When any file is encrypted on your computer or server, you can simply start looking for your backups and go ahead with recovery from tapes because there is no other remedial procedure available. It does not make any sense to contact blackmailer or pay bitcoins as it is technically impossible for the attacker to decrypt your data. Reason? Installation ID does't contain information necessary for key recovery hence extraction of the decryption key using their private key is impossible.
The internet community has figured some patterns of Petya's behavior. It's mainly communication of the compromised device to the following set of IP addresses 95.141.115.108, 185.165.29.78, 84.200.16.242, and 111.90.139.247 - making it easy to detect an infected station on network level.
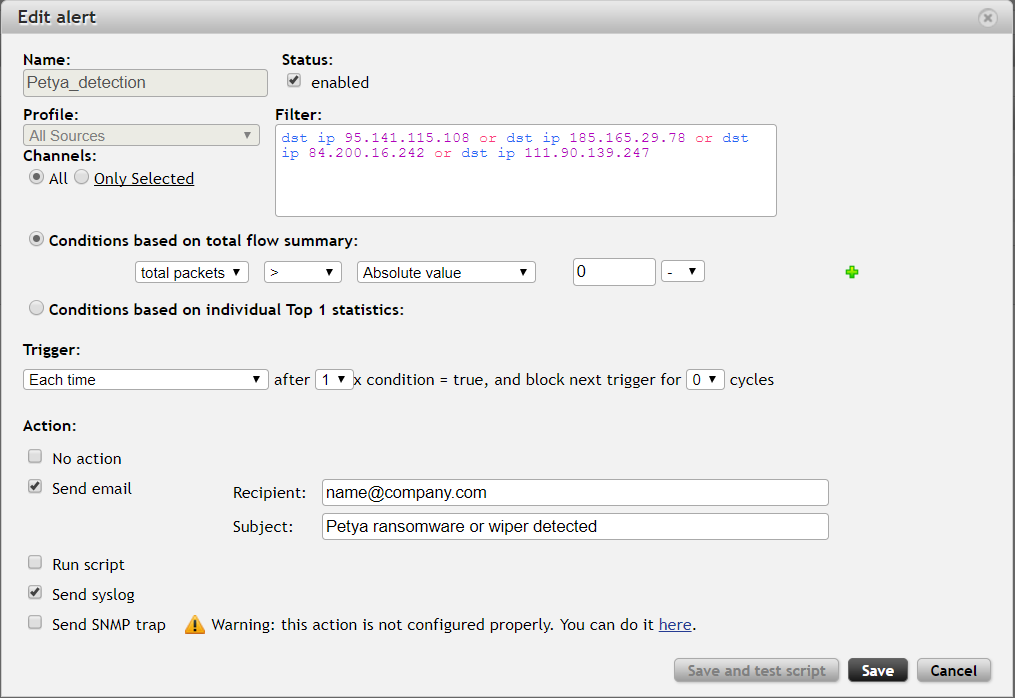
The first option is alerting in FMC where you can easily set up a new alert for Petya IP addresses.
Use following filter: dst ip 95.141.115.108 or dst ip 185.165.29.78 or dst ip 84.200.16.242 or dst ip 111.90.139.247
Another option is to use Custom behavior pattern definition in Flowmon ADS.
Set up custom behavior pattern as follows: destination_ip_address =
Tools.ip_to_int('95.141.115.108') OR destination_ip_address =
Tools.ip_to_int('185.165.29.78') OR destination_ip_address =
Tools.ip_to_int('84.200.16.242') OR destination_ip_address =
Tools.ip_to_int('111.90.139.247')
The recommended next step is to make sure you data is backed up for possible recovery of your critical infrastructure on tapes.
This article is also available as a video tutorial on our YouTube channel.
Using custom behavior patterns allows to detect various operational issues and security anomalies. To see how this applies to WannaCry ransomware see this previous blog post.