds of organizations consider insider threats more of a risk than external hackers. A third in another survey said they had an insider threat incident during the previous year. Another significant risk was getting compromised by an insider in a trusted business partner in the supply chain. A fact that shows that the surface for insider threats does not end at your network border.
What is an Insider Threat?
An insider threat is any malicious activity, like a data breach or the deployment of malware, performed by someone who has legitimate access to IT systems. People need access to systems at the appropriate level to do their jobs. Access will range from limited at one end to full administrative access at the other (although this level of access should be toughened with privileged access management that requires multiple authorizations in a workflow). People who have access to IT systems and who therefore are potentially an insider threat include staff, former staff who still have access, contractors, third-party staff who perform functions on or via the IT systems, and people in supply chain partners who have access to linked IT systems that deliver business functions. Insider threat refers to risks from deliberate malicious actions plus unintentional incidents due to human error. This latter class of insider threat accounts for more than half of all reported incidents of this type. People make mistakes. This is a fact of life, and organizations must build cybersecurity strategies with this fact at their core.
For incidents not due to human error, there are several reasons why trusted staff go rogue and cause harm. They include financial gain by selling the stolen data on the dark web or via a bribe paid to them by cyber criminals to introduce their attack tools to a PC on the network. Settling a score due to a perceived slight is another reason staff turn against the organization. This risk is especially acute when layoffs occur. For organizations in strategic sectors of the economy, espionage is another significant reason for insider threats. This espionage can be from foreign governments or competitors with lower scruples than expected and can be used to steal intellectual property or cause malicious damage. A recent high-profile espionage story that probably comprised both state and competitor advantage aspects was this Apple car project case.
Insider threats are now a fact of life in the digital-first world, so monitoring networks and systems to detect anomalous activities is crucial. And a core part of daily IT operations. But it comes with challenges.
Challenges of protection strategies
Modern IT networks and the systems that use them are complex. Many of the activities that insiders use when undertaking malicious activities are hard to separate from normal day-to-day business activities. Detecting them requires a blended approach that uses processes and technologies. For the former, plenty of processes and frameworks are available to learn from and implement to bolster security against insider and external threats. Flowmon can help deliver the protections needed by GDPR, as outlined in this article.
When deploying technologies to help protect networks and systems, it's worth noting what Gartner says on the topic of insider threats: "Most organizations have limited technical resources to devote to an insider threat program and are constrained in the types of data they can proactively collect and analyze for insider threats."
Source: Best Practices for Managing Insider Security Threats. It is from 2016, but the sentiments are still relevant. Flowmon solutions can plug this gap in technical resources that most organizations face.
Flowmon Detection of Insider Threats
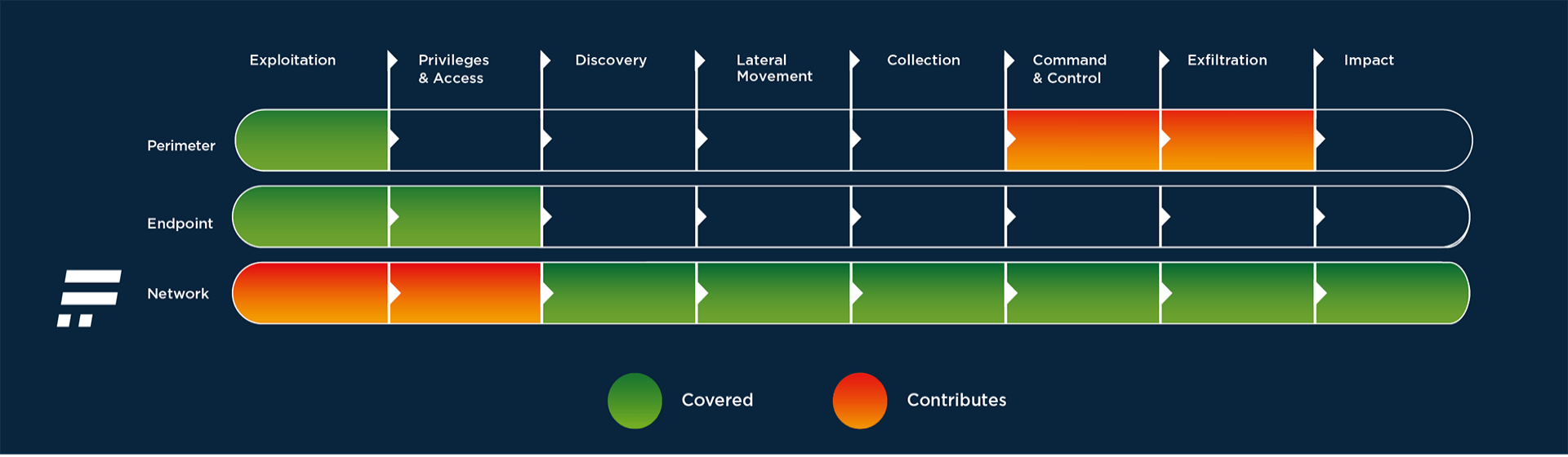
Detecting insider threat activity within regular activity on the network requires a layered strategy that stacks multiple monitoring points to provide an overall view and to detect anything that is a deviation from the normal. Flowmon monitors the entire network, closing any gaps between the perimeter, endpoints, and accounts. The following diagram outlines where Flowmon solutions provide protection as a typical cybersecurity incident progresses. Green segments are fully covered, and orange segments are where Flowmon contributes to the overall security posture alongside other essential tools that organizations should be using.
