The previous integration with Fortinet describes a way of stopping the attacker at the perimeter. The following use case is largely the same, except with a Check Point firewall instead.
Simulation of the automated attack defense
An attack has been simulated and is publicly accessible with more details on Flowmon Youtube channel:
Script setup
The integration uses Check Point (API) for contacting the firewall. Calling the firewall API once the Flowmon ADS detects a threat requires having the script set appropriately.
Therefore, correct input parameters of the script are necessary for the connection to be successful.
Figure 1 – Script configuration dialog in Flowmon ADS
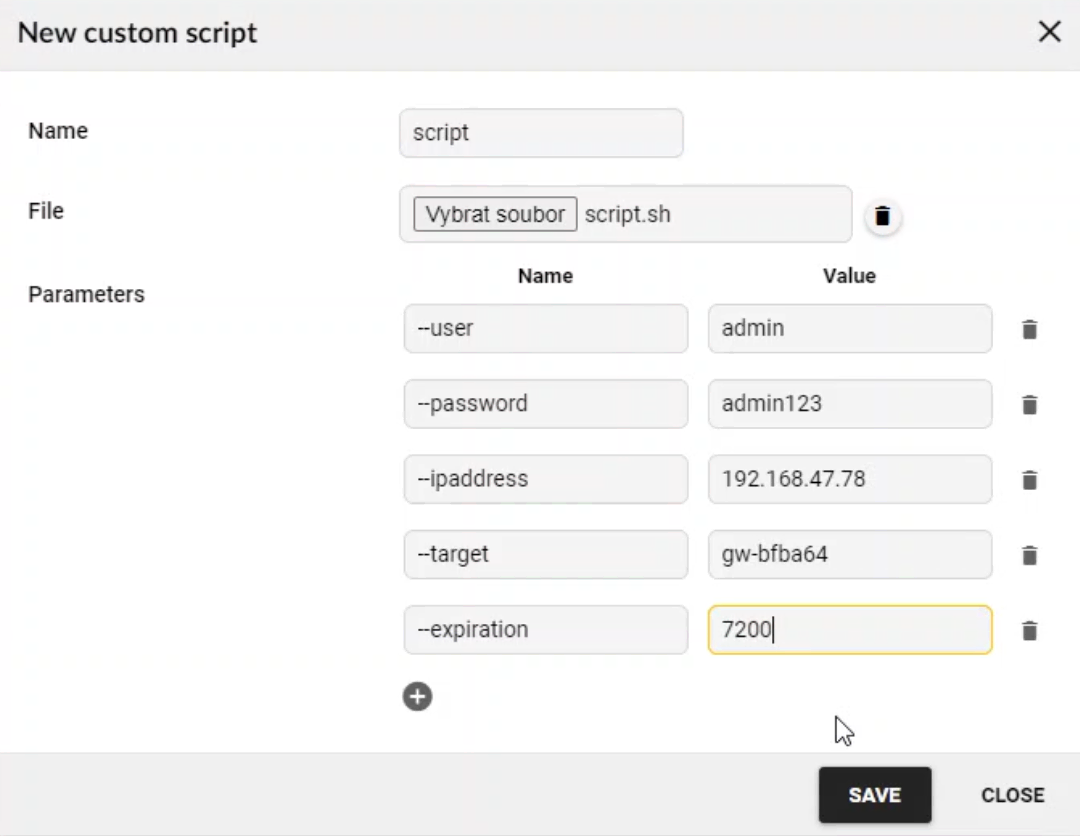
To instruct the ADS when to trigger a script, we use a feature called Perspectives. Perspectives are designed to prioritize detected events and control subsequent actions such as user notifications, triggered packet capture, or active response using integration scripts.
Figure 2 – Script configuration dialog in Flowmon ADS with additional settings

With the above script settings in place, your integration should be ready to perform automated blocking according to the set criteria.
Network topology
To demonstrate the functionality of the integration, consider the following scenario.
Let’s simulate a case under network 192.168.47.0/24 where an attacker performs a vertical scan against the victim. Default Gateway of the attacker is amended to reach the Check Point firewall first.
