Accelerate Network Detection, Respond Quickly and Efficiently
AI-Powered Cybersecurity Solution of Choice
Progress® Flowmon® Network Detection and Response (NDR) is the first line of defense, integrating AI and Intrusion Detection Systems (IDS) to reduce noise, automatically prioritize tasks and helps you minimize data breaches.
Enterprises you trust use Flowmon





Detect ransomware, expose insider threats, respond immediately
- Real-time network behavior analysis and enterprise-grade anomaly detection system
- 40+ detection methods and 200+ algorithms to detect data breaches at any stage
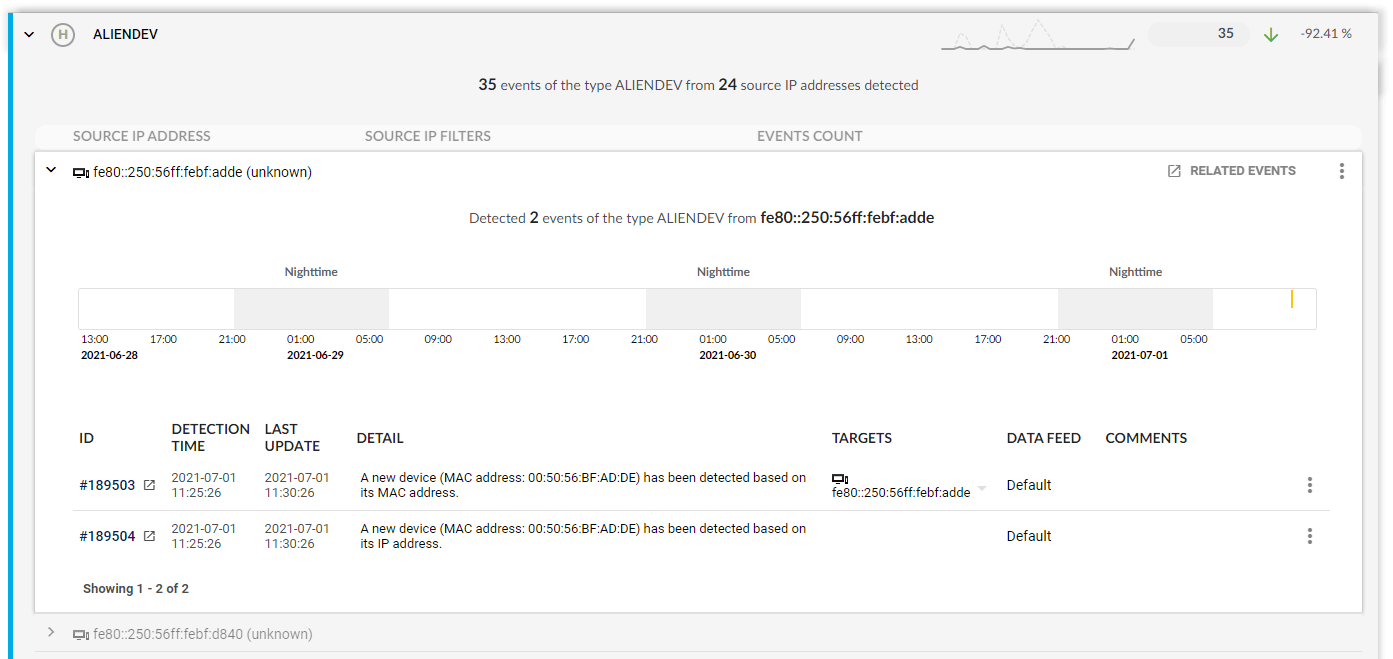
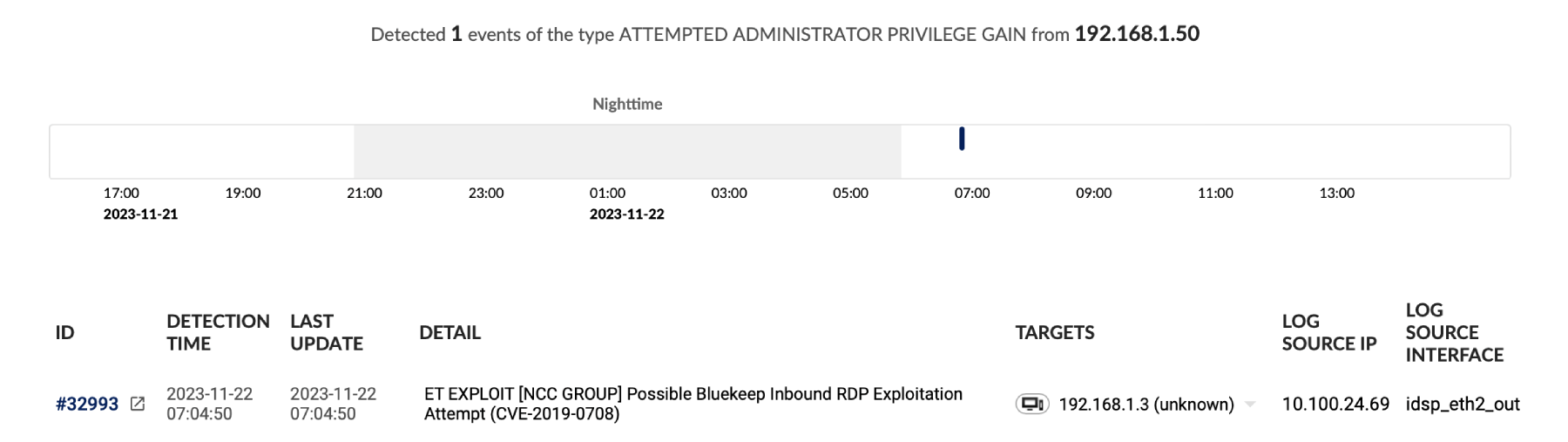
- Detection of rogues, insider threats, zero-day exploits, ransomware, and targeted attacks
- Reinforce your security matrix via integration with log management, SIEM, SDN, incident response, etc.
- Comprehensive visibility across on-premise, hybrid, and cloud environment at scale
- Combining AI capable of tracking unknown threats with signature-based intrusion detection and threat intelligence for known attackers and malware
See live product demo