The Flowmon solution uses several techniques simultaneously to pick up anomalies and recognize them as indicators of compromise. It uses these techniques:
- Machine learning
- Adaptive baselining
- Heuristics
- Behavior patterns
- Reputation databases
- Signature-based detection
When suspicious behavior is detected, the administrators get provided with immediate insights via alerting and also get data for a thorough post-compromise analysis. Using Network Detection & Response (NDR) and implementing the SOC Visibility Triad enables uncovering of insider threats, provides comprehensive incident understanding, significantly cuts incident resolution time, and limits the damage that a malicious insider or a tricked staff member can cause.
You can read much more on how Flowmon can help you detect, respond to, and reduce your risk on our dedicated Detection of Insider Threats page.
Significant Examples
How can an insider threat impact your organization? Here are a few high-profile cybersecurity incidents and data breaches resulting from an insider threat.
1. Third-Party vendor compromised - The Marriott Data Leak
In January 2020, attackers used a third-party application that Marriott used to provide guest services. The attackers gained access to 5.2 million records that included contact details (name, mailing address, email address, and phone number), additional personal details (company affiliation, gender, birthday details), loyalty account information (account number and points balance, but not passwords), partnerships and affiliations (linked airline loyalty programs and numbers), and saved guest preferences (stay/room preferences and language preference). Not all 5.2 million records had all this information, but the breach was significant and leaked a lot of personally identifiable information. The attackers had access until the end of February 2020, when Marriott IT staff noticed the suspicious activity and stopped the access from the third-party application. So they had access for up to two months, during which they could exfiltrate data. Marriott had to pay an £18.4 million (€21 million) fine levied under GDPR.
The suspicious activity and data exfiltration that was in progress over the time the attackers had access could have been flagged much earlier with a modern network anomaly detection solution in place.
2. You have been socially engineered - The Sony Pictures case
Email phishing is the most exploited way that attackers target organizations and trick users into making a mistake that leaks data or provides them with unauthorized access. A well-known example of a successful phishing attack compromised Sony Pictures systems in 2014. This resulted in the release of hundreds of emails that included discussions of famous actors, and it also highlighted a significant pay difference between male and female stars in the same movies. As a result, there was widespread coverage of the breach in the general press.
The threat from phishing and other social engineering attacks has increased since the 2014 Sony breach. All organizations must protect against a member of their staff getting tricked by attackers into providing a means to bypass security.
Flowmon can provide this protection in several ways:
- Use the BLACKLIST functionality in the solution. This prevents communications and traffic from known phishing pages, malware sources, or Command & Control domains that attackers use.
- Malware detection on systems. If a device gets infected with malware Flowmon detects other indicators of compromise. Malware will most certainly perform some of the following actions detectable by Flowmon ADS:
- "Calling home" - to the C&C server, sometimes via direct internet communication.
- Reconnaissance scanning and lateral movement - port scanning, later also trying brute force on passwords to gain control or spread malicious code.
- Data exfiltration - detect and block unusual data movements that are flowing on and out of the network.
- Use Flowmon BPATTERNS (Behavior PATTERNS) to define custom protection rules. Flowmon provides a selection of BPATTERNS to monitor for known threats, and we regularly release updates and new rules. You can also create your own to monitor any unique data or systems on your network.
3. Attackers among us - The Korea Credit Bureau case
When people are unhappy in a job, they sometimes quit. When they leave for a new job, some people take their email, contact lists, or other confidential data. Or worse - in 2014, a disgruntled employee of the Korea Credit Bureau (KCB) stole 20 million credit card records and sold them to marketing companies.
Some staff leak data even when they are not leaving a job. Whatever the reasons, monitoring user activity at a network level is crucial to spot unusual data movements. Data leakage is commonly seen when data gets uploaded outside the network, which you can easily catch with anomaly detection.
But more sophisticated breaches and leakages also exist where you need some advanced behavior analysis intelligence. These often get used by IT staff who know how the technologies work. But they are also used by cybercriminals who have gained a foothold on a network.
Flowmon can detect "covered channel" communication where a data payload gets sent over unusual protocols that regular traffic filtering systems overlook. By looking at the characteristics of user traffic, we can see a payload sent via the ICMP protocol normally used for signaling and thus should consist of packets with a small size. Flowmon also detects DNS tunneling. If a device does not have direct access to the internet, all that an attacker needs is access to at least one internal DNS server that can reach an external DNS and a Command & Control domain as a communication partner. Using regular DNS functionality and legitimate servers, the compromised device and the C&C domain can establish a two-way communication and exchange text messages encoded into the DNS query.
4. Policies do not apply to some people – The Target case
Access authorization can be lax in many organizations. When it is people who should not have access to certain systems frequently do. Or they should be blocked from accessing certain systems from unsecured devices or external networks. Gartner calls these employees “Goofs”. They know they should not connect to critical systems from unsecured networks and computers. Or should not perform any changes which have not been approved. Sometimes they need to carry out a pressing task while under the pressure of time. Sometimes they are lazy, but they never have any bad intentions. How can they be differentiated from a real attacker? How can their malicious behavior be visible on the network? They could be using peer-to-peer communications as well as VPN tunnels, bypassing the proxy server, or using anonymizers, such as TOR, to connect to the Dark Web. Target fell victim to this insider threat that resulted in scrappers getting installed on their point-of-sale terminals—allowing hackers to siphon off transaction data as staff scanned cards at checkouts.
These are all standard off-the-shelf detection capabilities of Flowmon ADS. By using Flowmon Probes, we even gain application-level visibility into many protocols, and we can also carry out full packet capture and analysis. For more details, check out dedicated product page of Flowmon Packet Investigator.
Conclusions
Processes or technologies can never bring a complete level of security, so the rule of thumb here is to create the most effective combination. Educate your employees, control their access, log their activity, and detect breaches and anomalies with Flowmon technologies that deliver rapid detection and allow you to respond in the most appropriate manner.
