Two different technologies are serving same purpose - to troubleshoot network related issues to IT professionals. Packet capture is well known for helping experienced network administrators of large enterprises for many years. The question is: "Can flow technologies do the same?" Well it depends. Talking about traditional L3/L4 sampled NetFlow answer is obvious: "No, it simply cannot." On the other hand, new flow monitoring standard IPFIX with L7 visibility can. Even Gartner claims since 2013 that flow analysis can handle around 80% of troubleshooting tasks while packet capture will help with the rest more advanced 20%. By enriching traditional flow statistics with application layer (L7) visibility, flow analysis can handle up to 95% of troubleshooting tasks.
Let's take one troubleshooting case as an example. User claims that he is not able to connect to his application running at services.invea.com and is not receiving updates at all. He provides indicative time slot and his IP address 192.168.222.87.
Troubleshooting using packet capture
I have my packet analyzer with continuous capture in place. So let's hope that my ring buffer still keeps the data I need. Thankfully we can download the PCAP containing traffic of IP address 192.168.222.87 and open the traffic in Wireshark.
Figure 1: Captured network traffic analysis in Wireshark.
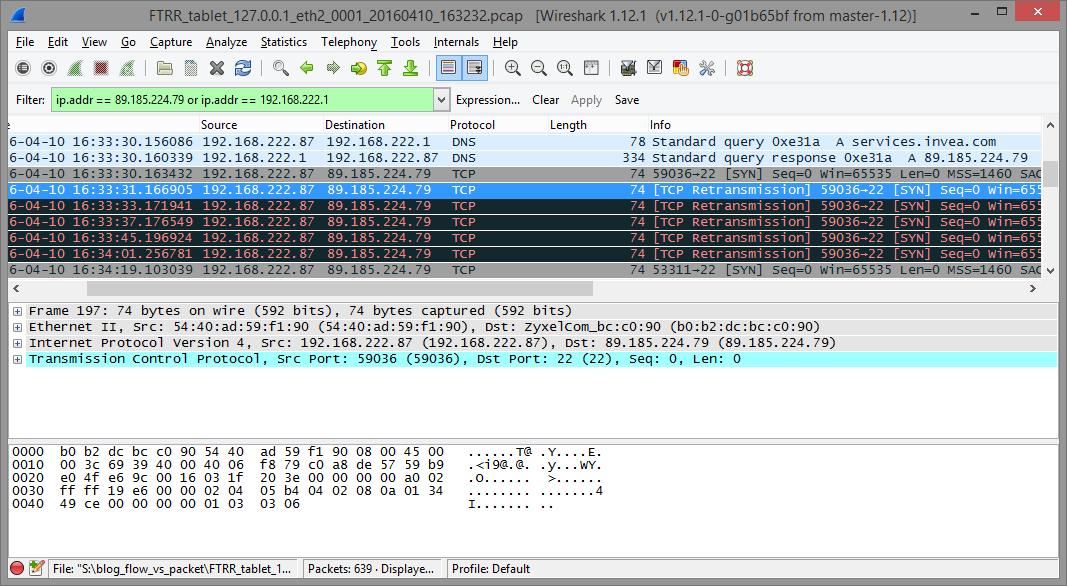
On picture above we can see the communication between user and services.invea.com. Domain services.invea.com is resolved correctly to IP address 89.185.224.79, but after DNS response was received, user tried to establish TCP session with no response from the external IP address. We have to check our firewall settings if this communication is allowed.