Explore a fully interactive product of Flowmon and see what issues it can tackle.
Technical features
Ransomware detection
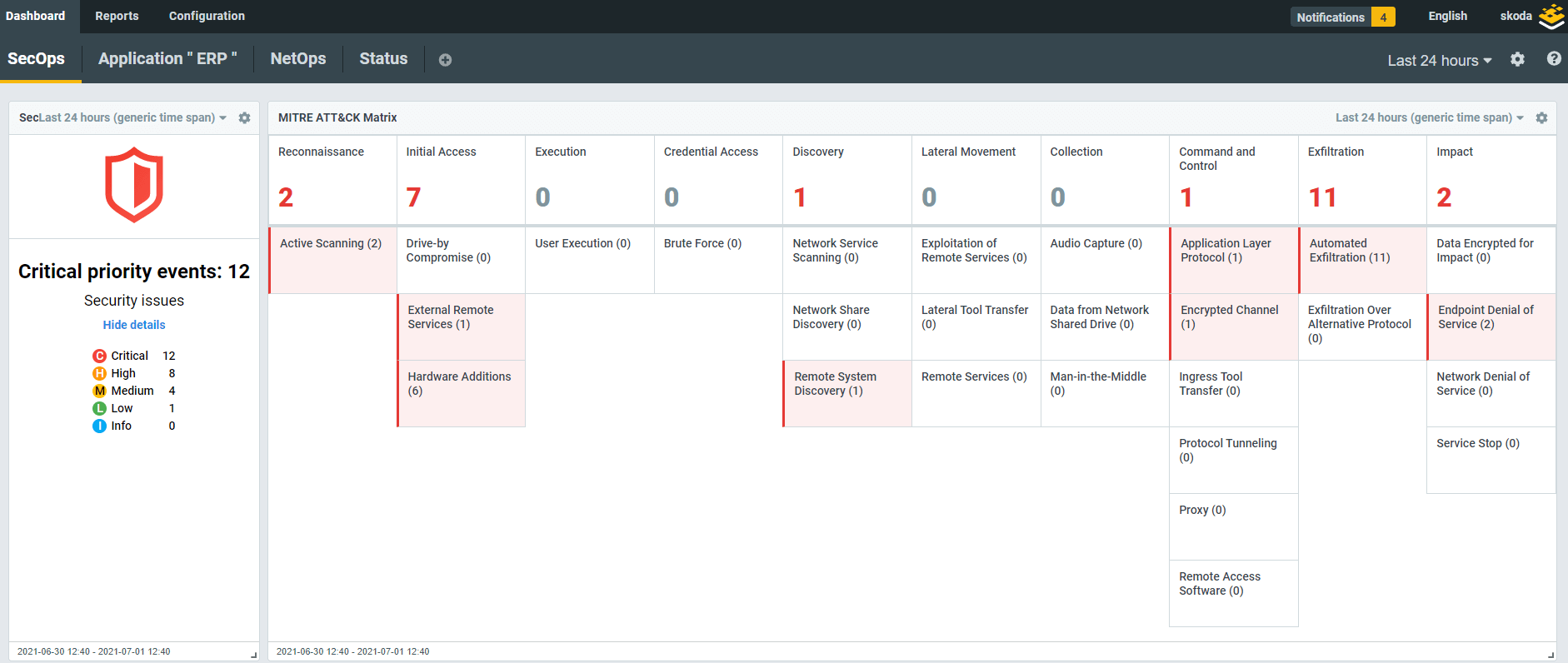
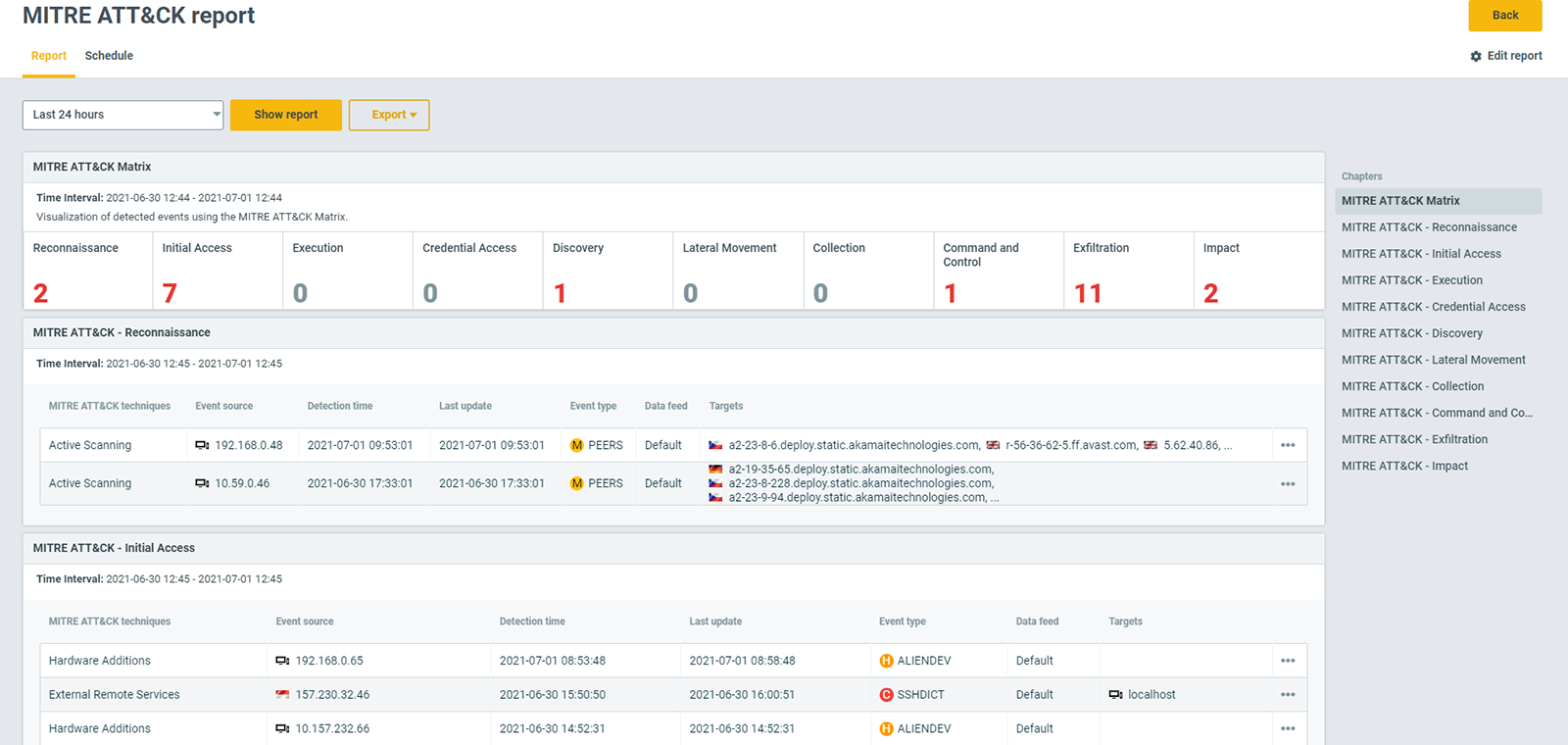
Flowmon picks up signs of malicious activity in the network and informs you about the adversary’s every step. Each detected event corresponds to a MITRE ATT&CK® tactic or technique to give you an unambiguous awareness of the attack severity, scope, and future development.
Reduce attack surface
A diversity of techniques covers more scenarios. The solution leverages over 40 methods and 200+ algorithms including machine learning, behavior analysis, community threat intelligence, IoCs, or reputation databases with automated packet analysis available on-demand. All these techniques are employed simultaneously, to bring the most reliable network-centric threat detection in on-premise, edge, or cloud environments, encrypted or not.
Eliminate blind spots
Tackling zero-day threats requires a pluralist approach, like the SOC Visibility Triad, where each solution makes up for the downsides of the others. Flowmon constitutes the network pillar of the triad by its ability to detect malware activities in their infancy and streamline threat detection and response.
