Why your IT Infrastructure Monitoring Isn’t Enough
IT Infrastructure Monitoring (ITIM) tools like Progress’s own What’s Up Gold are the backbone of any IT Operations monitoring strategy. However, these tools are primarily focused on general purpose visibility across a wide range of infrastructure and systems with an emphasis on operational availability and performance. When it comes to modern day attacks they can often show there’s a problem but don’t have the insight into the nature of the threat and the root cause that will allow you to respond.
Let’s imagine a scenario where you’re experiencing a Denial of Service (DoS) attack using a SYN flooding technique. This is a relatively low volume attack that may not even trigger your network utilisation alarms and is often used to obfuscate more target and dangerous attacks.
Below we can see how this attack appears using basic server performance telemetry. We have a warning for a single CPU core on one of the servers but in general this doesn’t look like very threatening or in danger of impacting user experience. Depending on other priorities and the organisational processes we may choose to just monitor this and wait to see if it escalates before we take any action.
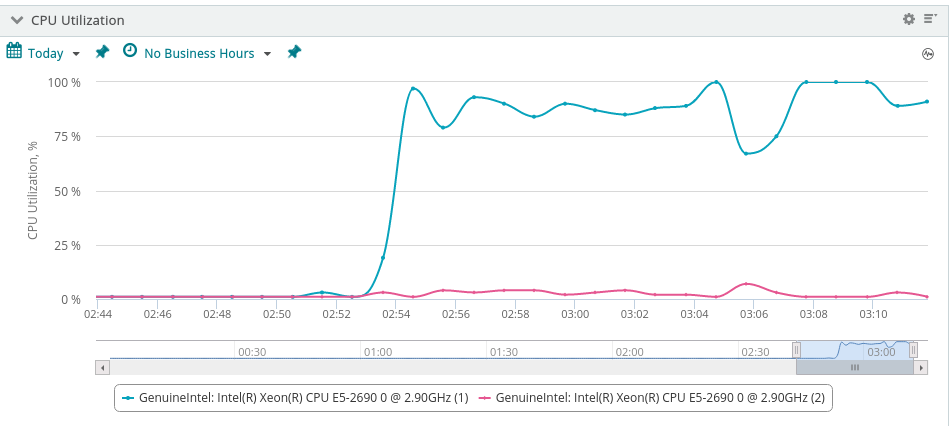 Figure1:
High
Utilisation of a Single CPU Core
Figure1:
High
Utilisation of a Single CPU Core
How Flowmon ADS Helps
Flowmon ADS implements multiple techniques and methods to detect threats using network telemetry and is an example of Network Detection & Response (NDR) technology. As an attacker attempts to scan for and exploit vulnerabilities in your systems as well as access and exfiltrate data all of it shows up on the wire at some stage. Flowmon ADS gives you detailed insight into every action an intruder takes.
When we look at the same DoS incident from the perspective of Flowmon ADS we can easily trace our way from a top-level even down to details attack and root cause information.
Using the built-in Flowmon integration with What’s Up Gold we can easily see a security event summary dashboard to alert us that there’s more going on than just the DoS attack.