Figure 3 – Sample network topology scenario

Attack recognition and automated blocking
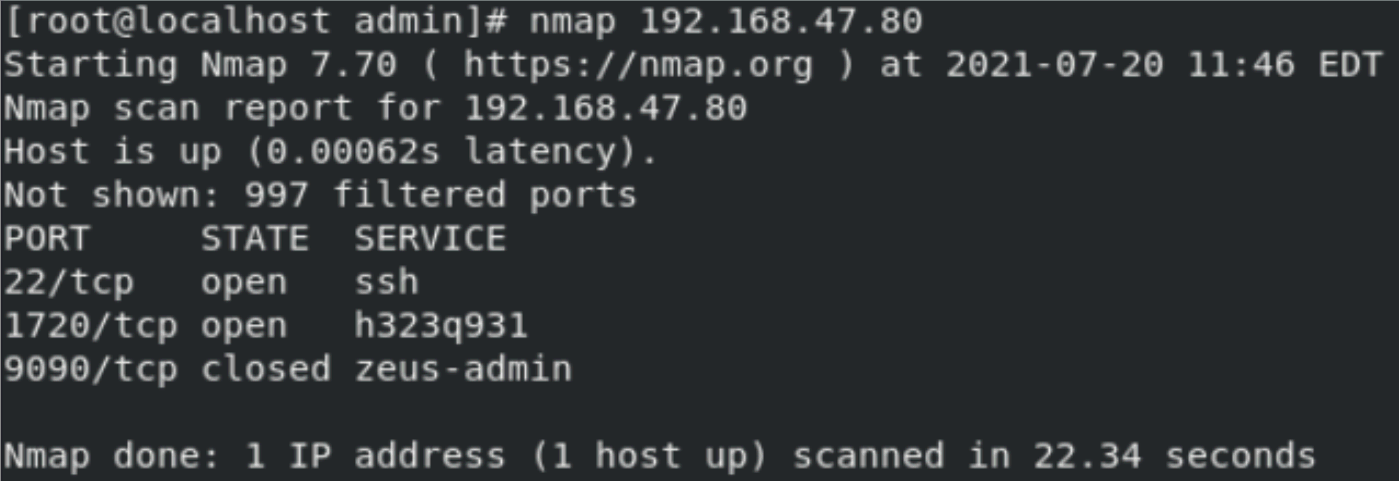
A scan targeting a host with the IP address of 192.168.47.80 has occurred in the network. The attacker with the IP address of 192.168.47.77 is using the Nmap utility to send numerous TCP SYN packets.
Figure 4 – TCP SYN flood as part of the Nmap scan
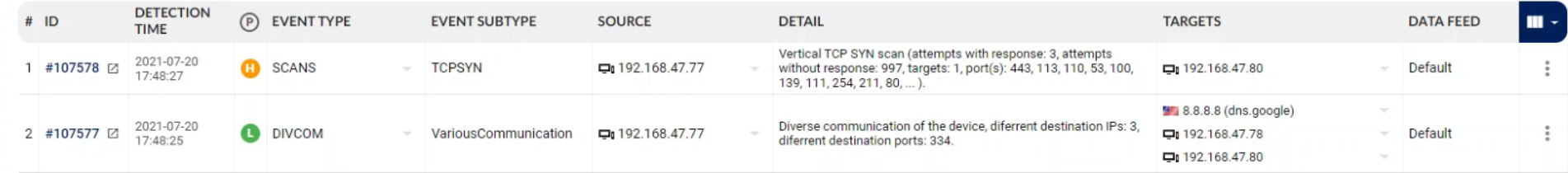
Since all the network communication is mirrored into a Flowmon appliance, malicious activity is detected by Flowmon ADS using the Behavior Patterns approach. Two method events are reported, namely SCANS and DIVCOM.
