On the digital battleground, it pays to stay on your toes, but there are ways to make the work easier. Flowmon ADS 11.2 brings you new and refined methods of avoiding known threats and learning from attacks carried out against others.
Main news:
JA3 blacklists
MISP threat intel integration
Encrypted threat blacklisting
It’s common practice that applications use encryption to secure communication, but it’s also known that some malware uses it for cover. Luckily, there is a quick way to spot this – JA3 fingerprints.
A JA3 fingerprint is a kind of stamp unique to every application created while an encrypted session is being established.
So, what is the news?
On top of being able to generate JA3 fingerprints, ADS 11.2 can use JA3 blacklists and the fingerprints of known malware to detect harmful or otherwise unwanted applications.
This means you don’t have to manually copy fingerprints out of flows and compare them with databases. The system does all this automatically.
Figure 1 An event detail showing a JA3 as the method of detection
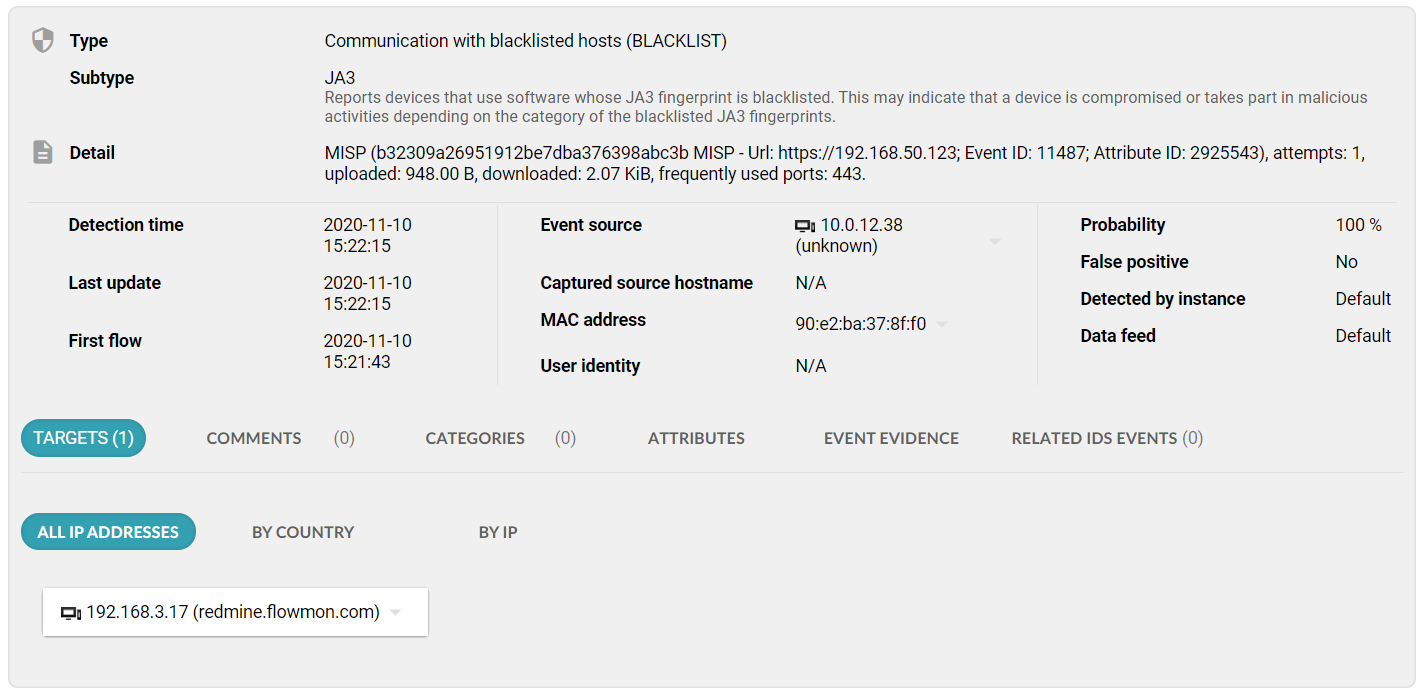
By uploading blacklists you will make the system better suited for your particular circumstances; for instance, to detect known malware or pick up disallowed applications in your network.
We’ve prepared a starter blacklist for you to add and use right away.
The reason we chose to provide a file instead of an out-of-the-box blacklist is that this method has a limitation in that the JA3 fingerprints of legitimate and malicious applications may sometimes be the same.