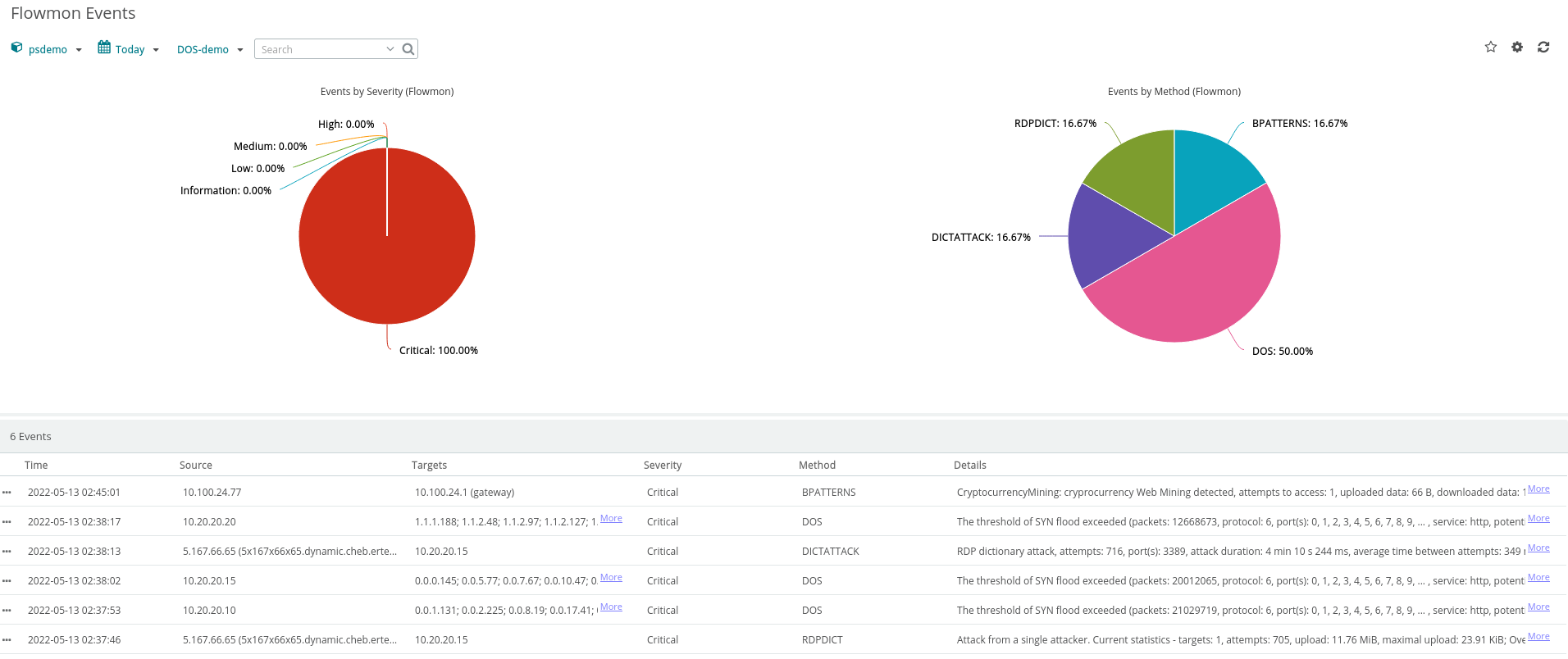
Figure 2:
Flowmon
ADS Integrated Events Dashboard in What’s Up Gold
From here we can immediately jump to the Flowmon ADS console to see more detailed information such as exploit and vulnerability details. The first important detail is the identification of the Bluekeep RDP vulnerability as the original entry point on to the server by the attacker. This attack was launched under the cover of the DoS attack, hoping it would distract us and hide the more targeted exploit. This is the root cause we need to mitigate by ensuring all our servers are properly patched.