Figure 5 – Security events in ADS UI indicating the attacker’s scanning activity
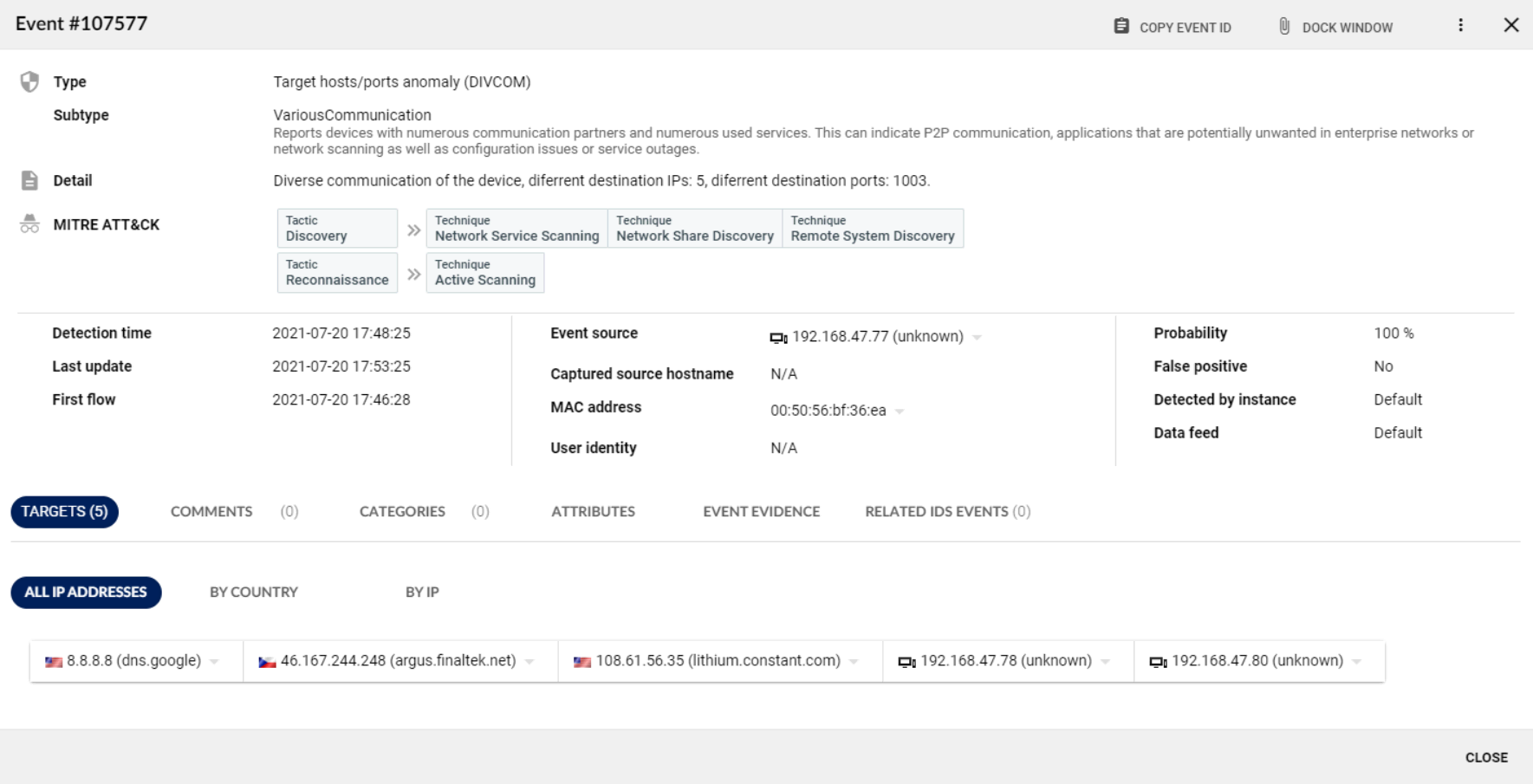
Both methods are classified under the MITRE ATT&CK framework and reported in the event description as Discovery and Reconnaissance Tactics and Network Service Scanning, Network Share Discovery, Remote System Discovery and Active Scanning Techniques.