Zero noise
You do not have to slog through scores of false positives; the solution’s AI-powered engine will distinguish between an anomaly and normal traffic and only alert you when a real danger occurs. Detected security events are ranked by severity and provide built-in expertise to enhance your situational awareness and speed up triage and response.
Integrated Intrusion Detection
Integrating signature-based IDS into our platform extends its reach beyond external threats, while enhancing network-wide security and insider threat detection. This synergy supports response targeting, which reduces disruptions to unaffected systems and users. As a result, Flowmon helps balance operational efficiency, while aiding security efforts.
Integrated NDR and IDS: Beyond Traditional Perimeter Defense
Traditionally, IDS focus on perimeter defenses and external threats. Our integrated NDR and IDS solution extends this protection to encompass the entire network, including east-west traffic and cloud environments. This approach not only enhances the detection of known malware, CVEs and compliance monitoring across network traffic but also helps address insider threats and amplify security coverage.
| Flowmon NDR + IDS engine | Traditional IDS | |
|---|---|---|
| Typical deployment | Network-wide | Yes |
| Signature-based detection of known threats | Yes | Yes |
| External attacks | Yes | No |
| Insider threats | Yes | No |
| East-west coverage | Yes | No |
| AI detection of unknown threats | Yes | No |
| Threat intelligence | Yes | No |
| Cloud support | Yes | No |
Off-the-shelf integration
Integrate the solution with other tools and get the most out of your security matrix. You may use the system to trigger automatic selective blocking with an inline solution or feed the detected events into a SIEM and greatly improve its analytical capability by feeding it noiseless inputs from the network.












Expose unknown threats before they become a problem
Flowmon tackles anomalies that traditional solutions miss.
Attack evidence and analysis
Understand every suspicious event in its complexity and take decisive action without delay.