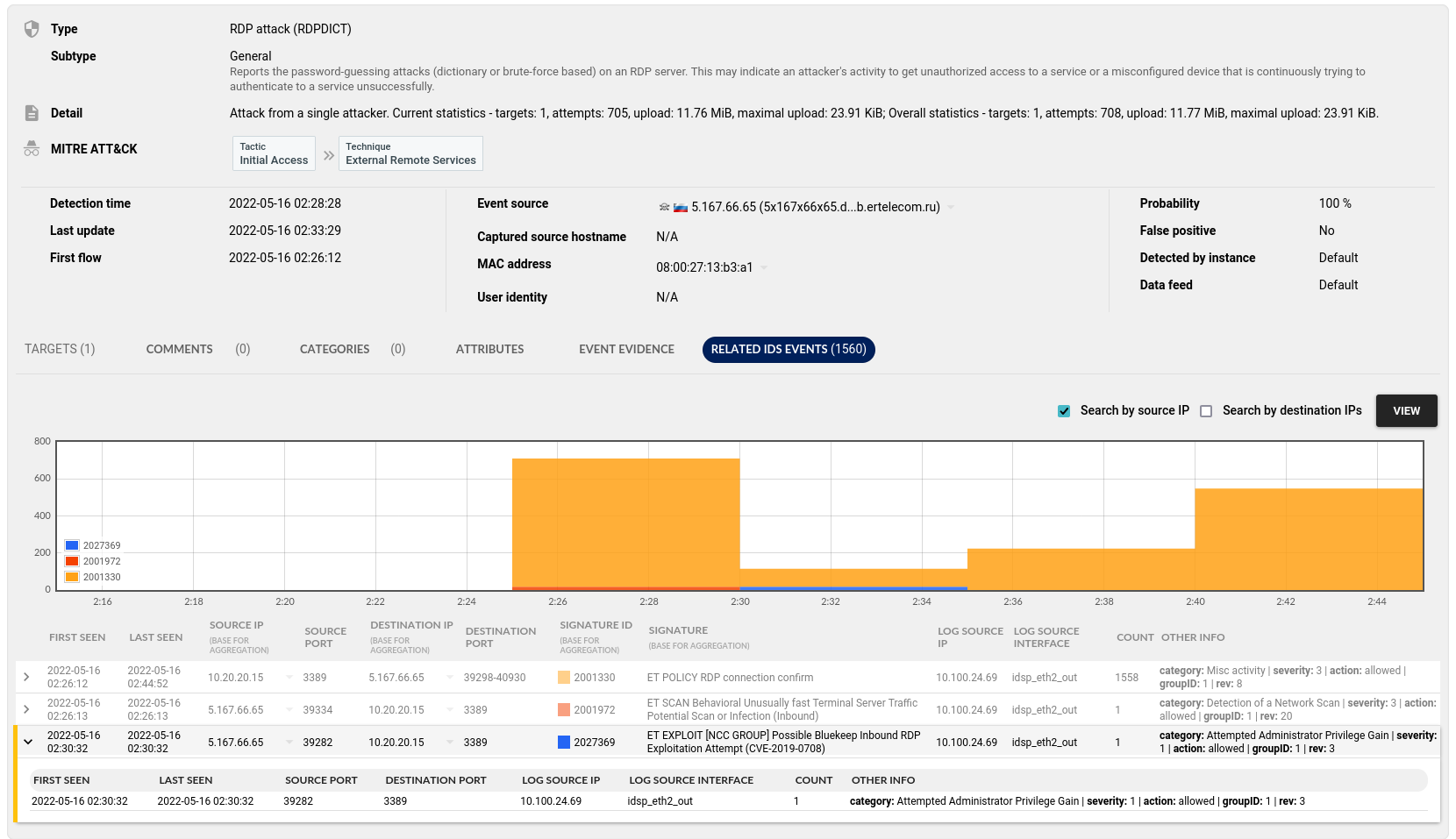 Figure 3:
Bluekeep
Vulnerability Event Details
Figure 3:
Bluekeep
Vulnerability Event Details
Next we inspect a related event from the web server experiencing increased load on one of it's CPU cores. It would be easy to dismiss this CPU load as a result of the DoS traffic however we can now see it’s the result of a crypto-currency mining program being run by the attacker. While the impact of this is largely financial (increase resource consumption, etc) the attacker has gained full administrative access to our server in order to plant this program. Much worse could be yet to come.