Figure 6 – Detail of the SCANS even
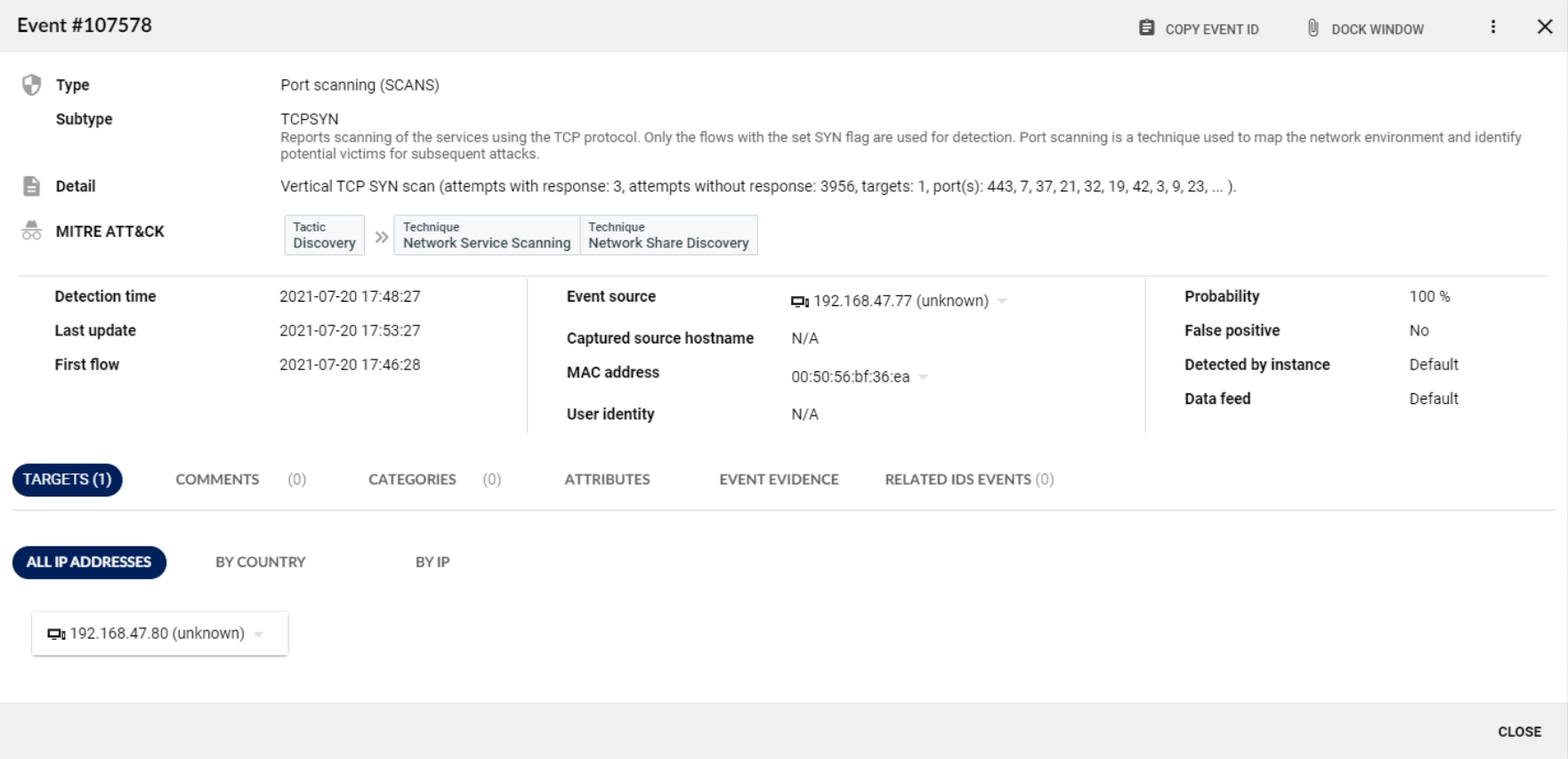
Figure 7 – Detail of the DIVCOM event
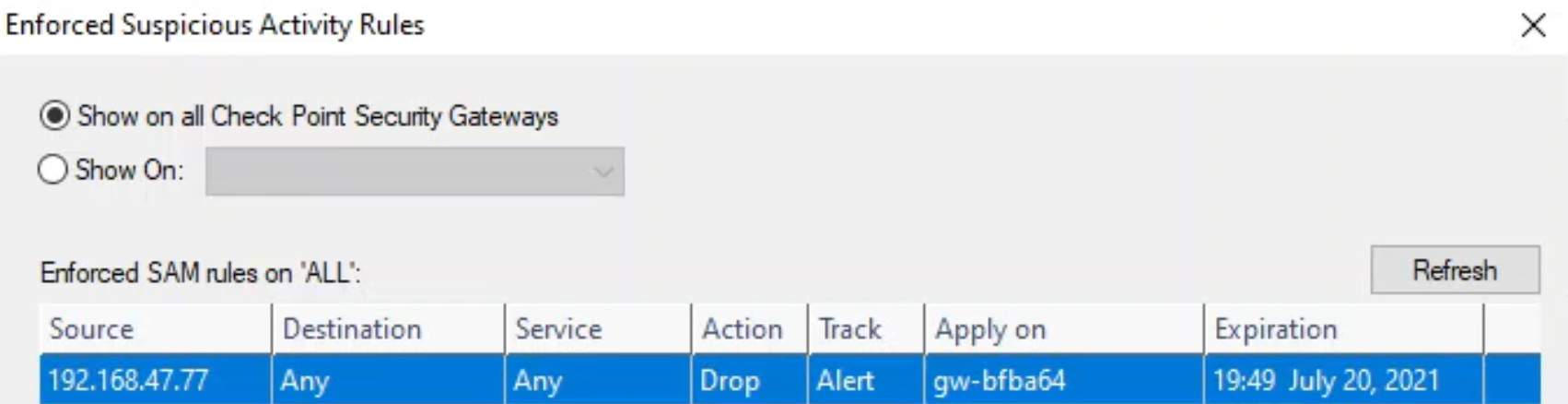
As soon as the ADS event is triggered, Flowmon runs the script, which puts the source IP address into the quarantine on the firewall. The blocking was implemented using Suspicious Activity Monitoring rules, and is displayed in the Check Point SmartView Monitor.
