We can observe a trend of rising popularity of DoS/DDoS attacks in all reports of major players on the security market. Ponemon Institute study (Cyber Security on the Offense:A Study of IT Security Experts) estimates that an average cost of a single minute of downtime is $22.000 when an average downtime is 54 minutes. According to Q3/2015 State of the Internet – Security Report, Infrastructure layer DDoS attacks increased by 30% from previous quarter and were up to 198% over Q3/2014 while characteristics including duration, volume and peak bandwidth of such attacks have dropped down.
Flowmon DDoS Defender is an extension of Flowmon solution representing a noninvasive DDoS attack detection system for high-speed networks based on NetFlow monitoring and network traffic analysis.
A combination of static rules and percentage deviation from adaptive thresholds is applied on protected segment, which is typically defined by an IP address range, port&protocol defined services, VLAN numbers or MPLS tags. Different rules for different protected segments could be configured for attack detection.
Figure: Attack detail overview
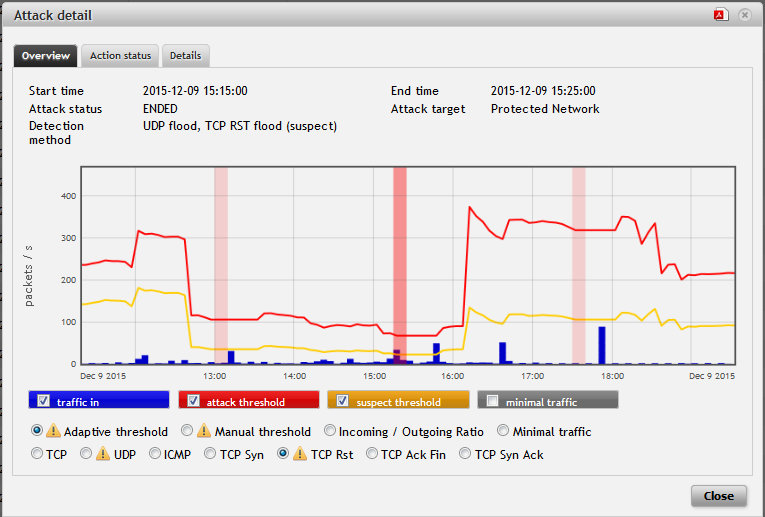
For all detected DDoS attacks, Flowmon shows information about the normal traffic volumes, attack size, timestamps, current state of the attack and advanced attack characteristics, including relevant TopN statistics.
Figure: Attack detail - Top 10 statistics
Integration with mitigation tools
Thanks to robust and versatile architecture, DDoS Defender is deployable as standalone solution as well as in conjunction with mitigation services provided by Scrubbing centers. The integration with network components is supported via PBR (Policy Based Routing), BGP (Border Gateway Protocol) or RTBH (Remotely Triggered Black Hole) mechanism as a simple method of attack mitigation. Initiation of a pre-defined script enables a reaction to the attacks in an environment, which usage of standard methods of routing traffic diversion or attack notification does not provide.
Once the attack is detected using on-premise flow data monitoring of network traffic, it needs to be diverted to a specific out-of-band DDoS mitigation appliance referred as Scrubbing centre. That enables legitimate traffic to pass through freely while the actual attack is being scrubbed. This procedure provides complex attack detection and mitigation focused on volumetric attacks. Compared to in-line deployment of attack mitigation appliances this approach provides higher scalability and significant cost efficiency especially for large networks with multiple peering partners and bandwidth of tens of gigabits per second.
Flowmon DDoS Defender provides necessary data for traffic diversion and subsequent mitigation when the attack is being detected. This general concept proved great results e.g. with Radware products as well as national-level based approach.
As an example of effective on-premise DDoS detection with external scrubbing is use-case from Netherlands. NaWas initiative (abbreviation for "Nationale Wasstraat" which is National Washing Facility in Dutch), a collective effort to handle large scale internet attacks. Several ISPs - customers of Flowmon Networks – use Flowmon DDoS Defender for prompt attack detection and traffic diversion into NaWas, which ensures mitigation part of the process.
If you are interested in details of integration with Radware products, check out our Whitepaper “DDoS protection for high-speed networks” published by Radware and Flowmon Networks. DDoS Defender together with Radware DefensePro appliance and Vision management appliance represent DDoS protection ecosystem designed to protect even the largest infrastructures and internet backbones. Native integration of DDoS Defender with Vision via RESTful API enables to manage multiple DefensePro appliances via standard management interface and dynamically configure network protection profiles while providing DefensePro details with about the attack and baselines of standard network traffic.
Figure: PDF report of attack
According to results of lab tests at CD-Telematika, the process of DDoS attack mitigation by Flowmon DDoS Defender and Radware solutions, takes from 3 to 10 minutes. As a matter of fact, development team is working on refining the granularity of flow statistics to 1 min batches, which will shorten the whole mitigation process to only 1-3 minutes. Increased granularity and manual thresholds complemented by dynamic baselines will reveal even DDoS attacks made to evade traditional detection approaches.
No experience with Flowmon DDoS Defender yet? Visit Flowmon Online Demo and stay in touch for further information on our products!