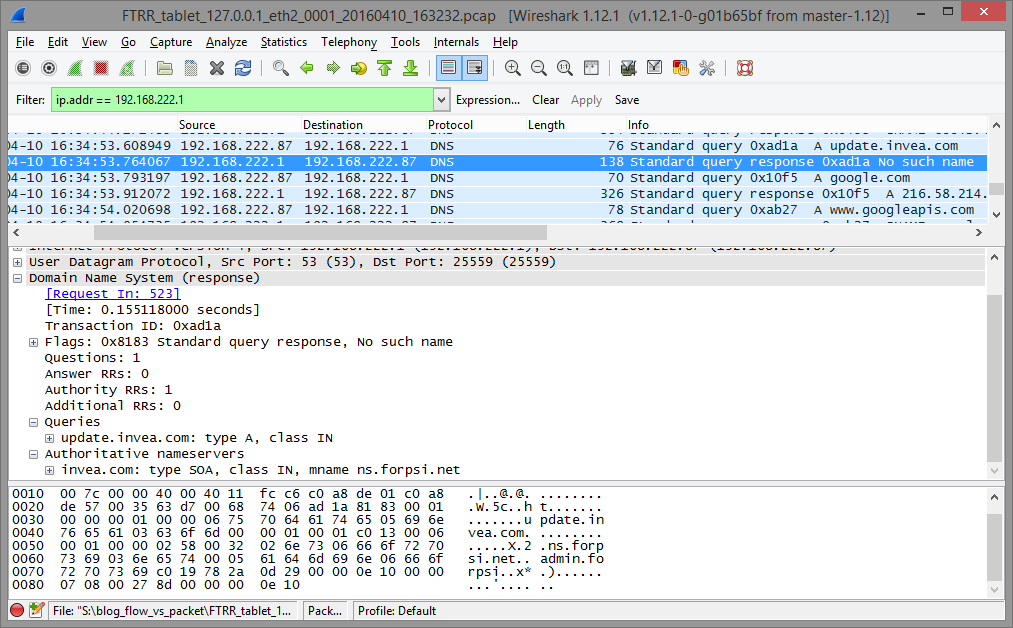
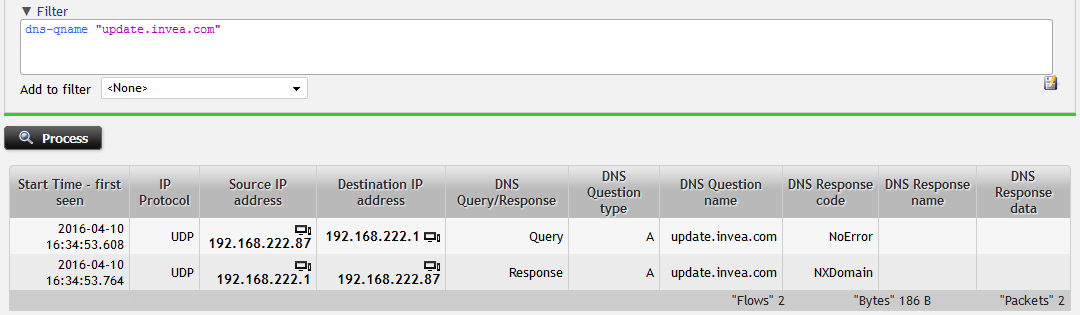
Second issue is related to non-existent domain queried by the user machine. We can see that update.invea.com does not exist which probably implies wrong configuration of the user and not a network related issue.
Figure 2: Host queries to resolve non-existent domain.
Troubleshooting using flow data with application layer visibility
I have Flowmon Probes in place monitoring network and Flowmon Collector with weeks of history of un-sampled and non-aggregated traffic statistics. So I can directly ask about DNS question to domain services.invea.com.
Figure 3: Filtering in DNS traffic – flow statistics enriched with DNS information.