Figure 8 – SmartView Monitor showing a quarantined IP address
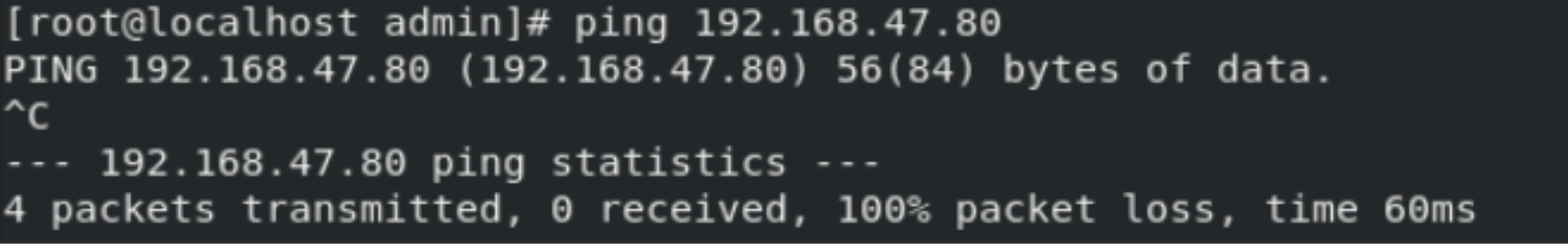
As the default gateway of the attacker has been amended, the IP address of 192.168.47.77 is no longer able to communicate with any network resources including the victim’s IP address. Please keep in mind that in a real-world scenario traffic within the L2 segment not passing the firewall is not blocked.