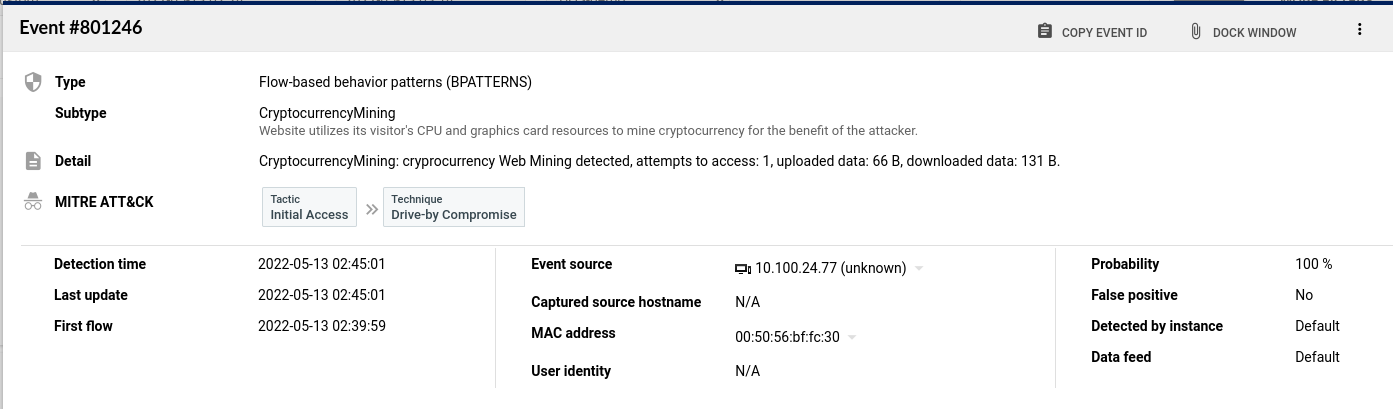 Figure 4: Cryptocurrency Mining Event
Figure 4: Cryptocurrency Mining Event
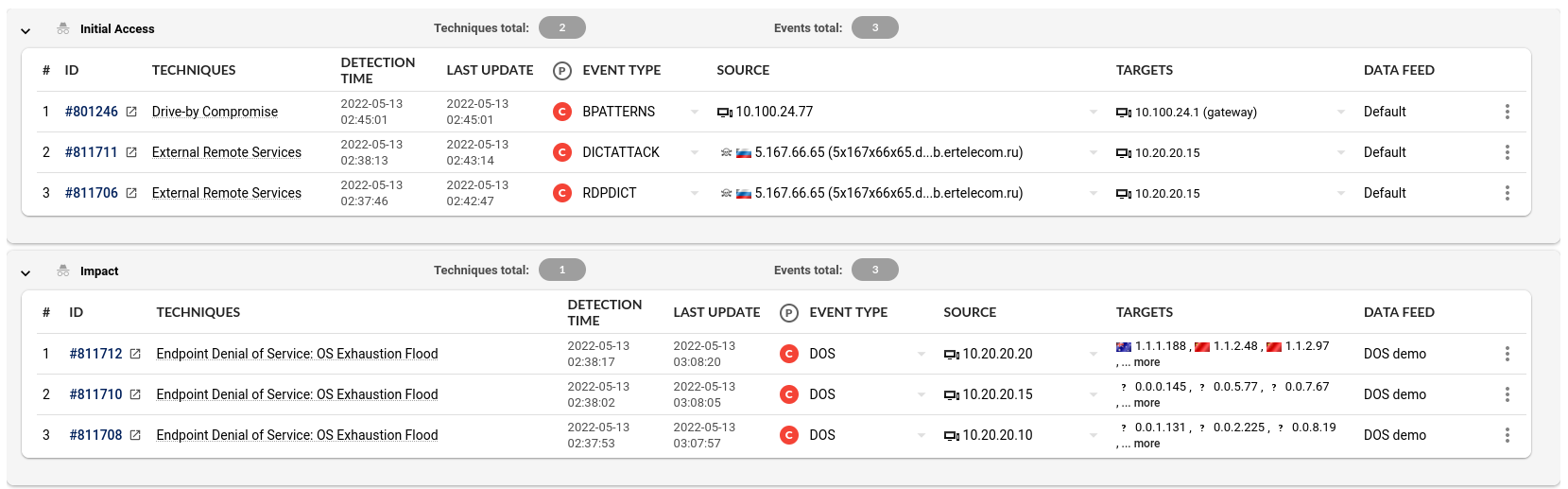
Finally we can see the whole incident in the context of the MITRE framework and how each of the various events from DoS to Bluekeep Exploit to Cryptocurrency Mining are tied together as progressive steps in a single attack.
Summary