This means that there is a certain risk of false positives where legitimate apps get detected as unwanted. You would not be able to edit an internal blacklist and thus have no means of eliminating the false positives. But with an external file, you can.
Threat intel integration
Experience is wisdom and wisdom should be shared. Platforms like MISP enable organizations to share Indicators of Compromise and thus collectively improve the community’s security posture.What can Flowmon offer here?
If you are one of the 6,000 participants of MISP, you can integrate the intelligence feed into your Flowmon ADS (if you are not, all you need to do is start an instance). It will pull the MISP data to automatically create IoC blacklists for you to detect and identify malicious communications, providing an immediate identification of what kind of attack you might be under.
Figure 2 A setup dialog for the configuration of the MISP threat intelligence feed
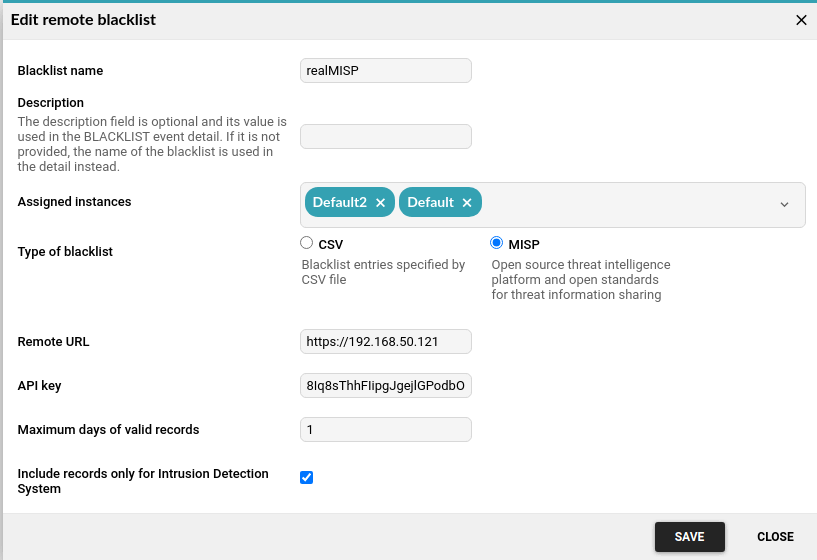
If an event is detected, the detail shows you whether it was based on MISP and includes a reference to the MISP event ID.
