Network detection tools utilize one of two prominent approaches for threat detection: AI-driven behavior-based methods capable of identifying early indicators of compromise, and signature-based ones, which flag known attacks and common CVEs. While these systems operate on distinct principles, their combination forms more robust defense mechanism, helps to consolidate tools, provides richer threat context and improves compliance. Signature-based techniques, employed in Intrusion Detection Systems (IDS), operate on the principle of identifying known attacks by comparing incoming packet data against a database of established attack signatures. While IDS is effective in detecting well-known attacks, it does depend on the availability and quality of the signature database.
Flowmon Anomaly Detection System harnesses the capabilities of AI to function as a behavior-based detection engine, primarily focusing on identifying deviations from learned baselines of normal behavior. This approach excels in detecting zero-day vulnerabilities for which the signature does not exist yet and unveils unusual behavior and anomalies in network traffic. Flowmon also doesn’t need network connectivity to download new signatures, making it a great choice for closed environments.
To maximize the synergy between both detection approaches, we integrated the IDS tool Suricata into Flowmon in 2020. We consistently expand Flowmon’s capabilities to consume, correlate and visualize alerts generated by Suricata. This combined approach brings several benefits such as:
- Enhanced Defense: Combining behavior-based and signature-based detections creates a more potent defense. It covers a broader range of threats, catching both known and emerging ones for a stronger security posture.
- Tool Efficiency: Integration reduces the need for multiple tools, simplifying management and lowering costs.
- Deeper Insight: This fusion provides a comprehensive threat perspective, offering specifics about known threats and context on unusual activities.
- Reliable Alerts: Cross-verifying alerts improves detection accuracy, reducing false positives and enhancing response confidence.
- Compliance Assurance: Integrating both methods aligns with industry regulations, demonstrating a commitment to comprehensive security.
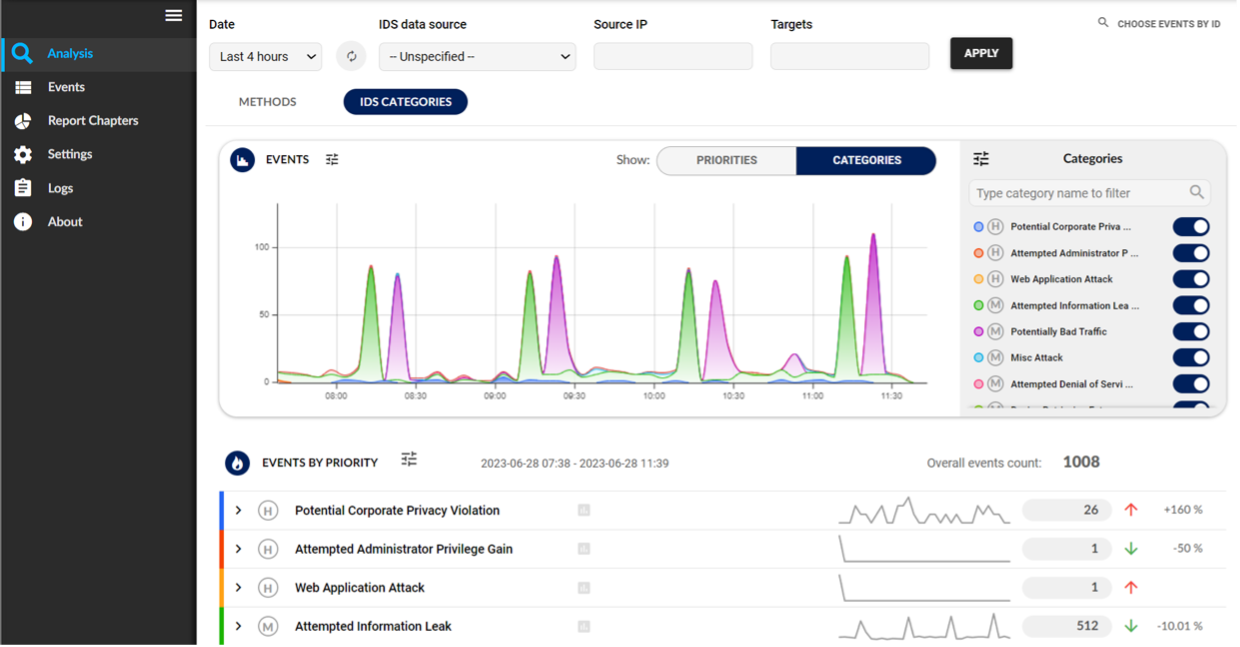
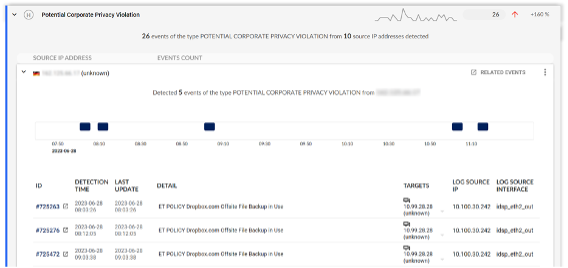
Flowmon intertwined Suricata on multiple levels. Dashboards and reports contain crucial information from both systems to increase your security awareness to help quickly prioritise and focus on the most critical events. Suricata events are now integrated into the regular analysis workflows and drilldowns to equalize the incident investigation experience. ADS correlates events from both systems to help reduce noise, cross-validate alerts and provide additional insights such as CVE descriptions.
In summary, combining behavior-based and signature-based detection methods in NDR tools is a crucial move to strengthen your cybersecurity. This bundle provides a strong defense against various threats, streamlines security, gives essential insights, improves alert accuracy, and ensures compliance with regulations. Embracing this approach not only secures your network but also prepares it for the evolving threat landscape.
IDS Suricata is a complimentary module available for Flowmon ADS. It requires simple installation with no configuration. You can find out more on how to enable IDS Suricata on Flowmon in this article.