Figure 9 – Unsuccessful ping attempt to reach the victim
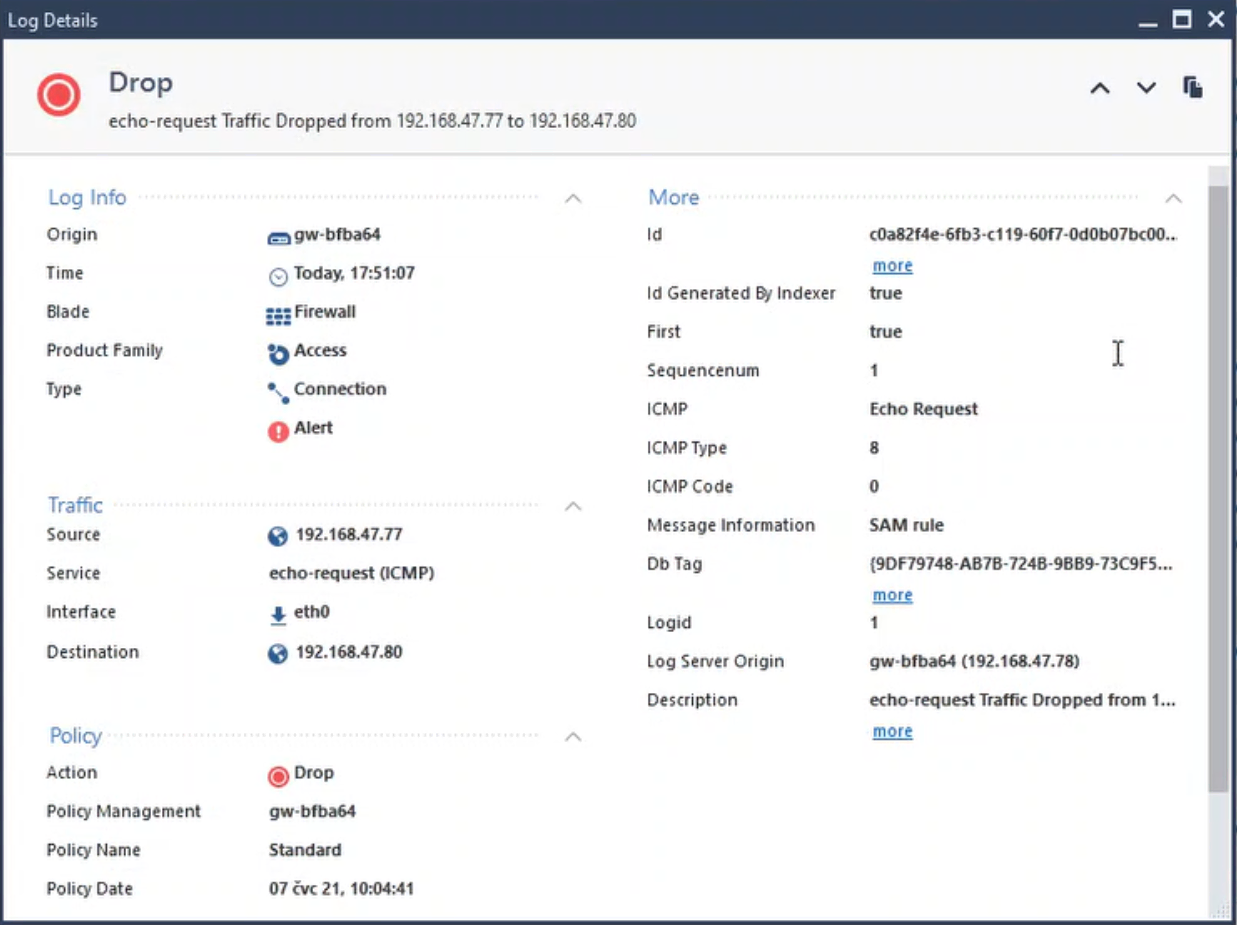
The isolated IP address is quarantined to prevent it from reaching other network segments or the Internet and can’t carry out any other malicious activity at all. Check Point Smart Console recognizes the subsequential ping attempt in the logs.
Figure 10 – Log details dialog in Check Point Smart Console
Network and end-point security
The integration of Flowmon and Check Point now forms an automated incident detection and response system that helps to protect your resources from both external and internal threats.
Both types of security solutions working together allow IT administrators to hold the attacker in the quarantine for a fully configurable length of time, giving them plenty of time to investigate the incident further.
If you have any questions, let us know.