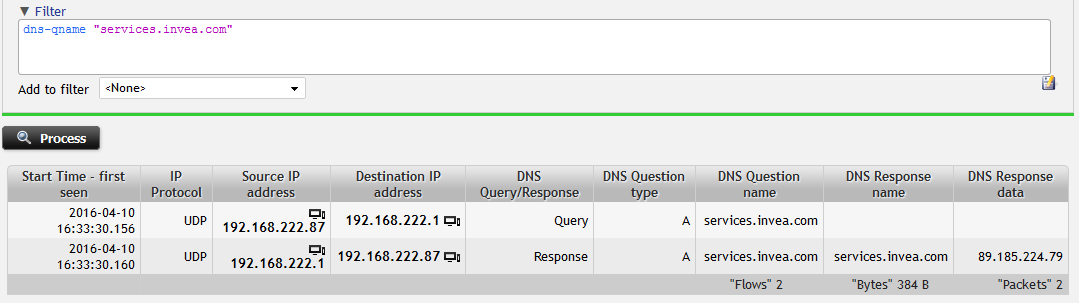
I can see the IP address provided by DNS server as response and check for the traffic going to that IP address easily. It is possible due to the fact that flows from the Probe corresponding to DNS are enriched with most important L7 information from DNS protocol.
Figure 4: Filtering user's communication with external service. Host is not recieving any response.
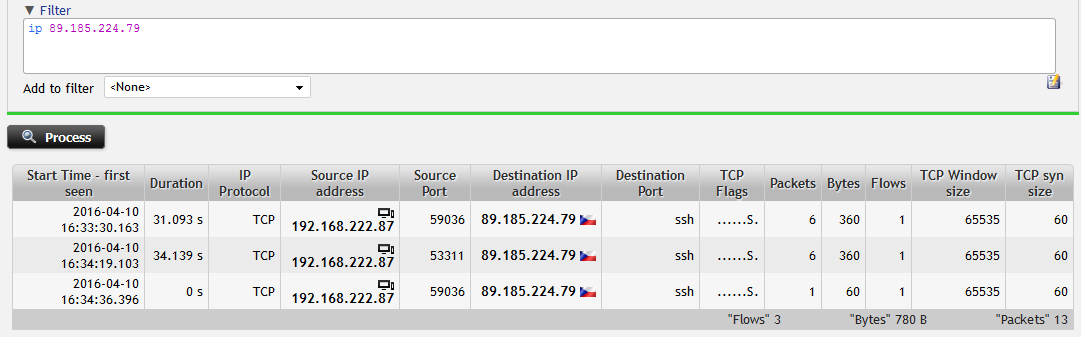
I see that only SYN packets are being transmitted to the network without any response from external IP address which implies the need to check firewall rules. In addition to common L3/L4 information I have the visibility into TCP specific items like default TCP segment (window) size which can help me to troubleshoot TCP session.
The non-existing domain is in my flow evidence as well. Domain update.invea.com does not exist which means that DNS server replies "NXDomain".
Figure 5: Filtering in DNS traffic – searching for NXDomain DNS Response Code.
Giving up the capturing capabilities
When you move towards flow visibility you don’t have to give up on packet capture capabilities. With Flowmon Probes and Traffic Recorder module you still have the capability to run on-demand packet captures and generate PCAPs when needed from more detailed visibility and analysis. And you can still use your favorite tool like Wireshark or any third-party commercial analyzer as you receive your PCAPs in standard format.
Conclusion
We have demonstrated a use-case where flow data with extended visibility are equally powerful to full packet capture and packet analysis. However, there are several differences. With flow data I can do the same on 1G, 10G or even higher speeds easily and still keep reasonable history of full non-aggregated flow data to analyze network related issues. Just compare that with the sizing (and pricing) of capture appliance equipped with rolling buffer to give you 24 hours of full history on a 10G backbone. Flows are afforable even for SMB, easy to deploy and easy to use. On the other hand, it is fair to say that even with extended flow level visibility you still might face issues where analysis of PCAPs is unavoidable. We in Flowmon Networks believe that merging flow and packet level visibility into one versatile solution is the technology that will help us to scale to future performance and capacity needs. So let's do continuous flow monitoring and packet capture when needed. At the end of the day you will most probably need to analyze PCAPs less than you've expected.
Get the insight with Flowmon. Try out the Flowmon Live Demo or free TRIAL and stay in touch for further information on our products!