Automated attack recording
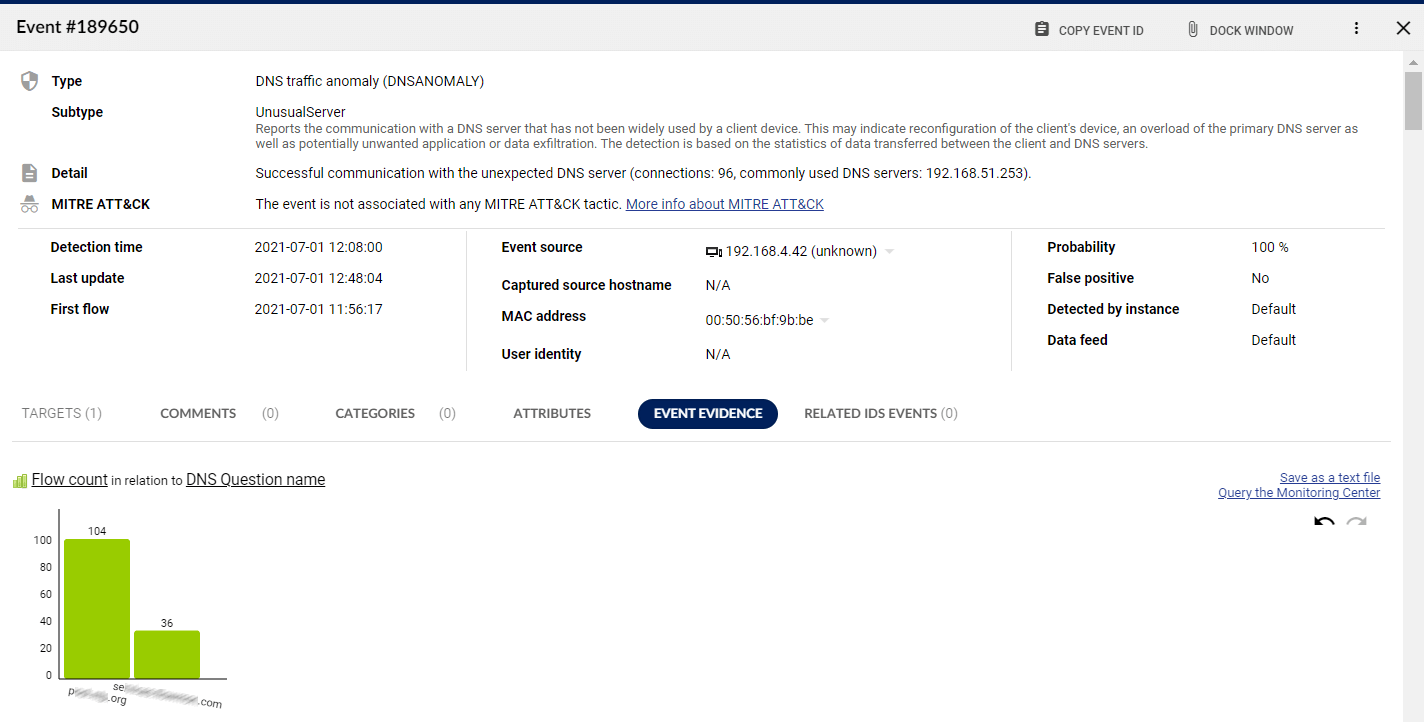
Trigger full packet capture upon event detection. The rolling memory buffer ensures no data is lost.
Seamless SIEM integration
Report detected events via integration with SIEM systems, surveillance, and incident handling systems.
Custom methods
Create your own custom methods and red-flag malicious or unwanted traffic specific to your environment or policies.
AI-based detection
Leverage a state-of-the-art detection engine that uses entropy modeling and machine learning to detect suspicious anomalies in your network traffic.
Threat intelligence
Enhance your detection capabilities with a combination of commercial and community threat intelligence feeds and stay briefed on the latest indicators of compromise.

Security and flow data resource library
Why not check out these resources to help you get started with a flow based security solution for your environment.

"After three months of intensive testing we were able to prove that Flowmon was the right product due to its performance, anomaly detection capabilities, scalability in GÉANT and its simplicity when managing and configuring."
Head of Information & Infrastructure Security
Ready to get started?
Try out an interactive demo and experience the capabilities of the most scalable NDR solution on the market.
Start demo now