There is a world of difference between detecting an event in ADS and knowing what kind of breach it belongs to and having to discover that for yourself.
Figure 3 An event detail showing MISP blacklist as the method of detection
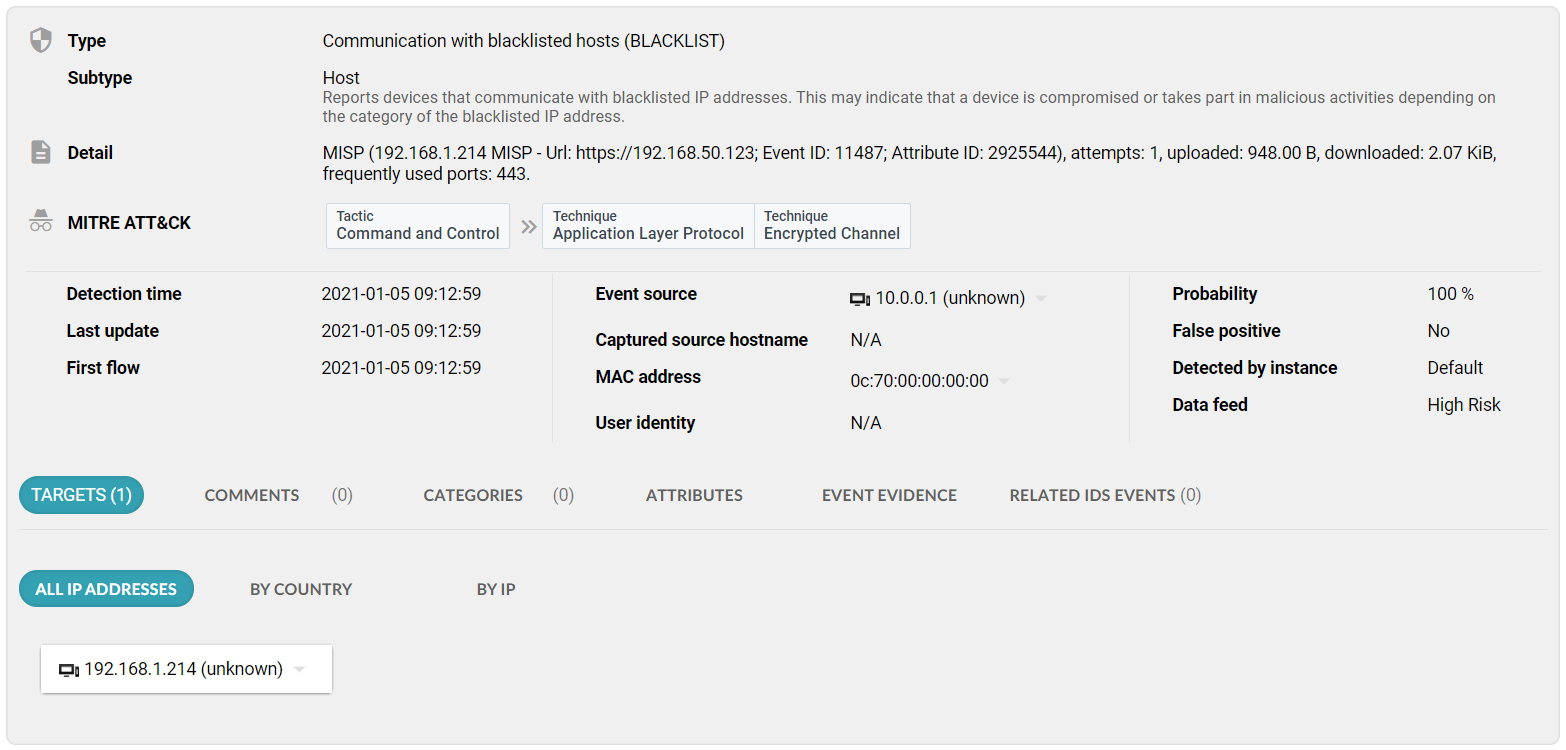
This is also a quick way to check if you haven’t fallen victim to an attack that has recently surged (does the word SUNBURST ring a bell?).
The feature includes all the supported blacklist data formats present in Flowmon ADS (IP address, web or domain, service, and newly also JA3 fingerprints).
Better visuals
Smooth detection deserves smooth visualization. ADS 11.2 departs from the angular style of graphs and assumes a smoother, more pleasant look.
Figure 4 New event chart design
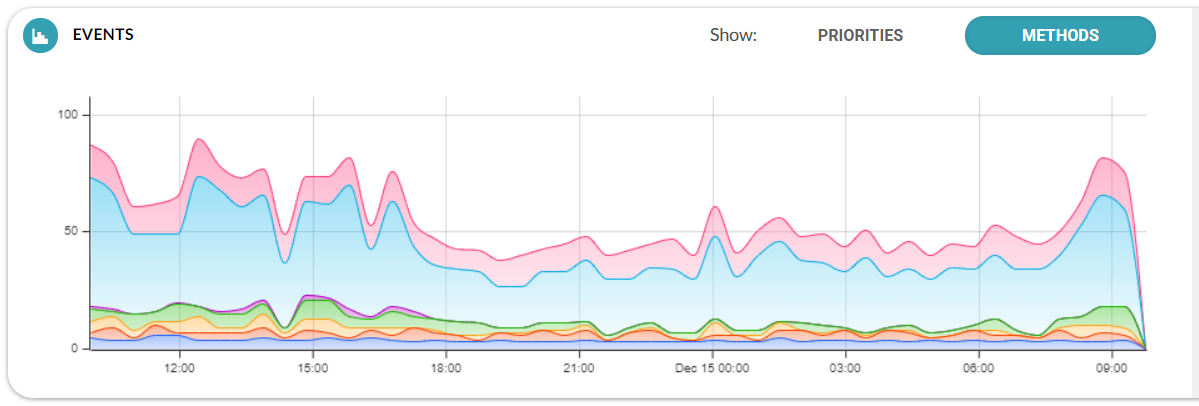
Automate the routine
Flowmon ADS 11.2 is a union of labor-saving automation and extensive threat intelligence designed to free the hands of any security admin.
Stay tuned for more exciting news on context-aware anomaly detection coming in the near future.
Do you have any feedback about Flowmon ADS 11.2? Let us know!